
US seizes $15bn in bitcoin from Cambodian gang leader, Khmelnytskyi crypto ring and other cybersecurity news
The week’s key cybersecurity stories.
The week’s key cybersecurity stories.
- Hackers have adapted malware for blockchain.
- Global Ledger: a report on cross-chain bridge hacks.
- Law enforcement dismantled a Khmelnytskyi crypto gang.
- The US seized $15bn in bitcoin from the leader of a Cambodian group.
Hackers adapt malware for blockchain
On 17 October, Google Threat Intelligence Group (GTIG) reported that hackers have begun using a technique called EtherHiding to host and deliver malware via smart contracts. The method is used to steal cryptocurrencies in socially engineered attacks.
According to the analysts, a North Korean group known as UNC5342 has used EtherHiding since February in operations dubbed Contagious Interview.
EtherHiding embeds malicious data into smart contracts deployed on public blockchains such as Ethereum.
Thanks to the properties of blockchains, EtherHiding offers:
- anonymity for operators;
- resilience to blocking and takedowns;
- flexible, low-cost updates to malicious code;
- high stealth, leaving no traces in transaction histories.
The smart contract contains a JADESNOW loader that interacts with Ethereum and launches the second stage — the InvisibleFerret JavaScript malware, typically used for long-term espionage.
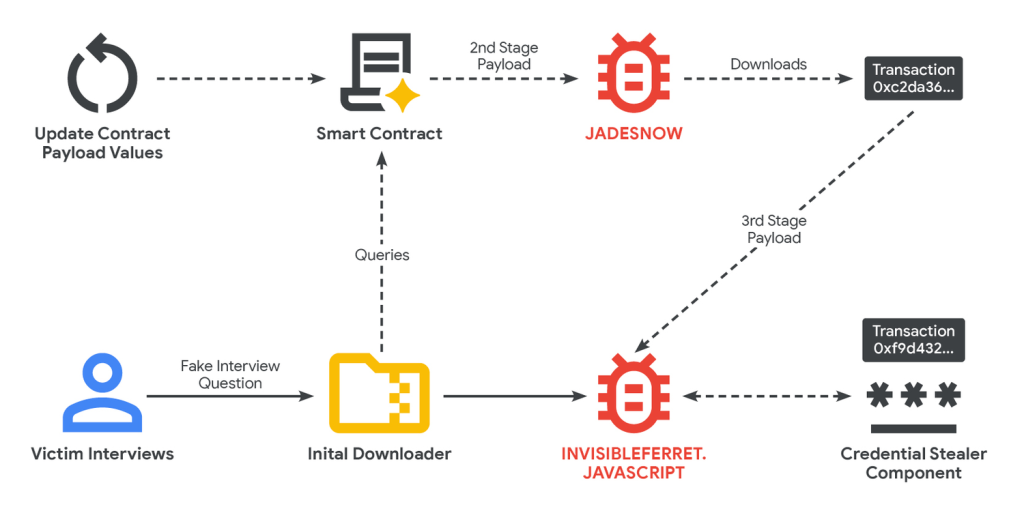
Attacks typically begin with fake job interviews at fictitious firms — a familiar North Korean tactic. Victims are coaxed into executing code as part of a supposed technical test; in reality it triggers malicious JavaScript.
Once installed, the malware:
- runs in the background;
- awaits commands from a remote server;
- can execute arbitrary commands and exfiltrate stolen files as ZIP archives to an external server or Telegram.
GTIG notes that the malware runs in memory and can fetch from Ethereum an additional module designed to steal credentials.
In the first four months, the contract was updated more than 20 times, with each upgrade costing on average just $1.37 in fees.
The malicious component targets passwords, bank-card data and wallets such as MetaMask and Phantom, as well as browser data.
Global Ledger: cross-chain bridge hacks report
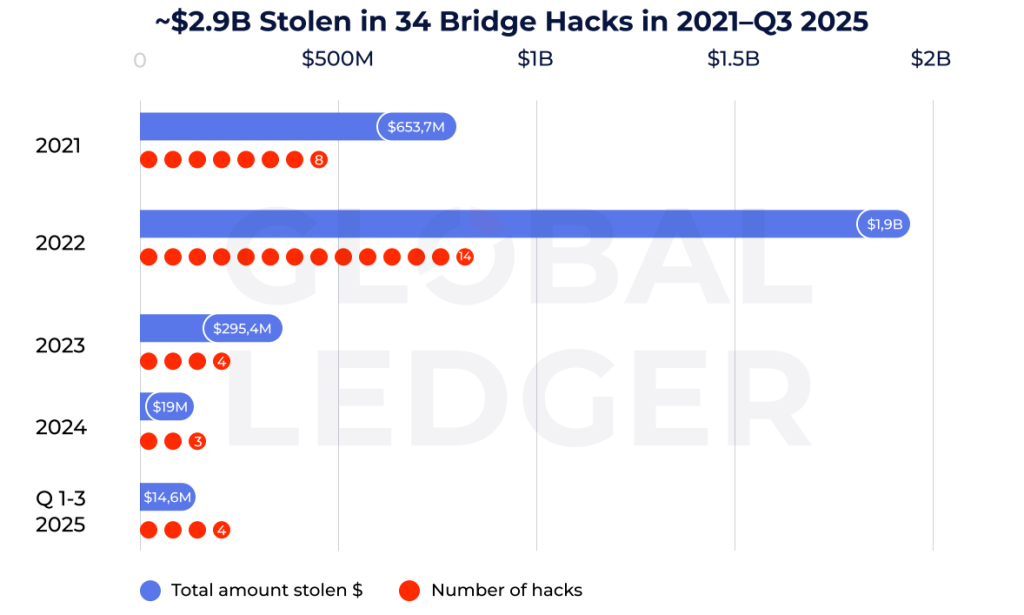
In October, analysts at Swiss firm Global Ledger released a report on confirmed cross-chain bridges hacks from 2021 through Q3 2025. Over the period there were 34 attacks, with losses of ~$2.9bn.
