
Atlas AI browser flaw, Wi‑Fi spying and other cybersecurity developments
This week’s key cybersecurity news: DeFi hack, AI browser flaw, LinkedIn phishing, Wi‑Fi tracking.
We gathered the week’s most important cybersecurity news.
- Hackers attacked a BTCFi protocol suspected of laundering assets stolen from Bybit.
- Crypto-fraud ring dismantled in Ukraine’s Vinnytsia region.
- A critical flaw was found in the Atlas AI browser.
- Hackers used LinkedIn for phishing.
Hackers attacked a BTCFi protocol suspected of laundering assets stolen from Bybit
The BTCFi protocol Garden Finance likely suffered a cross-chain exploit worth over $10.8 million, said on-chain sleuth ZachXBT.
Earlier, the expert indicated that the project might have been involved in laundering funds stolen in the hacks of Bybit and Swissborg.
I sincerely hope a government puts your team in prison with Diddy next cycle for ignoring victims like Bybit after >25% funds bridged are stolen funds
— ZachXBT (@zachxbt) October 28, 2025
“Ironically, just a few days ago I wrote on X that Garden Finance was ignoring victims, refusing to refund fees, although more than 25% of all their activity was tied to stolen funds,” the analyst noted.
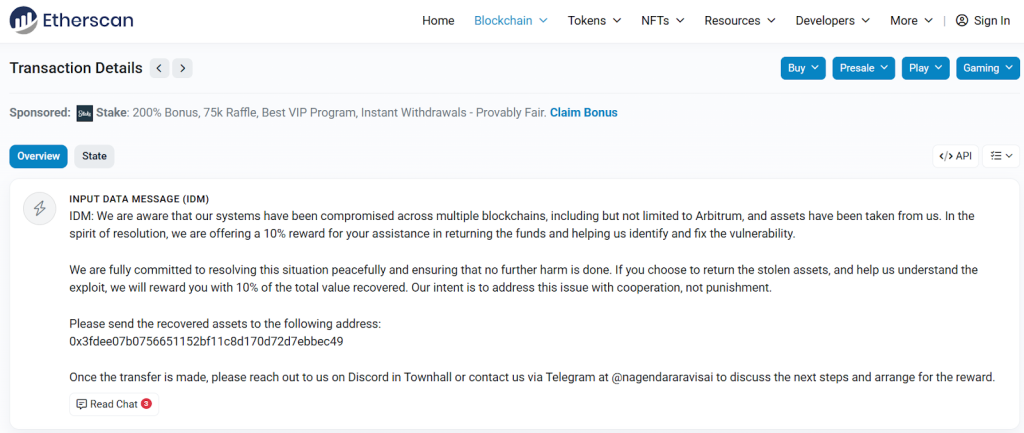
An address linked to the project’s team sent an on-chain message to the suspected hacker, offering a 10% bounty on the stolen funds.
Crypto-fraud ring dismantled in Ukraine’s Vinnytsia region
Ukraine’s Cyber Police, together with the Vinnytsia regional police and the SBU, exposed the organisers of a cryptocurrency scam.
According to law enforcement, two local residents used Telegram channels to advertise digital-asset exchanges and “legality checks”. Using social-engineering methods, they appropriated victims’ funds.
Victims included a German national, from whom the suspects stole 60,000 USDT.

Searches seized about $60,000 in cash, 48,000 hryvnias, two cars, computer equipment, bank and SIM cards, rough notes and other physical evidence. The pre-trial investigation continues.
A critical vulnerability was found in the Atlas AI browser
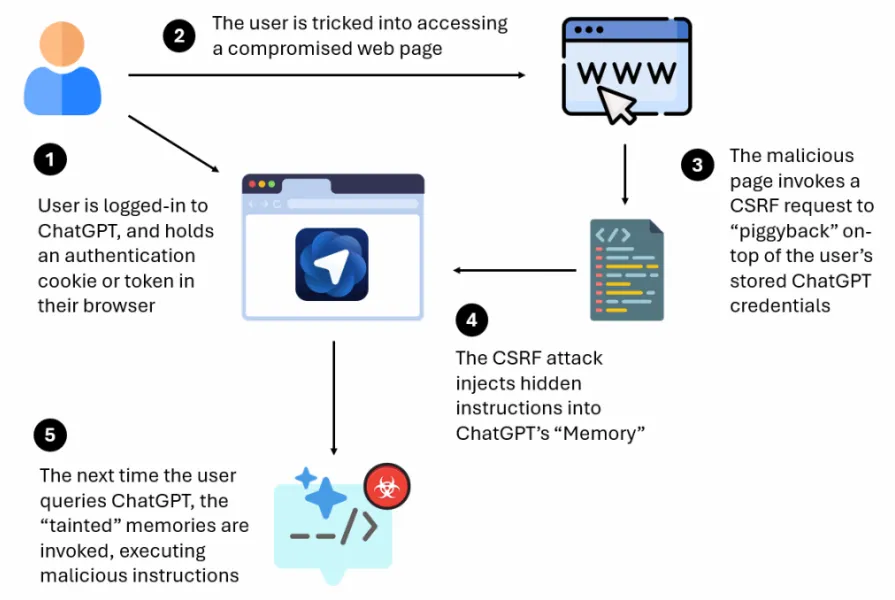
On October 27, researchers from LayerX discovered a critical vulnerability in the new Atlas AI browser from OpenAI. It allows attackers to inject malicious instructions into ChatGPT’s memory and execute arbitrary code.
