Who Are “White Hats” and How Do They Protect the Blockchain Industry?


Who are ‘white hats’?
The term “white hats” likely comes from cinema. In Westerns, cowboys in white hats symbolised the good guys, while the villains wore black.
The term “white-hat hackers” emerged in the 1960s, when research institutions began examining computer systems for vulnerabilities in order to fix them and improve security.
The subculture took off in the 1990s with the rise of the internet. White-hat hackers were increasingly brought in to defend systems, find weak spots and conduct penetration tests.
White hats have become integral to the blockchain industry, helping to combat cybercrime. Numerous professional training courses, bounty programmes and decentralised platforms such as Immunefi and Hacken channel talent in an ethical direction.
What other hats do hackers wear?
Beyond “white” and “black”, the community has put hackers in four more colours, depending on their intentions and methods:
- “grey hats” (gray hats). These hackers oscillate between white and black, switching sides with ease. They usually lack criminal intent, but may break into company products without permission. In some cases, they will not pass up the chance to sell data that comes into their possession;
- “blue hats” (blue hats). At Microsoft, this denotes good hackers—an analogue of “white hats”. The tech giant’s Microsoft BlueHat Conference promotes having products attacked by hackers before release. A second meaning can be found in public sources: hackers who break into resources for personal reasons, out of revenge;
- “green hats” (green hats) — novice hackers who still lack experience and skills. They may cause inadvertent damage and not know how to remedy the consequences of their activity;
- “red hats” (red hats) — hacker vigilantes, the main threat to “black hats” after law enforcement. Their principal aim is to punish wrongdoers by any means.
How do white hats operate in Web3?
White hats differ from black hats in that they obtain permission to hack from the system’s owner. Ethical hackers work proactively, fixing problems before adversaries discover them. Core techniques and methods in Web3 include:
- auditing smart contracts. Analysing code for overflow, unauthorised access or logical errors that could lead to loss of funds. Audits use both manual and automated tools such as Mythril, Securify and Slither;
- penetration testing. Finding weak entry points and simulating real attacks on the security mechanisms of blockchains, dapps and smart contracts. This may include social engineering and phishing to compromise accounts, keys and wallets;
- researching vulnerabilities in cross-chain bridges. This popular attack vector requires particular attention: issues in transaction verification, vulnerabilities in consensus algorithms and cross-network operations are examined;
- bug-bounty programmes. Run by blockchain firms and audit platforms, these initiatives help protect potential victims and financially incentivise white hats;
- reverse engineering. Analysing smart contracts and dapps through reverse development. This can uncover vulnerabilities, especially when code is available only as bytecode.
White-hat work typically follows four stages:
- Pre-engagement. Discussing the scope and goals of testing with system owners.
- Gathering information about the system, network and potential vulnerabilities.
- Threat modelling related to dapps, smart contracts or infrastructure providers. Creating an account and attempting a trial breach.
- Exploitation. Verifying identified bugs to confirm risks. Compiling a report that lists all issues found, ways to fix them and recommendations for the business.
How are white-hat hackers trained?
According to the Hacken blog, hacking is “more a way of life than a set of specialised skills”:
“Many enter this field after getting into computer games; some have a background in computer science, and others come from applied mathematics. Eventually they find a vulnerability, dig deeper, enjoy the process, and start looking for bugs again and again. Put simply, self-education makes a person a programmer, and curiosity makes a programmer a hacker.”
In traditional IT, white hats have been used for decades; training and upskilling processes are therefore well established.
In the view of the popular platform for ethical hackers HackerOne, you can become a certified cybersecurity professional in a few steps, including through its free Hacker101 courses.
To gain practical experience, it recommends joining the community and taking part in competitions such as Capture The Flag (CTF).
For a successful career and easier client acquisition, it helps to validate your skills with recognised certifications:
- Certified Ethical Hacker (CEH). Issued by EC-Council, it covers methodologies, tools and techniques of ethical hacking;
- Offensive Security Certified Professional (OSCP). A hands-on approach to penetration testing;
- CompTIA Security+. Covers foundational concepts and practices in cybersecurity.
Is it legal?
Unauthorised hacks are the province of grey hats; even with good intentions, they may face legal consequences. White-hat work requires careful alignment with the law.
Underdeveloped legislation in digital security and blockchain systems poses serious risks for them. There is no guarantee that an expert’s help will not be turned against them.