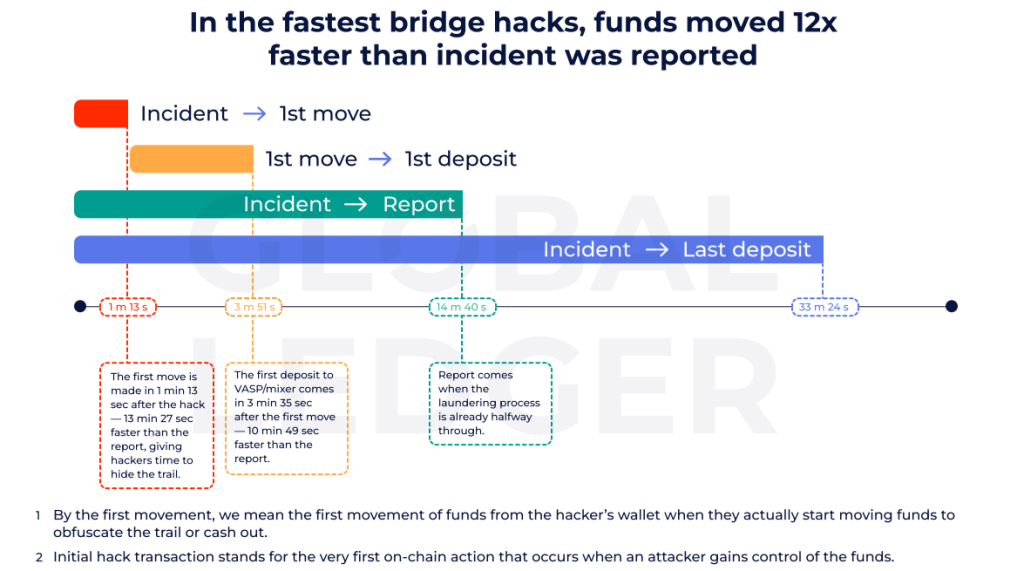
In 85% of cases, funds were moved before the incident was publicly disclosed. Initial transfers occurred on average within 2 hours 15 minutes, whereas public disclosure lagged by roughly 22 hours.
In 91% of incidents, funds moved within the first 24 hours; in one case, the full laundering cycle — from attack to final destination — took just 33.5 minutes.
The report records a speed record for moving stolen funds after a bridge hack: 1 minute 13 seconds.
Analysts highlight heavy reliance on the Tornado Cash mixer, used in 96% of cases involving transaction obfuscation.
The largest share of stolen assets was laundered through DeFi platforms, totalling ~$1.48bn. About $959m flowed through mixers and other anonymity-focused services, and $490m via cross-chain bridges.
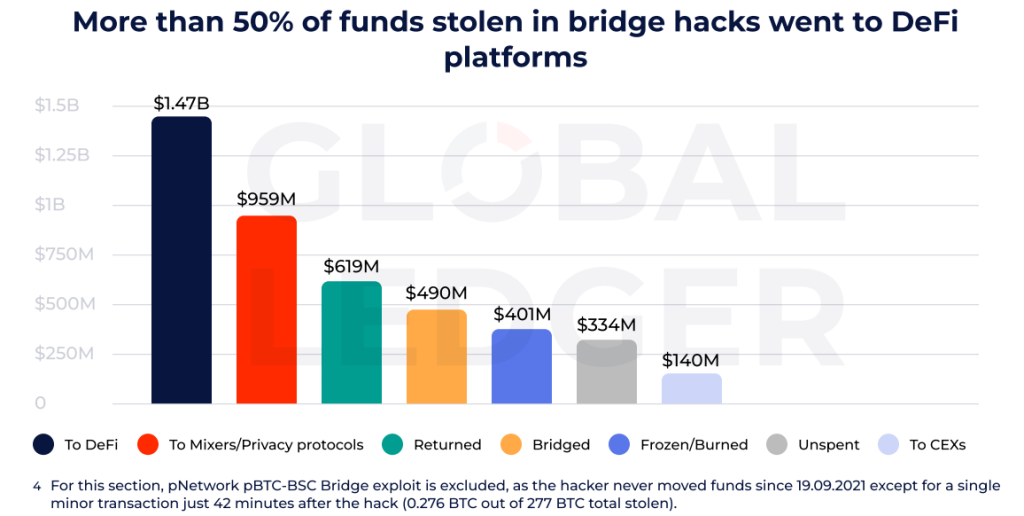
Of the stolen funds, some were returned while others are gone for good:
- ~$619m was returned by hackers;
- ~$401m was frozen or burned;
- over $334m remained unspent at the time of writing, sitting in attacker-linked wallets.
