
Cryptominer infections in 164 countries, Israel hit by hackers, and other cybersecurity developments
Here is a round-up of the week's most important cybersecurity news.
- More than 250,000 computers were infected with a miner after downloading a torrent file.
- A spyware worm spent five years masking its true functions.
- Turkish hackers say they breached Israel's Ministry of Defense systems.
- 167 VPNs and more than 200 email services were blocked in Russia.
More than 250,000 computers infected with a miner after downloading a torrent file
Positive Technologies discovered the autoit stealer campaign distributing a hidden miner via pirated software on torrents. It has infected more than 250,000 Windows-powered computers in 164 countries.
The vast majority of victims — over 200,000 — are in Russia, Ukraine, Belarus and Uzbekistan.
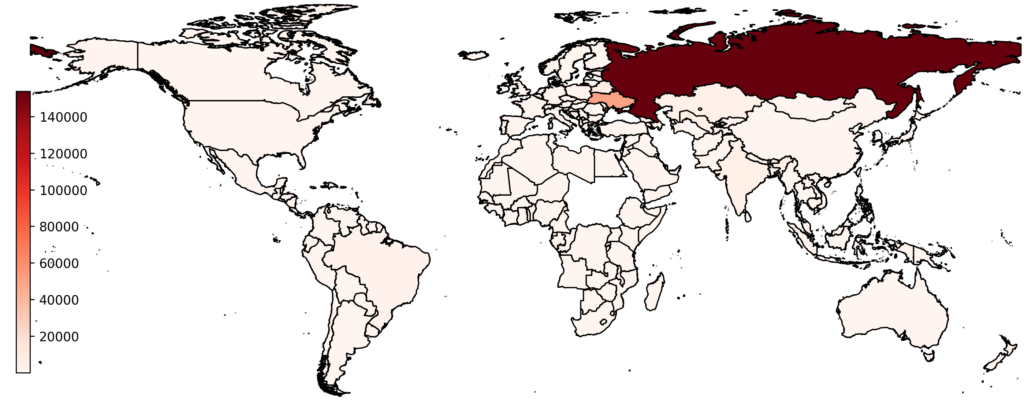
Most victims are ordinary users, but government bodies, oil and gas firms, healthcare facilities, retailers and IT companies are also affected.
Infection occurs after downloading a malicious torrent file from topsoft.space. Upon reaching the victim's device, the malware collects information about the system, installs the XMRig miner, and archives the Telegram folder contents — tdata.
The latter allows the attacker to access the user's session in the messenger, discreetly monitor the conversations and exfiltrate data from the account. Even when two-factor authentication is used as a password, the attacker can successfully brute-force it.
A Telegram bot serves as the command-and-control server. Analyzing messages from it, Positive Technologies identified the supposed operator of the malware under the nickname splokk.
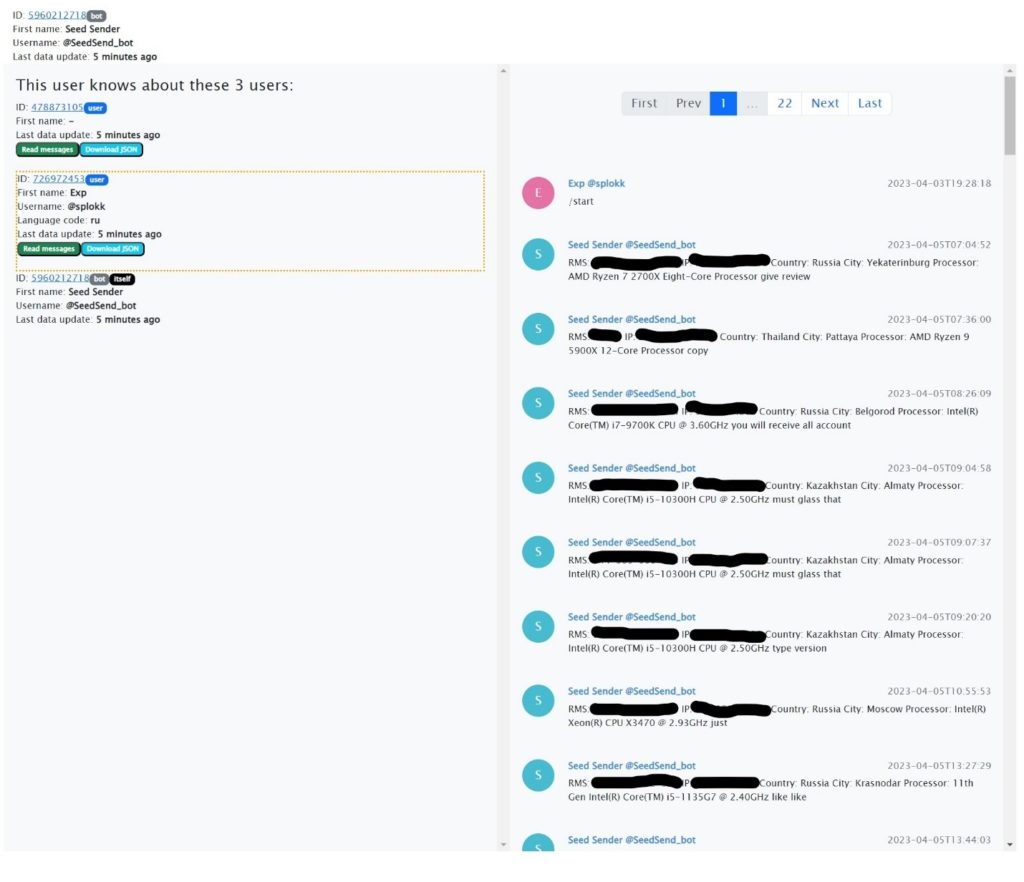
Based on the aggregate data, experts believe the attack's likely aim is to resell stolen Telegram access credentials.
