
LinkedIn account breaches, arrest of Lolek admins and other cybersecurity events
We round up the week’s most important cybersecurity news.
- Europol arrested administrators of the Lolek hosting service and seized its servers.
- The crypto-stealing apps were masquerading as beta versions of legitimate software.
- LinkedIn users faced a mass account breach.
- Cybersecurity specialists examined more than 100,000 compromised hacker profiles.
Europol arrests administrators of the Lolek hosting service and seizes its servers
In Poland, at the request of Europol and the U.S. Department of Justice five were arrested for the operation. Their servers have been seized.
According to law enforcement, cybercriminals used the service’s resources to organise DDoS attacks, carry out spam campaigns, disseminate infostealers, deploy command-and-control servers and counterfeit online stores.
One of the detainees was a Polish citizen named Artur Karol Grabowski.
The Ministry of Justice asserts that he helped the now-defunct Netwalker ransomware group rent Lolek servers, used in more than 50 attacks.
Grabowski has been charged with conspiracy to commit computer fraud, as well as money laundering on an international scale. He faces up to 45 years in prison.
Crypto-stealing apps masqueraded as beta versions of legitimate software
The attackers promote “beta versions” of apps supposedly designed for cryptocurrency investments to steal users’ digital assets. The FBI reported on the new scheme.
Using beta versions allows hackers to bypass app-store checks.
According to the agency, in this scheme attackers either ask users to enter credentials from an existing exchange account, or substitute legitimate addresses in transactions with their wallets.
LinkedIn users faced a mass account breach
Over the past few weeks, social media have been flooded with mass complaints from LinkedIn users about breaches or account blocks. The issue drew the attention of Cyberint researchers.
To compromise profiles, attackers use previously leaked credentials or brute force. In the event of a successful breach, hackers replace the linked email address with a Rambler.ru mailbox.
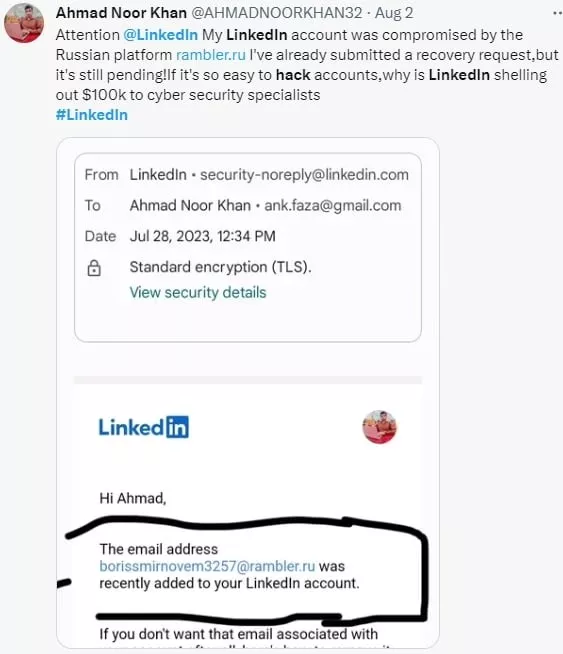
Among the affected were also users whose accounts were protected by strong passwords and two-factor authentication. They faced temporary account blocks due to multiple login attempts.
LinkedIn representatives have not commented on the incident yet.
Cybersecurity specialists studied more than 100,000 compromised hacker profiles
Hudson Rock researchers discovered 120,000 infected systems containing credentials for cybercrime forums. Many of the machines belong to hackers.
To identify the latest, experts used infostealer logs RedLine, Raccoon and Azorult, containing additional data, including names, email addresses, phone numbers and IP addresses.