The flaw exploits a cross-site request forgery mechanism (CSRF). An attacker can force a victim’s browser, already authenticated to ChatGPT, to send a hidden request that alters the bot’s internal memory. On subsequent interactions the infected instructions activate and may grant control over the victim’s account, browser or system.
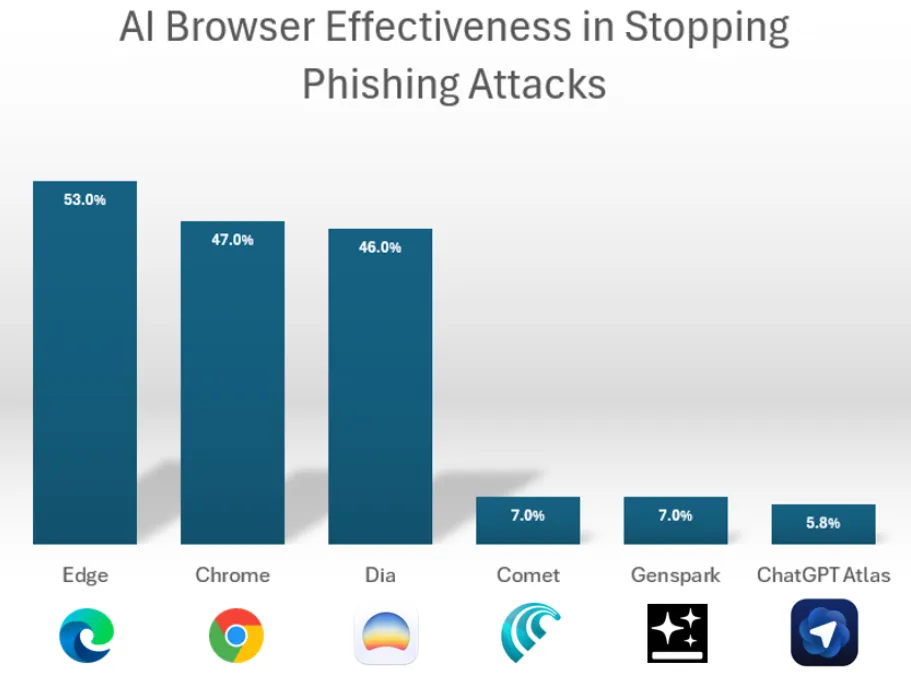
“Prompt injection” is particularly dangerous with Atlas: the browser keeps the user in a constantly authenticated session and has almost no built-in anti-phishing protections. In tests, Atlas blocked only about 5.8% of phishing attacks, whereas Chrome and Edge blocked roughly 50%.
According to the analysts, the bug affects not only Atlas but other browsers with access to ChatGPT. The infected memory remains tied to the account and can “follow” the user across devices and software.
Hackers used LinkedIn for phishing campaigns
Hackers have started using LinkedIn to conduct phishing attacks targeting executives at financial firms, researchers at Push Security reported on their blog.
Fraudsters send direct messages that mimic invitations to join the board of an investment fund, in order to trick victims into revealing their Microsoft credentials.
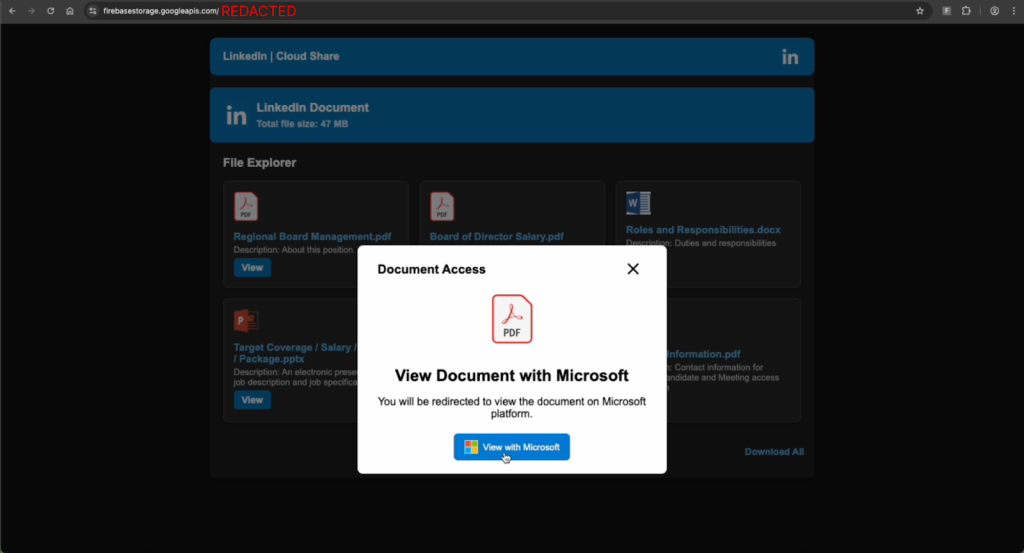
Following the link triggers a chain of redirects. When a fake site opens, supposedly hosting documents on board duties, the victim is prompted to click the View with Microsoft button. After a Cloudflare CAPTCHA, a spoofed login page appears to steal usernames and passwords.
