
Losses from crypto hacks reached $3.4bn in 2025
Over $2bn was attributed to North Korean hackers
From January to early December 2025, hackers stole cryptocurrencies worth more than $3.4bn, slightly above last year’s $3.3bn, according to Chainalysis.
1/ In the first preview chapter of our 2026 Crypto Crime Report, we look at how North Korean hackers stole $2.02B in crypto during 2025, a 51% increase from 2024, pushing their all-time total to $6.75B: https://t.co/B9l4x1g9VM
— Chainalysis (@chainalysis) December 18, 2025
Almost half of all losses — 44%, or $1.5bn — stemmed from the the Bybit exchange hack.
Analysts observed a record skew in the data: for the first time, the gap between the largest attack and the average incident exceeded 1,000-fold.
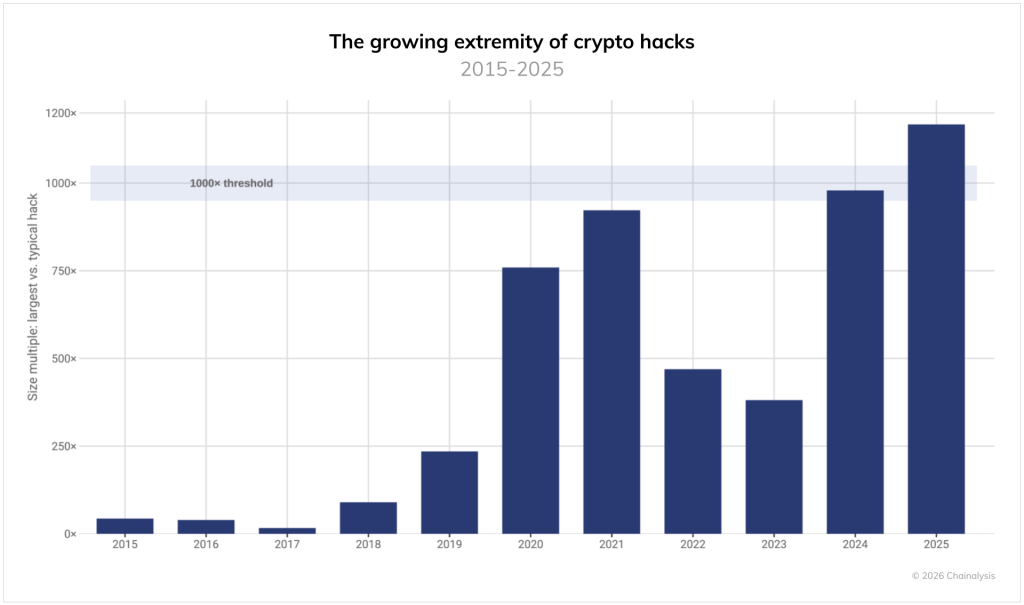
“The amount stolen in top-tier attacks is now a thousand times larger than in an ordinary theft, surpassing even the peak figures of the 2021 bull market,” they explained.
Another notable trend is the rise in personal wallet breaches and key thefts at centralized services. The share of such incidents climbed from 7.3% in 2022 to 44% in 2024.
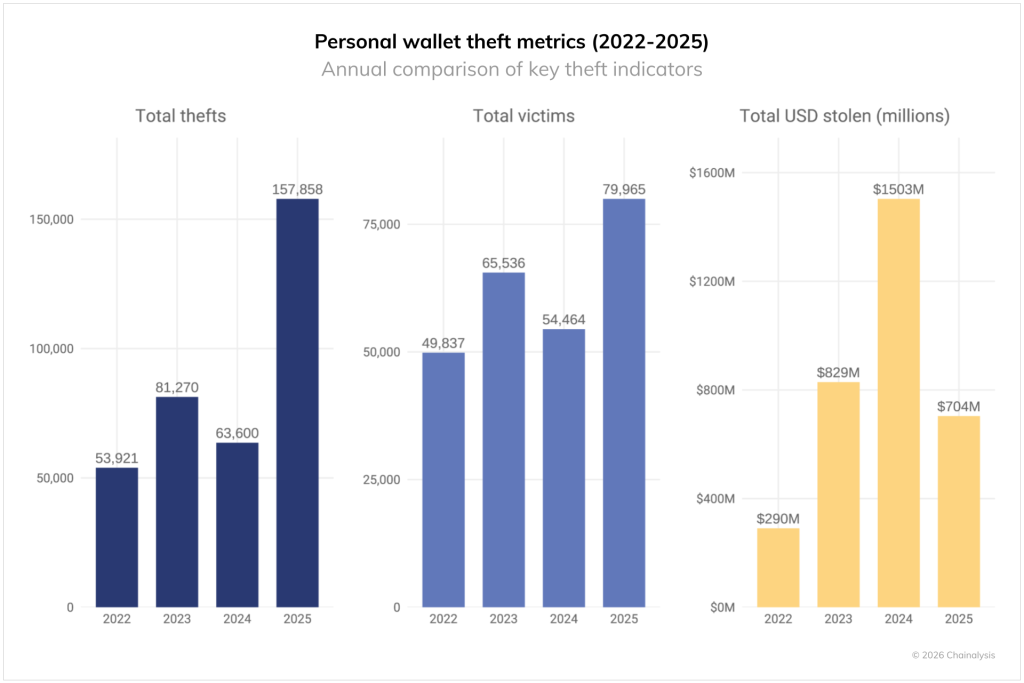
There were 158,000 incidents affecting at least 80,000 unique addresses. Aggregate losses fell from $1.5bn to $713m.
