
An Ethereum-stealing cheat, smishing at Binance, and other cybersecurity news
Here are the week’s most significant cybersecurity developments.
- Bitcoin-wallet owners lured by game cheats.
- Binance warns of smishing texts and Trojanised apps.
- Coding-focused AI models face a new attack class.
Bitcoin-wallet owners lured by game cheats
Criminals are placing links in YouTube descriptions under videos advertising game cheats that download an archive whose contents install the Arcane infostealer, according to researchers at Kaspersky Lab.
? Think twice before downloading that “free cheat.”
Cybercriminals are now using ArcanaLoader—a sneaky downloader that claims to install cheats, cracks, and other “useful” gaming tools, but which actually infects devices with the Arcane stealer ?
Full story:… pic.twitter.com/7sZ4Ht0pQQ
— Kaspersky (@kaspersky) March 21, 2025
Among other things, the malware targets crypto wallets including Armory, Jaxx, Exodus, Electrum, Atomic Wallet, Guarda and Coinomi. It also exfiltrates system information and user data from browsers, VPN clients, networking tools, messengers, email and gaming services.
Most infections so far are in Russia, Belarus and Kazakhstan.
Binance warns of smishing and Trojan apps
The cryptocurrency exchange Binance warned users about a new wave of smishing—fraudulent SMS messages sent in the name of the platform’s administrators.
Attackers send a bogus alert about suspicious account activity, then, under various pretexts, try to get the user to contact them and move funds to a “safe” wallet.
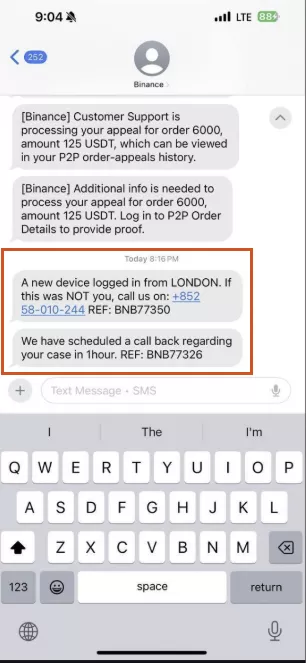
The exchange reiterated that it never asks users to make calls or compels them to move assets.
Binance also warned about Trojans disguised as legitimate software. Recently, crypto holders were hit by the Bom app, which masqueraded as a mining tool.
After installation it requested access to local files and scanned them for private keys or seed phrases. The campaign led to more than $650,000 being stolen across several blockchains.
AI coding models hit by a new attack vector
Researchers at Pillar Security found a new attack vector against GitHub Copilot and Cursor that compromises the code they generate.
The rise of #VibeCoding together with developers’ inherent “automation bias” creates the perfect attack surface. We discovered a New Rules File Backdoor attack, that allows hackers to poison AI-powered tools like #GitHub Copilot & #Cursor , and inject hidden malicious code into…
— Pillar Security (@Pillar_sec) March 21, 2025
Malicious instructions are planted in tool configuration files using invisible Unicode characters. As a result, the models start producing backdoored and otherwise vulnerable code that slips past standard checks.
