How Bitcoin transactions are tracked


1
What do addresses on the Bitcoin network look like?
Bitcoin addresses are strings of Latin letters and digits. They do not contain their owners’ names, which can give users a false sense of full anonymity. However, transactions are recorded on the Bitcoin network without encryption, so they can be traced.
Much depends on how an address is used and what traces of activity it leaves. For instance, transactions to or from an address placed in its owner’s email signature or on forums are fairly easy to track.
If, by contrast, the address was created in a separate system accessed via the Tor anonymity network and received coins solely from a mining pool such as Eligius, which does not require registration, the task becomes far harder.
Even so, by deploying serious analytical tools and investing time and resources, one can get very close to the bitcoin holder.
2
What can any user track?
The simplest tools for tracing transactions are the many explorers of the Bitcoin blockchain. They are typically used to check that an operation has succeeded rather than sitting unconfirmed.
Anyone can play sleuth and, in a few clicks, pull up a given address’s past transactions, current balance, amounts moved, and lists of input and output addresses. Enter a transaction identifier (TXID, TxHash), address, hash or block height into a block explorer’s search bar to see status instantly.
Try starting with Block Explorer or Blockchain.com. Similar data, with different presentation, are also available from OXT, Token View, Blockcypher, Insight, Sochain and Blockstream Bitcoin Explorer. With Cryptocurrency Alerting you can set alerts for activity on an address of interest, while Blockseer will “follow the bitcoin”, visualising links among addresses that participated in transactions.
3
Can you hide from tracking?
Given Bitcoin’s pseudo-anonymous nature, anti-tracking measures offer only relative protection. Even CoinJoin, a popular technique that combines multiple users’ transfers into a single transaction with many outputs and does not require handing coins to a third-party service, does not guarantee full anonymity. Inputs and outputs still appear on-chain, and transactions can be identified using toolsets such as coinjoinsudoku.
Even so, such measures are worth taking to avoid becoming an easy mark for crypto-fraudsters. In some cases, generate a new address for each transaction or counterparty, avoid sending sensitive transactions via exchange accounts, and use open-source wallets.
4
Are there commercial tools for tracking BTC transactions?
5
Chainalysis
Perhaps the best-known player in Bitcoin-tracing is the American blockchain analytics startup Chainalysis. Since 2015 it has helped the US Internal Revenue Service (IRS) identify people evading taxes on cryptocurrency operations. The company works with Europol, law-enforcement agencies around the world and crypto-exchanges.
Its core products are Chainalysis Reactor and Chainalysis Know Your Transaction (KYT). Reactor lets investigators launch automated inquiries from any starting point given even a small crypto-data lead. KYT, built as an anti-money-laundering tool, uses an API to monitor vast data volumes in real time and flag high-risk transactions. For example, since autumn 2018 the cryptocurrency exchange Binance has used Chainalysis KYT “to build a blockchain ecosystem where everyone will feel safe”.
Chainalysis’s tools are not publicly accessible, making it impossible to assess the methodology or rule out false positives. In court cases, parties have at times questioned the reliability of Chainalysis’s transaction data for this reason.
6
Crystal
In January 2018 Bitfury Group, one of the world’s largest developers and providers of blockchain solutions, unveiled Crystal for financial institutions and law-enforcement agencies—built specifically for Bitcoin-related investigations.
Crystal analyses the Bitcoin blockchain, focusing on specified addresses and transaction sets, and also goes off-chain to gather relevant data from available sources such as websites and thematic forums.
The tool visualises fund flows down to the final address and conversion of cryptoassets into fiat, and emails the results to the client. Whereas manual tracking can be overwhelmed by branching flows of funds, Crystal produces a list of concrete addresses that received the money and enumerates every path the funds took.
Investigations can go deeper into transaction risk assessment and track suspicious activity at a BTC address. The developers say that by applying a unique clustering algorithm, Crystal can ultimately identify the real name of a coin holder.