“Given a reimbursement rate of ~1.5% and the splitting of fund flows across numerous endpoints, traditional post-incident response strategies have proved ineffective”, the report says.
Police dismantle a Khmelnytskyi crypto gang
On 15 October, the cyber police of Khmelnytskyi region reported the exposure of a group suspected of unlawfully seizing digital assets from citizens of Ukraine, Europe and the Middle East.
According to law enforcement, the perpetrators created a cryptocurrency and wooed investors via Telegram communities. They flaunted a lavish lifestyle and “profitable trading deals”, pushing victims to invest.

Once victims invested, the creators blocked access to the purchased assets.
The suspects laundered the proceeds through specialised anonymity services and converted them to cash.

Police identified five Ukrainian victims of the alleged fraud. Searches in Khmelnytskyi and Kyiv yielded equipment, hardware crypto wallets, draft notes corroborating criminal activity, and luxury cars.
The detainees face up to eight years in prison. The investigation is ongoing.
US seized $15bn in bitcoin from Cambodian group leader
According to a press release dated 14 October, the US Department of Justice seized 127,271 BTC worth ~$15bn from the head of Prince Group, Chen Zhi. The criminal organisation stole billions of dollars worldwide via fake cryptocurrency investments, known as “confidence fraud”.
Typically, perpetrators establish contact through social networks and dating sites, gain trust, then persuade victims to invest in sham projects. Instead of investing, the scammers move the funds to their own accounts.
According to court documents made public, since 2015 the Cambodian group Prince Group has operated more than 100 shell and holding companies in 30 countries. The organisation forced thousands of people to participate in fraudulent schemes and successfully evaded law enforcement.
The criminals also ran automated call centres that used millions of phone numbers.
“Prince Group carried out its schemes by engaging in human trafficking and forcing hundreds of workers to conduct fraudulent operations in compounds in Cambodia, often under threat of violence”, the press release says.
Such complexes included vast dormitories ringed with high walls and barbed wire, effectively functioning as forced-labour camps.
The group’s leader, Chen Zhi, also known as Vincent, remains at large. He personally bribed officials to stave off law enforcement, ran the camps and used violence against those held there.
Some of the stolen funds paid for luxury travel, high-end purchases and costly assets — yachts, private jets, villas and a Picasso painting bought at a New York auction.
Developer extensions are growing more dangerous
A cybercriminal using the handle TigerJack is persistently targeting developers by publishing malicious extensions on the Microsoft Visual Code (VSCode) marketplace and the OpenVSX registry to steal digital assets and plant backdoors, researchers at Koi Security reported.
Two extensions removed from VSCode after 17,000 downloads are still available on OpenVSX. What is more, TigerJack republishes the same malicious code under new names on the VSCode marketplace.
The two extensions removed from VSCode — C++ Playground and HTTP Format — were reintroduced on the platform via new accounts.
When launched, C++ Playground registers a listener for C++ files to exfiltrate source code to several external endpoints. The listener triggers roughly 500 milliseconds after edits, capturing keystrokes nearly in real time.
According to Koi Security, HTTP Format works as advertised but secretly launches a CoinIMP miner in the background, using hard-coded credentials and configuration to mine cryptocurrency. The miner appears to impose no resource limits, harnessing all available compute.
Another category of TigerJack’s extensions retrieves JavaScript from a hard-coded address and executes it on the host. The remote address is polled every 20 minutes, enabling arbitrary code execution without updating the extension itself.
Researchers note that, unlike the source-code stealer and the cryptominer, this third type is far more threatening due to its broader capabilities:
“TigerJack can dynamically inject any malicious payload without updating the extension — steal credentials and API keys, deploy ransomware, use compromised developer machines as footholds into corporate networks, plant backdoors in your projects or monitor your activity in real time”.
At the time of writing, OpenVSX administrators had not contacted Koi Security. The two extensions remain available for download.
Also on ForkLog:
- A wallet of the hacked LuBian pool moved 9,757 BTC after three years of ‘hibernation’.
- Satellite communications lacked encryption — scientists intercepted military data.
What to read this weekend?
“Copyleft” — a way to preserve software freedom in an era of pervasive commercialisation. Read about its creator, Richard Stallman, in a new ForkLog feature.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


