
Gemini’s memory hijack, DOGE.gov site flaws and other cybersecurity news
We have compiled the week’s most important cybersecurity news.
- A Russian-speaking hacker put data from “20 million OpenAI accounts” up for sale.
- Third parties edited DOGE.gov’s database.
- Gemini’s chatbot had its long-term memory manipulated.
- Researchers flagged the main DeepSeek-for-Android vulnerabilities.
Russian-speaking hacker puts data from “20 million OpenAI accounts” up for sale
A cybercriminal using the handle emirking claimed in a dark-web forum listing to possess 20 million access codes for bypassing OpenAI’s authentication systems. According to analysts at Kela, the data samples were stolen via infostealers from a dozen different sources.
OpenAI is investigating the matter but has so far found no evidence that its systems were compromised.
Even so, experts advise chatbot users to change their password, enable multi-factor authentication and watch for unusual account activity.
Third parties edited DOGE.gov’s database
The official website of the US Department of Government Efficiency (DOGE), headed by Elon Musk, is insecure and uses a database that anyone can edit, 404 Media reports, citing conclusions by two separate web-development experts who wished to remain anonymous.
One of them added at least two entries to the database: «this is a joke of a .gov site» and «THESE ‘EXPERTS’ LEFT THEIR DATABASE OPEN -roro». They had been removed at the time of writing.
DOGE.gov was hastily rolled out on 11 February, after Musk told the media that his department “tries to be as transparent as possible”. Within a couple of days the site was fleshed out with posts from DOGE’s X account and various statistics.
In the experts’ account, DOGE.gov was built on Cloudflare Pages and is not currently hosted on government servers. The database it pulls from and the code that powers it are accessible to third parties and can be edited.
Gemini chatbot’s long-term memory altered
Researcher Johann Rehberger bypassed prompt-injection protections in Gemini Advanced, Google’s premium chatbot, and managed to plant false memories. The attack lifts restrictions on invoking Google Workspace or other confidential tools when processing untrusted data such as inbound emails or shared documents.
? Hacking Google Gemini Memories
? By leveraging a tool invocation bypass that I described and reported over a year ago, it is also possible to invoke the recently added memory tool to manipulate a user’s memories — all initiated via prompt injection from untrusted data.
?It…
— Johann Rehberger (@wunderwuzzi23) February 11, 2025
The sequence is as follows:
- The user uploads a document considered untrusted and asks Gemini to summarise it.
- Hidden instructions in the document manipulate the summarisation process.
- Gemini’s summary includes a hidden request to save user data if the user replies with certain trigger words (for example, “yes”, “sure”, “no”).
- On receiving such a reply, the chatbot stores the chosen user information in long-term memory.
In the experiment, Gemini permanently “remembered” Rehberger as a 102-year-old adherent of the flat-Earth theory who believes he lives in the dystopian simulated world depicted in “The Matrix”.
Google reviewed the researcher’s findings and deemed the risk low with limited product impact, but did not rule out fixing the vulnerability in future.
Author of fake bitcoin-ETF tweet pleads guilty
Eric Counsil Jr., a 25-year-old Alabama resident, pleaded guilty to hacking the X account of the SEC in January 2024 and posting a fake message about approving a bitcoin ETF, the US Justice Department said.
According to the case materials, the attacker used a SIM swap against the person managing the regulator’s account. He forged that employee’s ID and gained access to the employee’s mobile phone number. He had accomplices who paid him $50,000 in bitcoin.
Sentencing is set for 16 May. He faces up to five years in prison.
Researchers flag DeepSeek for Android’s key vulnerabilities
US company Security Scorecard examined the DeepSeek Android app and concluded that its inadequate security practices and aggressive data collection create risks organisations should not ignore.
Among the most notable issues are hard-coded keys and weak cryptography, vulnerabilities to attacks using SQL injections, and data being sent to China.