Main legal constraints white hats face include:
- confidentiality. Handling personal data, intellectual property or trade secrets demands care and responsibility;
- compliance with laws and regulations. The obligation to follow applicable law, such as the Computer Fraud and Abuse Act (CFAA) in the United States or the General Data Protection Regulation (GDPR) in the EU;
- non-disclosure agreements (NDA). Some clients may require signing such documents to protect a target organisation’s confidential information and trade secrets. Breaching an NDA can lead to legal consequences.
What is the Security Alliance (SEAL)?
On February 14, 2024, Paradigm’s head of security—and noted white hat—samczsun called on the Web3 community to unite in defending the rights of “ethical hackers” in their fight against crypto crime. That day, a non-profit—the Security Alliance (SEAL)—and the Whitehat Legal Defence Fund were formally registered.
He said his motivation was to reduce legal risk for peers. He recalled the 2022 hack of the Nomad cross-chain protocol for more than $186m, when many white hats wanted to help but had to watch from the sidelines. Thanks to the efforts of individuals who would later form SEAL, it managed to save about $39m, and Nomad was relaunched.
After the incident, samczsun proposed a round-the-clock “rescue service” — SEAL 911. Anyone affected by a hack, or noticing suspicious activity, can reach out in a Telegram chat for free, real-time assistance. The service operates in line with applicable legal frameworks.
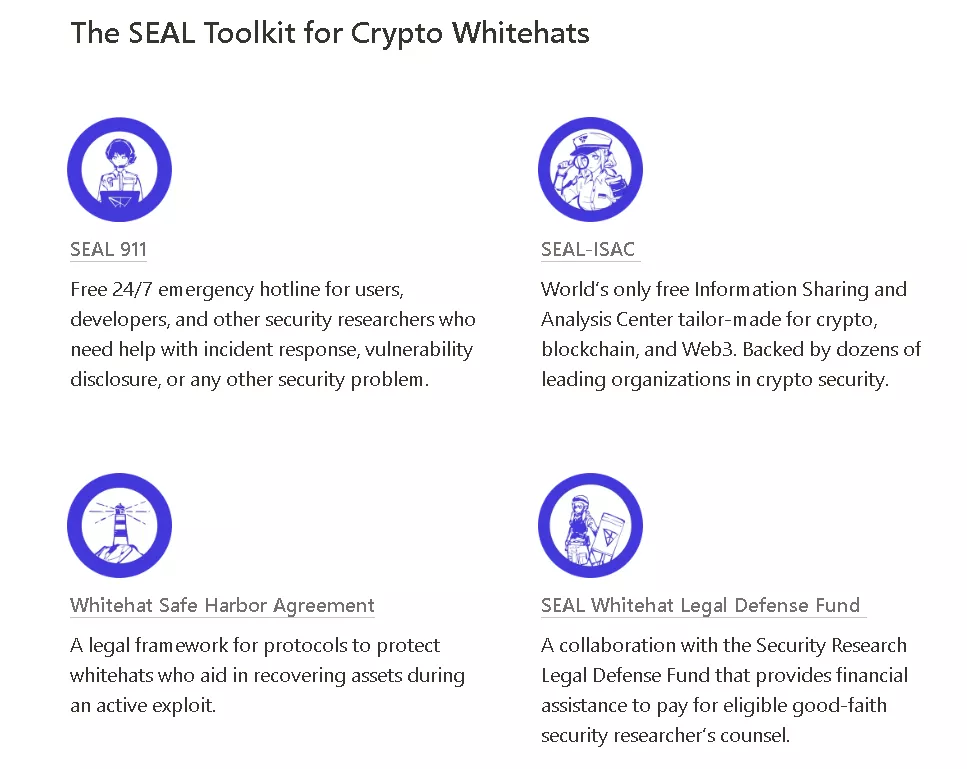
SEAL also includes SEAL-ISAC — an analytical, information-sharing centre for crypto security — and the Whitehat Safe Harbor Agreement.