Experts noted that attackers are now going after a larger number of victims but for smaller sums.
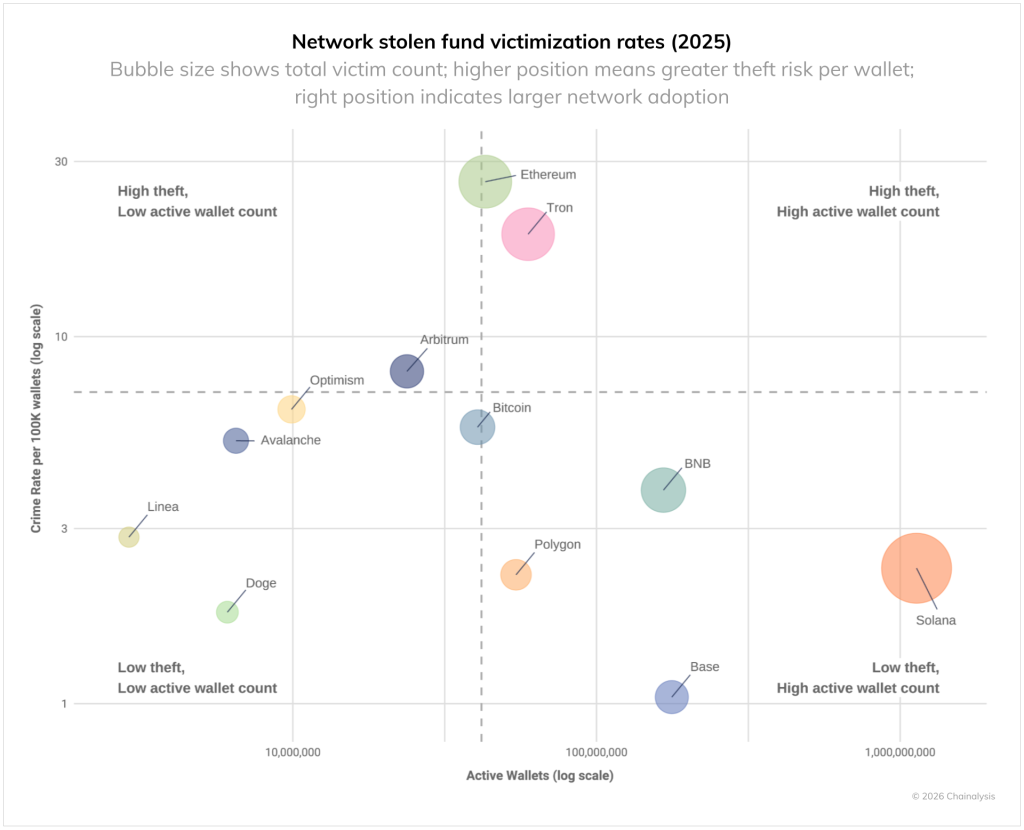
The highest attack density per 100,000 wallets is seen on the Ethereum and Tron networks.
