What is the darknet? What is Tor?


1
What is the darknet?
Attention! The article is outdated and awaiting an update.
The darknet is a hidden network on the internet in which connections are established only between trusted peers, using non‑standard ports and custom data‑transfer protocols.
The term “darknet” is often used interchangeably with “dark web”. The dark web is the part of the World Wide Web accessible via overlay networks—that is, the “darknets” themselves.
The darknet (dark web) is sometimes confused with the so‑called deep web—web pages not indexed by search engines. Unlike the darknet, accessing the deep web does not require specialised software.
The opposite of the darknet is the visible or surface web—the part of the internet indexed by search engines and publicly accessible.
2
When and how did the darknet emerge?
Originally, the term “darknet” referred to computers on ARPANET, created in 1969 by the Defense Advanced Research Projects Agency (DARPA) of the US Department of Defense. ARPANET was a prototype of the internet. Computer networks—“darknets”—were configured to receive messages from ARPANET, but their addresses were not listed and they did not respond to external queries, thereby remaining “dark”.
The term gained prominence after the 2002 publication of a research paper, “The Darknet and the Future of Content Distribution”, by Microsoft employees Brian Willman, Marcus Peinado, Paul England and Peter Biddle. They argued that the presence of a darknet is the main obstacle to the development of digital‑rights‑management (DRM) technologies and will inevitably lead to copyright infringement. In the paper, the darknet was described broadly as any network requiring a specific protocol for access and existing “parallel” to the surface or visible web.
The term spread widely via the media, which associated it with the anonymous marketplace Silk Road, active from 2011 to 2013 in the .onion zone of the Tor network.
3
How is the darknet used?
It is used to bypass censorship, content‑filtering systems and surveillance. It also supports file‑sharing.
The technology can be used by political dissidents and criminals alike.
4
Which anonymous networks does the darknet use?
5
What is Tor?
6
How does Tor work?
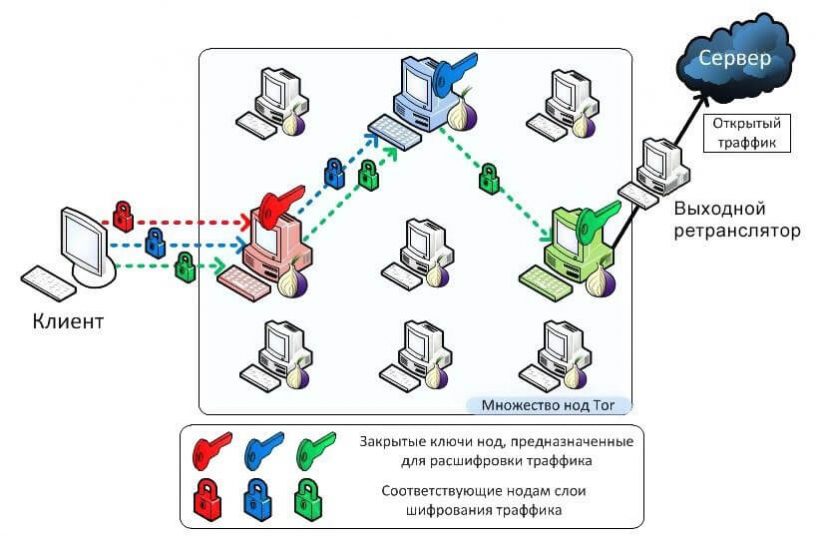
Unlike a regular browser, which sends user data straight to a server and allows third parties to determine location, the Tor Browser relays data through a chain of nodes—intermediate relays scattered around the world. This model makes tracking far harder.
Tor architecture
How Tor works:
- On launch, the program forms a circuit of three random nodes through which traffic flows.
- When a request is sent, the data are wrapped in three layers of encryption (the multilayer design resembles an onion, hence the “onion” name).
- The first node removes the outer layer of encryption. It learns the address of the previous and the next node, then forwards the data onward.
- The process repeats and the data reach the last node in the circuit—the exit node.
- The exit node fully decrypts the payload and forwards the request to its destination.
- The response returns along the same path, passing through the same stages.
7
Does Tor guarantee complete anonymity?
8
How did Tor originate?
Development of Tor began in 1995 under a US government contract at the High‑Performance Computing Systems Center of the US Naval Research Laboratory (NRL), as part of the Free Haven project in collaboration with DARPA. The source code was distributed as free software.
In the early 2000s the project was named The Onion Routing (Tor). In October 2002 a network of routers was deployed which, by the end of 2003, included more than ten nodes in the United States and one in Germany.
Since 2004 the project has received financial and informational support from the civil‑liberties organisation Electronic Frontier Foundation.
In 2006 a non‑profit organisation was created in the United States to develop the network, the Tor Project.