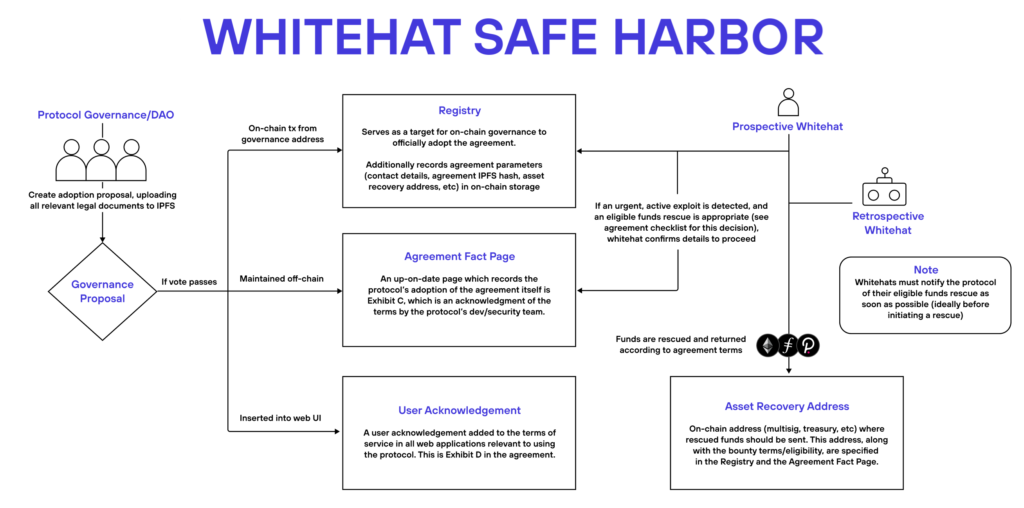
The purpose of the Safe Harbour Agreement (SHA) is to shield white hats from unfair prosecution and bring legal clarity to their actions. It is concluded between a protocol under attack and specialists who come to help, allowing them to intervene and redirect funds to a safe address (“harbour”) for recovery.
What is Immunefi?
Immunefi is a Web3 cybersecurity platform. It was founded in December 2020 by Mitchell Amador and is one of the leading venues for bug bounties.
Its main task is to create a safe environment in which white hats can responsibly disclose discovered vulnerabilities and receive rewards. The start-up works with Safe Harbor Agreements, similar to SEAL.
The platform is valued for its generous rewards and systemic analytics. Over its lifetime, more than $100m has been paid out to hackers.
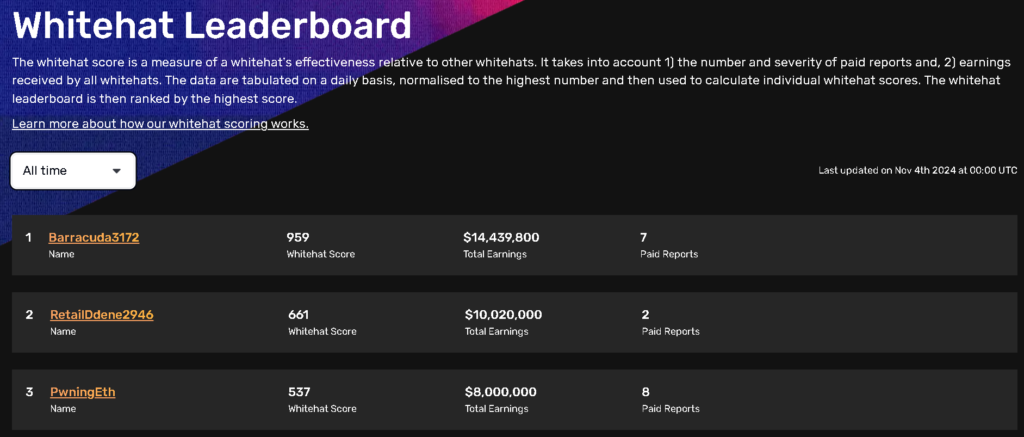
In 2022, the team launched a white-hat rating system. Updated daily, it classifies hackers by the number and complexity of paid reports, as well as total earnings.
Immunefi recognises outstanding ethical hackers with NFT items from the Whitehat Hall of Fame collection. They are unique and issued as one-of-ones.
Immunefi also provides security consulting. Its specialists help projects build more resilient and secure systems.
The organisation partners with major industry players to help projects minimise cyber-risk and bolster user trust in Web3. It frequently runs attackathons.
In September 2022, Immunefi closed a $24m Series A led by Framework Ventures, with participation from Electric Capital, Polygon Ventures, Samsung Next and others.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