Version 2.2 added several investigator-friendly features. Clients can configure notifications on activity for a given address, add all addresses from a transaction to monitoring and visualisation with one click, and trace operations conducted between addresses via intermediaries.
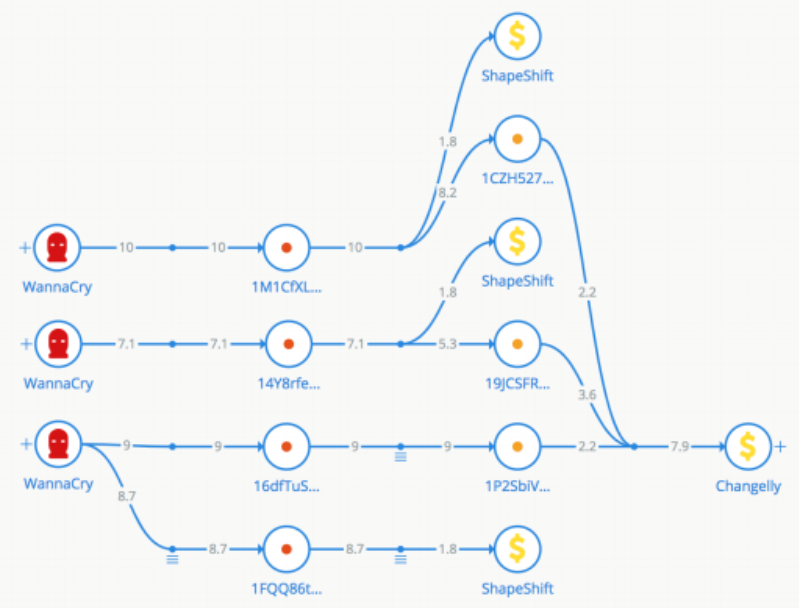
As proof of effectiveness, its creators cite the WannaCry ransomware case. In May 2017 it inflicted almost $1bn of damage in four days, hitting Britain’s National Health Service, Telefónica in Spain, America’s logistics giant FedEx and users in 150 countries. Using Crystal, its creators tracked the movement of funds from the attackers’ Bitcoin wallets in three hours—to off-ramps via the Changelly and ShapeShift exchanges—and determined who was behind the attacks.
Bitfury also investigated the September 2018 hack of the Japanese exchange Zaif, which lost $60m in cryptoassets, including 6,000 bitcoins.
The researchers found that part of the loot was sent for cash-out via the Binance exchange; another part was split into small sums and scattered to numerous addresses via mixers, gaming services and other exchanges; and 30% remained at previously unseen addresses presumed to belong to the attacker. Those addresses, registered to unknown persons, were then placed under continued observation in Crystal.
7
Elliptic
Founded in London in 2013, Elliptic—now a provider of blockchain analytics—once served as a cold wallet for storing private keys to Bitcoin addresses, before pivoting to anti-money-laundering services for crypto-exchanges and financial firms.
Elliptic also developed software used by law enforcement to track terrorist financing in bitcoin. The firm works with the FBI and CIA and is known for investigations into criminal activity on the dark web.
As the company explains, web scraping of “clean” sites and the dark web, plus monitoring court-filing registries, can surface references to crypto addresses, which are then analysed and, in the dark web, probed for interaction or emulated.
To identify real owners of wallets on the dark web, Elliptic applies machine-learning algorithms: the software focuses on addresses known to be used on a given platform, then uses that technology to identify other addresses and transactions on the same marketplace. For law enforcement, the findings are rendered graphically in a transaction explorer.
Details of the London startup’s work with the FBI and CIA are not public. It is known, however, that the company played a significant role in cases against a darknet drug dealer from Portsmouth, sentenced to 16 years for selling ecstasy for bitcoin, and a businessman who tried to import firearm parts into Britain after buying them on the dark web for bitcoin. In July 2018 Elliptic specialists also said that officers of Russia’s military intelligence (the GRU), accused of meddling in America’s 2016 presidential campaign, conducted bitcoin transactions and laundered funds via the BTC-e exchange.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!