How to safeguard privacy and security in Bitcoin mining
In the early days of Bitcoin mining, it was truly open and accessible. Anyone could simply download free software onto their computer and start earning.
However such a low barrier to entry did not last long. By the end of 2010, mining with a CPU lost competitiveness due to the appearance of GPU. This trend led to the creation of Slush Pool in November of the same year, which allowed CPU miners to earn a stable income again.
When ASIC devices entered the market in 2013-2014, they quickly revolutionised the industry. The demand for specialised mining hardware sharply raised the entry barrier, and it remains high to this day. However, not all was lost.
At least, if you were able to obtain several SHA-256 ASICs and affordable electricity, nothing prevented you from mining. Unfortunately, nowadays even this right may not belong to everyone.
As governments and regulators study Bitcoin, their attempts to regulate or even directly control mining seem inevitable.
What can be done to keep mining as accessible as possible? Slush Pool explains.
Network security
Would you like your internet provider to know everything you do online? Probably not. One of the ways internet users have partially restored privacy in recent years is by moving from HTTP to HTTPS. The latter has already become the standard for all websites.
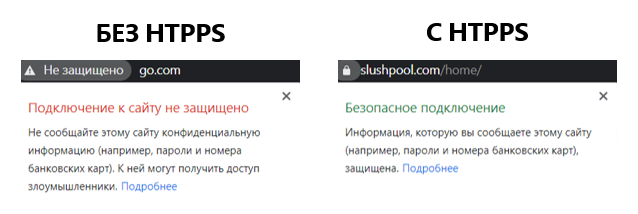
The ‘S’ in HTTPS stands for ‘Secure’ — an abbreviation of Secure Sockets Layer (SSL) — the Secure Sockets Layer. In essence, this means your internet service provider knows which websites you visit, but not what you do on them.
On websites without SSL certificates your internet provider can track all your activity, including usernames, passwords and even payment details. Obviously, HTTPS is a more acceptable protocol for users.
Most Bitcoin miners still use the mining equivalent of HTTP — Stratum V1. Miners and mining pools constantly exchange data in JSON format (a human-readable format), and, if no additional precautions are taken, internet providers can see all the details of this data transfer.
In other words, ISPs, based on the data at their disposal, can easily see that someone is mining Bitcoin. Worse still, a malicious ISP employee could steal hashrate (and thus Bitcoins) without your knowledge. Even your neighbour could carry out a hashrate hijack attack if the ISP does not isolate clients from one another properly.
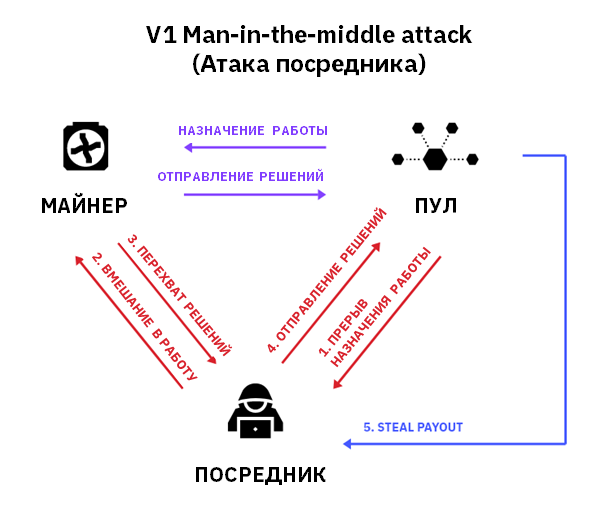
To prevent this, miners can use the industry equivalent of HTTPS: Stratum V2. While V1 data transfer is unencrypted and readable by humans, Stratum V2 uses authenticated encryption with associated data (AEAD) to ensure the privacy of data transmission between miners and pools.
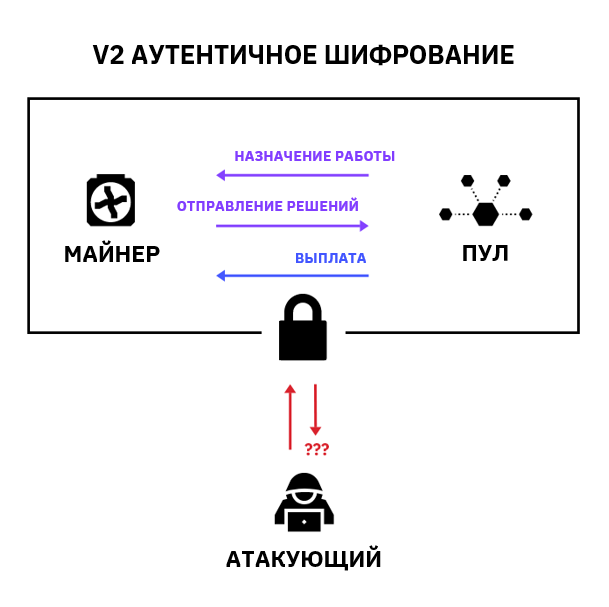
Switching from JSON to binary in Stratum V2 significantly reduces the size of transmitted data, so encrypted messages in V2 are about 50% lighter than unencrypted messages in V1. The miner’s data load will not increase after switching to V2.
Your internet service provider should not know that you mine Bitcoin. Using Stratum V2 helps avoid this. But this is only part of the solution.
Total privacy
Your internet service provider can still see which websites you visit. A great deal can be learned about a person even from the list of URLs.
For ordinary web browsing a VPN can be handy. A VPN masks your public IP address so your ISP does not know what you do on the internet and does not track your actions. Bitcoin miners can also use VPN services, but this introduces network latency, which can be quite costly in a business where every millisecond counts.
Bitcoin miners can achieve the same level of privacy with a DNS proxy without significantly increasing network latency.
This dnsscrypt-proxy provides a local service that can be used directly on a local resolver or as a DNS forwarder, encrypting and authenticating queries using the DNSCrypt protocol and passing them to an upstream server. The DNSCrypt protocol uses high-speed elliptic-curve cryptography with strong protection, which is similar to DNSCurve, but aimed at ensuring the security of the connection between the client and its first-level resolver.
Information that is usually open is also encrypted via a DNS proxy, which means your internet provider cannot determine which sites you visit.
Miners can use any DNS proxy that supports encrypted DNS protocols, such as DNSCrypt v2 and DNS-over-HTTPS, to achieve much greater privacy. In combination with Stratum V2 this is equivalent to browsing the web with a VPN and visiting only HTTPS domains.
Hiding your energy use — that’s another problem
If you are using only one or a few ASIC devices, the measures described will help you make mining private and secure. Large-scale mining, however, leaves a thermodynamic footprint that is hard to hide.
The best you can do with software is to ensure that no one, including your ISP, can eavesdrop on your mining or steal your hashrate.
Subscribe to ForkLog’s news on Telegram: ForkLog Feed — the full news feed, ForkLog — the most important news and polls.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