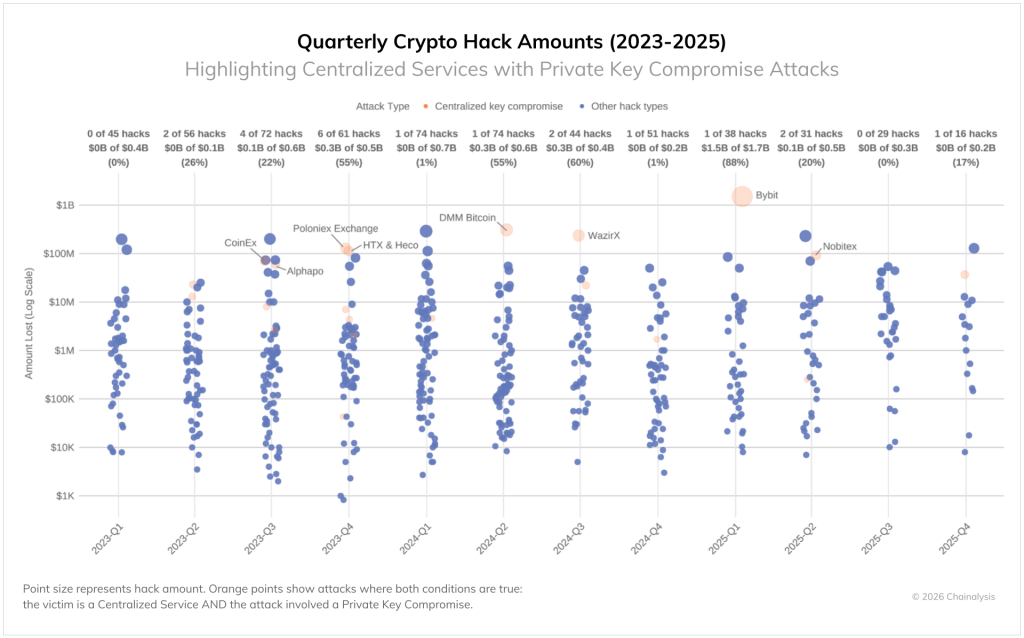
Despite professional security infrastructure, centralized services remain vulnerable. In the first quarter, such platforms accounted for 88% of all funds stolen. The main single point of failure is private keys.
Progress in DeFi
In 2025, losses from hacks in DeFi were low despite rising TVL. In Chainalysis’s view, the trend points to higher security standards across the sector.
The September incident at Venus Protocol was instructive. Thanks to monitoring by Hexagate, the team spotted suspicious activity 18 hours before the attack. Developers were able to pause the protocol and quickly recover funds.
Later, the community, via the DAO, froze a further $3m that was under the hacker’s control. As a result, the attacker made no profit and even incurred losses.
“Although attacks still occur, the ability to detect, respond to and even reverse them represents a fundamental shift from the early DeFi era, when successful hacks often meant irretrievable losses,” the specialists commented.
A record year for North Korea
North Korea set a new negative record, cementing its status as the chief threat to the crypto industry. In 2025, hackers stole at least $2.02bn — $681m more than in 2024.
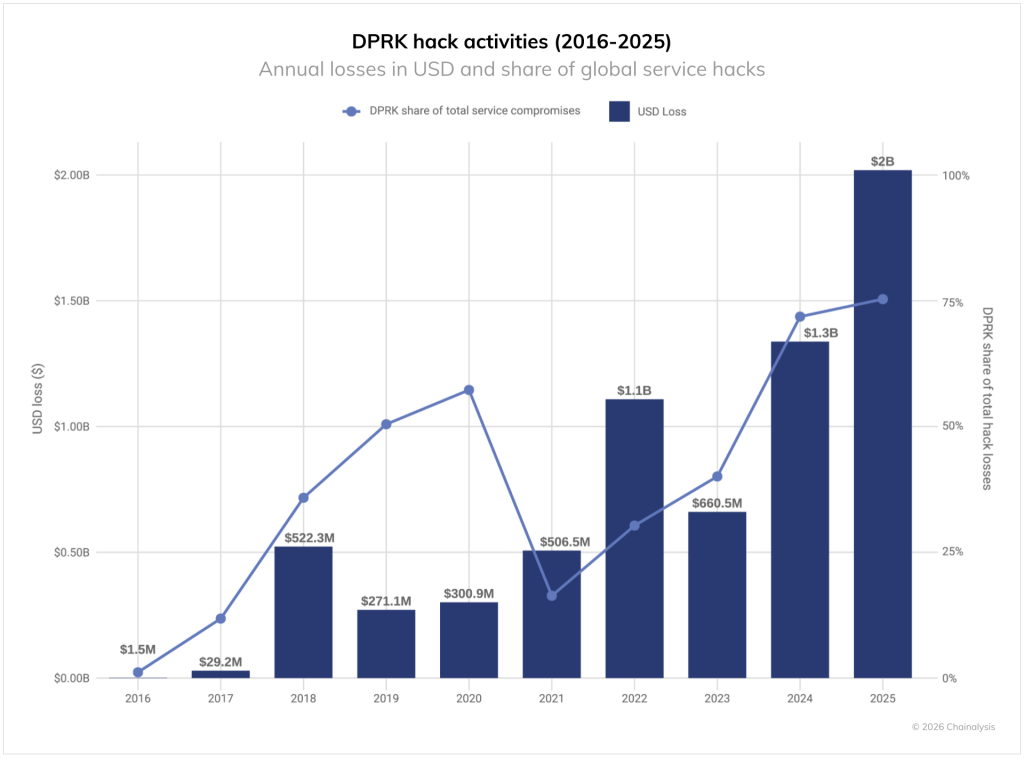
Cumulative losses attributed to DPRK hackers reached $6.75bn.
