
Crypto scammers held over €600m theft, lax Louvre security and other cybersecurity news
The week’s key cybersecurity news.
We have compiled the week’s most important cybersecurity news.
- Police arrested crypto scammers suspected of stealing €600 million.
- North Korea’s financial network is now under sanctions.
- Charges filed against suspects in the JPEX crypto exchange case.
- Crime networks that stole $344 million across 193 countries were dismantled.
Police arrest crypto scammers suspected of stealing €600 million
European law enforcement arrested nine alleged members of a network that stole more than €600 million from victims in multiple countries, according to a press release from Eurojust.
The scammers built sham investment platforms that mimicked legitimate crypto services and promised “clients” high returns. They lured targets via social media, phone calls and advertising. Once funds were transferred, users lost access to their cryptocurrency.
Raids on 27 and 29 October in Spain, Germany and Cyprus led to arrests on charges including participation in laundering proceeds of fraud. Authorities seized €800,000 in bank accounts, €415,000 in cryptocurrency and €300,000 in cash.
North Korea’s financial network comes under sanctions
On 4 November the US Treasury announced sanctions against North Korea’s global financial institutions and associated individuals.
They are accused of laundering proceeds from illicit activity, including cybercrime and fraud. The authorities say the funds directly finance weapons-of-mass-destruction programmes and ballistic-missile production.
Those listed include two North Korean bankers who helped manage funds, including about $5.3 million in cryptocurrency, through Cheil Credit Bank. In addition, OFAC sanctioned foreign representatives of North Korean banks, including senior staff at Koryo Commercial Bank, Ryugyong Commercial Bank, the Foreign Trade Bank and the DPRK central bank.
Some are linked to a ransomware group that targeted US companies and laundered proceeds from overseas IT-worker operations.
According to TRM Labs, the 53 listed crypto addresses hold more than $5.4 million in total. Most of the USDT was frozen during a large-scale freeze carried out by Tether in April–May 2025.
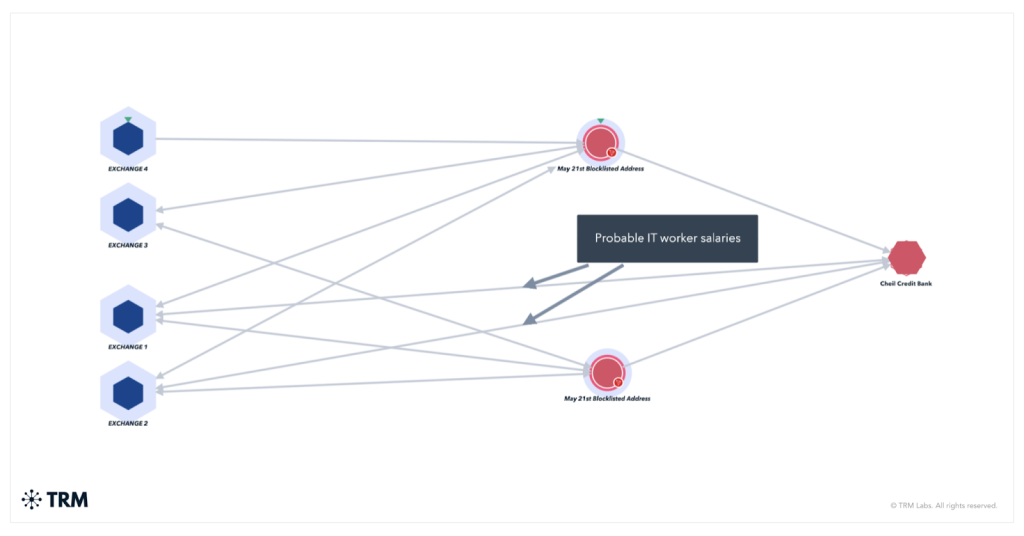
Addresses linked to Cheil Bank show regular payroll-like transactions, likely reflecting income of IT specialists working abroad under false identities. Between June 2023 and May 2025, wallets controlled by Cheil received more than $12.7 million.