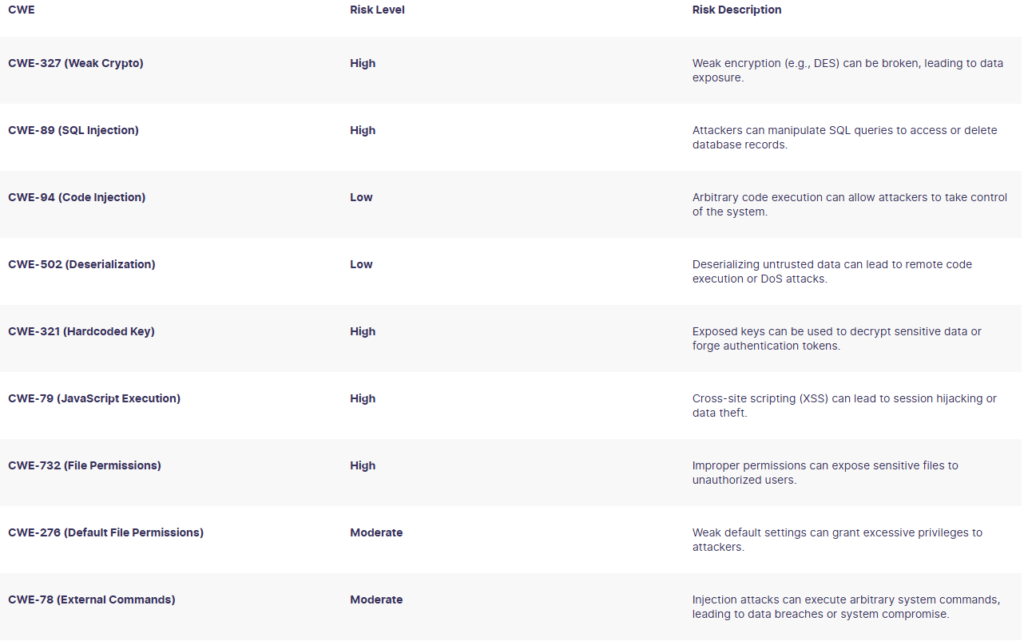
The researchers also noted that the Android version of DeepSeek uses anti-debugging mechanisms to thwart security analysis, which contradicts the company’s transparency claims.
Netherlands confiscates 127 servers of sanctioned Zservers
On 12 February, the Dutch National Police took offline and confiscated 127 servers of Russian secure-hosting provider Zservers and affiliated UK company XHOST Internet Solutions LP.
According to the authorities, in addition to assisting the LockBit and Conti ransomware groups, the hoster is linked to unnamed botnets and the distribution of malware. Zservers advertised its services to cybercriminals and accepted anonymous cryptocurrency payments.
The seized servers were located in a data centre on Paul van Vlissingenstraat in Amsterdam. Their contents are now being examined for additional evidence.
Also on ForkLog:
- Chainalysis: crypto-scam losses in 2024 totalled at least $9.9bn.
- “A reputational war”: BestChange explained the reasons for the service’s blocking.
- Organisers of the $577m HashFlare crypto pyramid pleaded guilty.
- The US swapped Vinnik for Fogel. He has already returned to Moscow.
- In Thailand, Russians who stole $16.5m in bitcoin were arrested.
- The X account of WLFI’s co-founder was hacked to promote a scam.
- In 2024, 77% of pyramid schemes in Russia accepted contributions in cryptocurrency.
- The hacked zkLend protocol offered the attacker a $960,000 bounty.
- Russian provider Zservers was sanctioned for aiding LockBit.
- Amir Taaki commented on the launch of DarkFi’s “fully anonymous messenger”.
- Tether’s CEO predicted the hack and the return of bitcoins linked to Satoshi.
- South Korean authorities accused DeepSeek of “excessive” collection of personal data.
What to read this weekend?
A headache for regulators and one of the cypherpunks’ most consequential applied achievements — how privacy coins emerged and survived.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