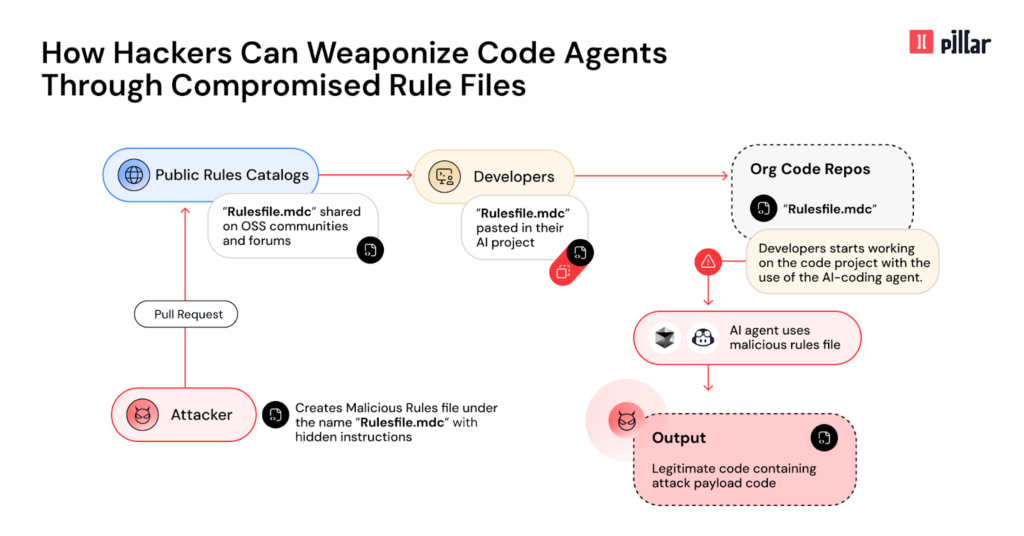
Following the disclosure, GitHub and Cursor said users are responsible for reviewing code proposed by their AI models.
WhatsApp patches zero-day used in Paragon attacks
WhatsApp representatives told Bleeping Computer the company fixed a zero-day vulnerability that was used to install Paragon’s Graphite spyware.
The fix was shipped at the end of 2024 and did not require additional client-side action.
The service contacted potential victims directly, including journalists and members of civil society.
A major RuNet outage linked to Cloudflare blocking
On March 20th, some Russian users experienced problems accessing popular sites and services, including YouTube, Twitch and TikTok. Complaints were logged by Сбой.рф and Downdetector.
According to their data, customers of several Russian ISPs were affected. In some regions, mobile operators also suffered outages.
In comments to RBC, Roskomnadzor said the disruptions were related to “the use of foreign server infrastructure, where technical failures were recorded.” The watchdog recommended Russian firms move to local hosting platforms.
Meanwhile, participants of the ntc.party technical forum reported the unavailability of the US CDN service Cloudflare. They argued that the fact not all ISPs were affected points to a Roskomnadzor block rather than a server-side failure.
Britain sets a timeline for post-quantum cryptography
The UK’s National Cyber Security Centre (NCSC) urged critical organisations to implement post-quantum cryptography (PQC) by 2035.
The guidance primarily addresses government agencies, large enterprises, operators of critical national infrastructure, and technology and software vendors with bespoke IT systems. All must ensure full migration of their systems, services and products by the deadline.
NCSC listed the risks of falling behind the proposed roadmap.
The United States set a similar PQC migration schedule in National Security Memorandum No. 10.
Also on ForkLog:
- RWA protocol Zoth suffered an $8.4 million exploit.
- Ben Zhou: most of the funds stolen from Bybit can be traced.
- Experts warned about infected software in TradingView Premium.
- Gotbit’s CEO pleaded guilty to fraud and agreed to pay $23 million.
- Crypto address “poisoning” netted hackers $1.2 million in three weeks.
- Media: prosecutors sought 10 years in prison for the attacker of Haru Invest’s CEO.
- The US withdrew claims against the creator of the BitClout social network.
- Hackers began laundering crypto while posing as novice traders.
- Microsoft warned of a Trojan targeting crypto wallets.
- Wallet explained its approach to blocking user wallets.
- Wemix explained the delay in disclosing the $6.2 million hack.
- Bitcoin held by North Korean hackers surpassed the reserves of El Salvador and Bhutan.
- Users reported phishing emails impersonating Coinbase and Gemini.
- Reporters learned of restrictions on DeepSeek employees in China.
- Jameson Lopp proposed burning quantum-vulnerable bitcoins.
- OKX suspended its DEX aggregator due to hacker activity.
- Hackers posted fake warnings on behalf of Kaito.
What to read this weekend?
With Vladimir Menaskop, we examine the importance of consensus and its role in preventing hacks.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