The US Treasury says North Korea has stolen more than $3 billion over the past three years, mostly in cryptocurrency, using sophisticated cyberattacks. TRM Labs estimates that in 2025 alone DPRK-linked hackers stole $2.7 billion, chiefly thanks to the record Bybit exchange hack in February.
Hong Kong charges suspects in JPEX crypto exchange case
Hong Kong authorities have charged 16 people, including former lawyer and influencer Joseph Lam, in connection with the scandal around the JPEX crypto exchange. The news was reported by the South China Morning Post.
In April 2024, 72 people were arrested on suspicion of fraud linked to the trading platform. JPEX ran a crypto-trading venue without a licence, misleading customers by presenting itself as a legitimate exchange.
Investigators say the platform’s operators defrauded more than 2,700 investors of HK$1.6 billion (about $205.8 million).
Media reports describe it as Hong Kong’s largest financial fraud case. Six suspects were core JPEX team members; another seven, including Lam, were influencers or over-the-counter crypto dealers. Interpol issued red notices for three fugitives who, according to investigators, played a central role.
Crime networks that stole $344 million in 193 countries dismantled
According to Europol, an international operation dismantled three criminal networks whose activities focused on stealing from credit cards and laundering money, causing total losses of roughly $344 million.
On 4 November investigators from nine countries conducted a joint operation targeting 44 suspects, including alleged network operators, payment-service providers, intermediaries and a risk manager. Eighteen people were arrested, among them five executives of four German companies.
💳 Three criminal networks suspected of misusing credit card data from cardholders across 193 countries; 18 suspects arrested.
Read more in our press release: https://t.co/Qb0cegnUF1 pic.twitter.com/SWTdN4D0sI
— Europol (@Europol) November 5, 2025
Between 2016 and 2021, the suspects allegedly used stolen data to create more than 19 million fake subscriptions on porn sites, dating services and streaming platforms. The monthly charges were relatively small — about $58 — and accompanied by vague descriptions.
To conceal the activity, the fraudsters used numerous shell companies, mostly registered in the UK and Cyprus, leveraging Crime-as-a-Service infrastructure. More than 4.3 million users in 193 countries were affected.
Following 29 searches in Germany, authorities seized more than $40 million in assets, including luxury cars, cryptocurrency, laptops and mobile phones.
Libération: years of lax security at the Louvre
The Louvre’s cybersecurity was weak, and major system failures went unaddressed for years — failings likely exploited in the recent robbery — according to an investigation by the French newspaper Libération.
Reporters say that as early as 2014 specialists from the national cybersecurity agency identified vulnerabilities at the museum.

During an audit, experts penetrated the Louvre’s network from ordinary office computers. They were able to damage the CCTV system remotely and alter access rights on passes.
Passwords for security systems also made breaches easier. Journalists learned that in 2014 the password required to access the server managing video surveillance was “Louvre.”
In 2015 the museum commissioned a second audit that lasted a year and a half. A report marked confidential, prepared in 2017 and reviewed by the journalists, again rated the museum’s defences inadequate. Louvre management was advised to rotate passwords more frequently and not to neglect antivirus updates.
Having reviewed technical documents provided by the museum between 2019 and 2025, the investigators noted that some issues remained unresolved after eight years. This affected at least eight programs controlling video surveillance, access management and servers. A 2021 document also stated that Sathi software ran on Windows Server 2003, which Microsoft stopped supporting in 2015.
According to Libération, in early 2025 Paris police began a new security audit of the museum and, in particular, its control centres. Neither the Louvre, nor the police prefecture, nor France’s Ministry of Culture commented on the investigation.
Also on ForkLog:
- The Balancer team identified the cause of the $128 million hack.
- A researcher uncovered an undisclosed $44 million DWF Labs hack.
- The founders of Samourai Wallet were charged with deliberate money laundering.
- Experts estimated collateral damage from the Stream Finance hack.
- Russians complained about account blocks at Bybit EU and Revolut.
What to read this weekend?
From early HTML-era initiatives and experiments of the 1990s to the new x402 standard. In a new feature, ForkLog examines the history of internet micropayments.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