Researchers demonstrated a neat way to identify people via Wi‑Fi signals
A German cybersecurity group at KASTEL Security Research Labs discovered a new method of identifying a person by intercepting Wi‑Fi traffic — BFId.
In an experiment involving 197 people, the attack showed high accuracy — 99.5%.
To scan a person’s gait, the system analyses unique distortions in Wi‑Fi signals. It factors in rhythm, speed and body movement, then creates a unique “radio-frequency identity fingerprint”.
According to the specialists, the BFId attack successfully identifies people even when gait style changes, when a backpack is worn or when the pace quickens.
The issue lies in the very principle of the beamforming feedback (BFI) mechanism — a standard Wi‑Fi 5 technology designed to improve network performance. The signal is transmitted back to the access point in broadcast, unencrypted form. The problem is present in Wi‑Fi 5 and Wi‑Fi 6 and very likely persists in the latest Wi‑Fi 7.
The experts noted that there is currently no simple and reliable protection.
A Microsoft Copilot Studio flaw allowed credential theft
Researchers at Datadog Security Labs reported a new phishing scheme called CoPhish. It uses legitimate Microsoft Copilot Studio services to steal credentials.
Scammers create fake Copilot agents and send links leading to spoofed login pages.
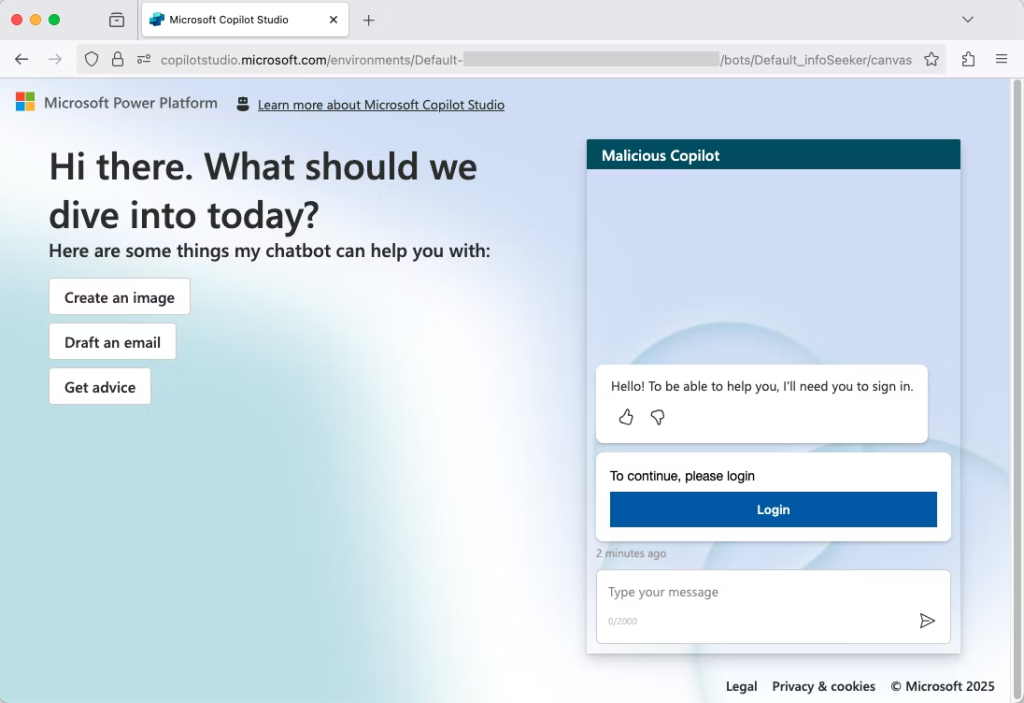
In a comment to Bleeping Computer, Microsoft acknowledged the issue and promised to fix the vulnerability in future updates. The company notes the attack relies on social engineering. Microsoft urges limiting administrator rights on devices and scrutinising access requests.
Datadog recommended that organisations disable the creation of user applications, tighten OAuth access policies and monitor the creation of agents in Copilot Studio to prevent similar attacks.
Also on ForkLog:
- The 402bridge protocol lost more than 17,000 USDC.
- Mysten Labs: AI in the hands of North Korean hackers has become more dangerous than quantum computing.
- Mt. Gox postponed creditor payouts until October 2026.
What to read this weekend?
The world is inexorably digitising; it is still not too late to turn to decentralised systems of digital identity, though that brings other pitfalls, as ForkLog has learned. Read our new piece on the past, present and possible future of digital IDs.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