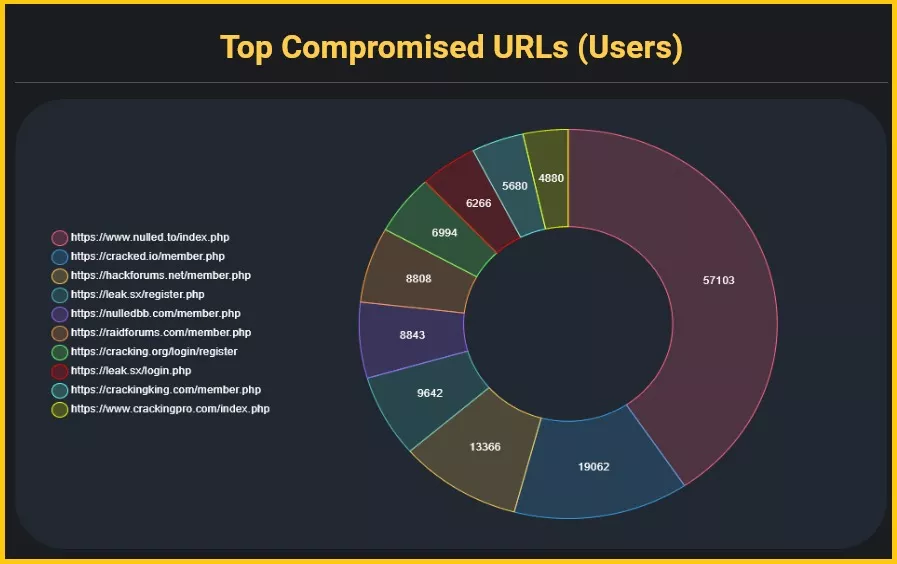
More than 57,000 compromised users had accounts on the Nulled.to community for aspiring cybercriminals. Cracked.io and Hackforums.net ranked second and third.
Users of the BreachForums hack forum had the most reliable login passwords for the site — more than 40% of them were at least 10 characters long and used four different types.
Most of the hacker profiles studied by Hudson Rock belong to residents of Tunisia, Malaysia, Belgium, the Netherlands and Israel.
Discord.io data breach affects 760,000 users
On August 14, a database of users and access to the Discord.io server — a third-party service for creating custom invites to Discord — appeared for sale on a dark-net forum. The Telegram channel “InfoLeaks” reports.
According to the seller using the nickname Akhirah, the dump includes logins and email addresses of 760,000 users. It also contains partial information about hashed passwords and payment addresses.
The next day the service’s administrators confirmed the incident. The site was temporarily taken offline during the investigation.
In a comment to Bleeping Computer, the hacker responsible for the breach explained that Discord.io allegedly contains links to illegal and malicious content. If these materials are removed, he is willing to abandon the data leak.
Experts warned of a more sophisticated phone-fraud scheme
To conduct more targeted attacks, phone scammers began posing as colleagues of their victims. Experts from the Kaspersky Lab reported.
In this scheme, the target user receives in a messenger a notice about an upcoming “important” call from law enforcement or supervisory authorities. To gain the victim’s trust, criminals pose as employees of the same field or send messages from previously stolen accounts of the victim’s real colleagues.
During the subsequent call, the user is subjected to psychological pressure to cooperate with the “law enforcement,” after which they are redirected to a “trusted” financial institution and forced to transfer funds to the specified details.
Sometimes cybercriminals may persuade the person to buy a separate phone or SIM card and turn off their personal device for added security.
Also on ForkLog:
- Over five years, North Korean hackers stole cryptocurrency worth $2 billion.
- The DeFi project Exactly Protocol was hacked for $12 million.
- The court denied Coinbase’s motion to remove sanctions from Tornado Cash.
- Eighteen crypto companies from Ukraine were placed on the list of suspicious entities.
- In Singapore, a group was arrested for laundering more than $700 million via cryptocurrencies.
- The developers of SwirlLend carried out a rug pull of $460,000.
- The FBI seized about $1.7 million in cryptocurrencies over three months.
- De.Fi released a antivirus scanner on the zkSync Era network.
- The RocketSwap Base platform lost $870,000 due to key leakage.
- A Chinese company was accused of organizing a financial pyramid for Filecoin mining.
- Uniswap fired a developer over possible fraud.
- The DeFi protocol Zunami, in an exploit, lost $2.1 million.
- Curve returned 70% of the funds stolen by the hacker.
What to read this weekend?
ForkLog published a chapter from journalist Geoffrey Cain’s “The State of a Strict Regime,” about how China developed the first AI systems for citizen surveillance.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