The espionage worm spent five years masking its true functions with an embedded miner
The StripedFly malware framework, active since 2017, presented itself as a routine hidden crypto miner, but is in fact a sophisticated piece of malware with espionage capabilities, according to researchers at Kaspersky Lab.
StripedFly targets Windows and Linux machines. Over five years, it has victimized more than a million users worldwide.
Recent analysis shows that the payload comprising several modules enables the malware to act as an APT, a cryptominer, ransomware and spyware.
Every two hours it collects credentials for various sites and for connecting to Wi‑Fi, as well as personal information, including name, address, phone number, workplace and job title.
In addition, the malware can discreetly take screenshots, gain full control of the device, and even record audio from the microphone.
Moreover, StripedFly features a sophisticated traffic-masking system via Tor, automatically updates from trusted platforms and spreads like a worm via a custom EternalBlue exploit.
Kaspersky Lab warned that the campaign remains active to this day, albeit on a smaller scale.
The Turkish hackers say they breached Israel's Ministry of Defense systems
The hacker group Ayyıldız Tim from Turkey says they hacked Israel's Ministry of Defense systems and obtained access to secret data about its operations and personnel.
İsrail Savunma Bakanlığı'na ait çok gizli askeri veriler, tatbikat verileri ve personel verileri Ayyıldız Tim tarafından hacklenip ele geçirilmiştir.
Türk’ün gücünü göreceksiniz!
Sessizce nöbetteyiz!#AyyıldızTim ?? pic.twitter.com/wRkJur8fZt
— Ayyıldız Tim ?? (@AyyildizTim209) October 22, 2023
In their X posts, the hackers also announced plans to attack Israel's stock exchange, power infrastructure and dam systems “after receiving the relevant instruction.”
The Defence Ministry did not comment on the matter.
In Spain, 34 cybercriminals were arrested for money laundering through cryptocurrencies
Spanish police dismantled a cybercrime group that used various schemes to steal confidential data and money. More than 4 million people were affected by its activities.
According to investigators, the criminals ran telephone scams, deployed large-scale phishing campaigns posing as electricity suppliers and delivery services.
They also hacked various financial firms, contacted their clients and asked them to repay a loan allegedly issued due to a technical error. Stolen user data were also resold to other criminals.
In total the criminals obtained about $3.2 million and laundered it, including via cryptocurrencies.
Authorities arrested 34 people and conducted 16 searches, during which they seized firearms and bladed weapons, four luxury cars, €80,000 in cash, and computers with a database of four million citizens.
CCleaner confirms breach tied to the Cl0p MOVEit Transfer incident
The makers of CCleaner sent users letters detailing a breach caused by the Cl0p MOVEit Transfer incident.
According to them, the attackers managed to steal data from some employees and clients, including their name, email address and phone number.
However, CCleaner classified the breach as a low-risk leak.
The company continues its investigation and intends to offer all affected parties free darknet monitoring services to search for personal information.
The attacker who compromised Cisco modified the backdoor to conceal it
Over the past weekend the number of compromised due to zero-day vulnerabilities in Cisco IOS XE devices sharply declined from 40,000 to a few hundred.
Please note that a potential trace cleaning step is underway to hide the implant (following exploitation of #CVE-2023-20198) 1/2 https://t.co/i9y2MzwpZ5
— CERT Orange Cyberdefense (@CERTCyberdef) October 21, 2023
As Fox-IT NCC Group researchers found, the attackers modified the backdoor to conceal itself during scanning. It now responds only when the correct HTTP Authorization header is present.
Experts estimate the number of affected devices remains at least 37,000, including Rockwell Automation's Stratix industrial Ethernet switches.
Cisco, in turn, reported discovery of a new zero-day vulnerability used in the attack to escalate privileges and gain root access.
Patches for both issues are available on the company's website, alongside a mechanism to check a workstation for the implant.
Experts did not rule out that the mass IOS XE compromise could be a lure to obscure the attackers' real goals.
167 VPNs and more than 200 email services blocked in Russia
Roskomnadzor, in its bid to counter cybersecurity threats and the resilience of the Russian segment of the internet, restricted 167 VPNs, over 590,000 information resources and more than 200 email services. Interfax reported.
Meanwhile, the average effectiveness of VPN blocking was estimated at 90%.
Additionally, Roskomnadzor blocked 2,000 phishing sites, 84 apps and more than 20 malware-distribution centres.
The agency's automated internet-safety system now covers almost 100% of telecoms traffic, which together exceeds 100 Tbps.
Also on ForkLog:
- Creators of 'fake' BAYC tokens will pay $1.6 million to Yuga Labs.
- Russia opens the first treason case over cryptocurrency donations.
- Britain passes a bill to ease confiscation of crypto assets.
- Gary Gensler again warns of the prevalence of scams in the crypto industry.
- Elliptic points to a small share of cryptocurrency in Hamas funding.
- Unciphered proposed hacking the wallet of Ripple’s former CTO containing 7,000 BTC.
- A Spanish court accuses a hacker of advising “the Russian mafia” on Bitcoin.
- CipherBlade leadership accused of asset theft and “takeover” of the company.
- An expert detects movement of 4,800 BTC from the closed dark-net market Abraxas.
- A Bitcoin developer reveals a critical vulnerability in the Lightning Network.
What to read this weekend?
An interview with the winners of the DemHack hackathon about why there is no need to fear that dictators know how to wield cutting-edge technologies.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