Experts said a key tactic remains the placement of fake IT workers. After gaining access to projects’ internal infrastructure, they steal funds. In May, one such spy was identified by the Kraken exchange team.
In September, Binance founder Changpeng Zhao warned about this threat.
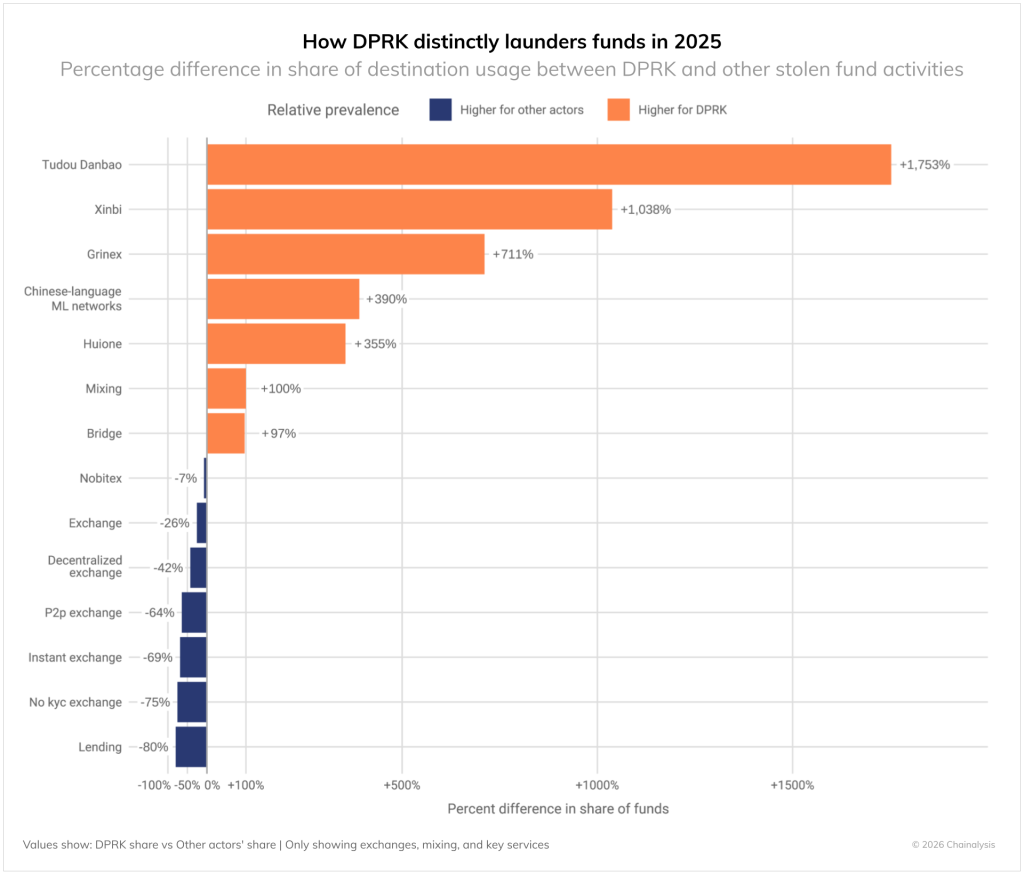
Analysts also highlighted North Korean groups’ laundering patterns. Unlike other cybercriminals, they split large sums into tranches of less than $500,000.
DPRK actors also prefer Chinese-language services, bridges, mixers and specialised platforms such as Huione. Most other hackers more often opt for lending protocols, exchanges without KYC and P2P platforms.
North Korean hackers follow a well-rehearsed playbook that typically spans about 45 days:
- Within the first five days, they rush assets through mixers and DeFi protocols to break links to the theft site.
- From the second week, funds are redistributed via DEX and bridges to prepare for cash-out.
- Days 20–45: they use unregulated Chinese-language services and other platforms to convert to fiat.
“North Korea continues to use cryptocurrency theft to fund state priorities and evade international sanctions. The industry must recognize that this actor plays by different rules than typical cybercriminals. The task for 2026 is to detect and prevent these highly efficient operations before DPRK actors inflict damage comparable to the Bybit incident,” Chainalysis said.
Mysten Labs cryptographer Kostas Chalkias believes artificial intelligence in the hands of North Korean hackers is a more serious threat than quantum computers.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