In 2008 the Tor Browser appeared.
9
Who funds Tor?
10
How is the Tor project developing?
The team promotes the project, urging the use of Tor to defend the right to free access to information and to privacy.
The Tor Project’s administrators oppose cybercrime: together with the US Agency for International Development, the Brookings Institution, the Cato Institute, the Bill & Melinda Gates Foundation, Trend Micro and the Bitcoin Foundation, they are part of a working group on combating cybercrime.
Tor is supported by many advocates of online security and privacy, including former NSA employee Edward Snowden and WikiLeaks founder Julian Assange.
On the pretext that Tor hosts numerous markets for drugs, weapons, pornography and the like, law‑enforcement agencies in various countries have targeted it. In 2014 the FBI paid $1m to researchers at Carnegie Mellon University in the United States for help de‑anonymising Tor users.
In 2017 Russia passed a law obliging anonymisers, including Tor, to block services and websites on Roskomnadzor’s blacklist, but Tor refused to comply.
In July 2019 the hacker group 0v1ru$ hacked the server of Saitek, a company presumed to be a contractor to Russian special services. Documents obtained by the hackers contained information on several secret projects by the Russian authorities aimed, among other things, at analysing Tor traffic.
In October 2019 the Tor administration conducted a large‑scale “cleanup” of the network, blocking 13% of all active nodes. They were blocked for using outdated software. The “cleanup” was intended to make the network faster and safer.
In November 2019 Tor released a software update capable of automatically blocking connections to obsolete nodes. Abandoned entry points whose IP addresses were not listed in public directories were also blocked.
In March 2020 the Russian “Main Radio Frequency Centre”, subordinated to Roskomnadzor, began studying the possibility of restricting mesh networks, IoT networks and anonymous protocols. The technologies under review included The Onion Router (TOR), Invisible Internet Project (I2P), Telegram Open Network, Freenet, Zeronet, anoNet, and the mesh networks Yggdrasill, cjDNS, Briar, Signal Offline and FireChat.
The work was assigned to the Federal Research Centre “Informatics and Control” of the Russian Academy of Sciences. It was allocated 9.2m roubles, with a report due by 30 June 2020.
Russia ranks second by number of Tor users after Iran. In 2019 slightly more than 330,000 Russians used the browser daily, accounting for 17.39% of all users.
11
What other anonymous darknet networks exist?
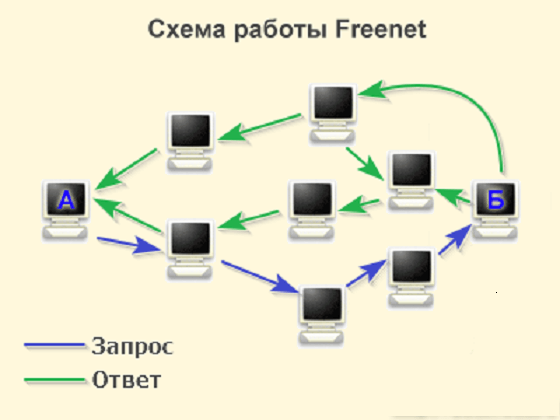
Freenet is a peer‑to‑peer network designed for decentralised, distributed data storage.
Unlike Tor and I2P, Freenet provides anonymity only within its own network.
Freenet has no servers; all data are stored in encrypted form on users’ computers, pooled together. Users contribute bandwidth and disk space to publish or retrieve information. To locate data, Freenet uses key‑based routing similar to a distributed hash table.
Users can choose the level of protection: the lower it is, the faster the connection, but at the expense of data security.
Even at low protection, connections remain slow: loading an image can take several minutes, and video playback is impossible, since Freenet does not support the databases and scripts required for dynamic content. The project’s purpose is censorship‑resistant data storage, not performance or ease of use.
Freenet is split into two parts: Opennet and Darknet. Opennet is the public segment; access to Darknet is by invitation only.
12
What is I2P?
I2P (Invisible Internet Project) is an overlay anonymous network consisting of two types of nodes:
- Routers. They have internal network and regular IP addresses, are reachable on the public internet and keep the I2P network running.
- Hidden nodes. They have no IP addresses.
I2P separates routers and destinations, hiding where the destination is and which router it is connected to. Each user has several addresses—for websites, torrents and so on—complicating tracking and identification.
I2P is based on tunnels—paths through several routers. As in Tor, multilayer encryption is used: each router decrypts one layer. Unlike Tor, return traffic travels through a separate tunnel.
The user can set tunnel length. The longer the tunnel, the lower the chances of detection, but the slower the connection.
Digital signatures and strong cryptography make I2P the most secure darknet network at the moment.
Subscribe to Forklog on Facebook!
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!