
Spotify’s expropriation, a crypto wallet–targeting stealer, and other cybersecurity news
The week’s key cybersecurity developments.
We have gathered the week’s most important cybersecurity news.
- Researchers found a new, feature-rich cryptocurrency stealer.
- Chrome extensions intercepted user traffic for eight years.
- Activists “backed up” 86 million Spotify audio files.
- Uzbekistan’s traffic-management database was left without a password.
Researchers uncover a new crypto stealer with broad capabilities
Experts at Kaspersky reported a new stealer, Stealka. The malware, which targets Windows users, can steal data and cryptocurrency, hijack accounts and install hidden miners.
According to analysts, the software most often masquerades as cracks, cheats and mods. The malware is triggered manually by the victim and spreads via popular platforms such as GitHub, SourceForge, Softpedia and Google Sites.
In more elaborate schemes, attackers create convincing copies of websites by tapping into popular search queries. Mimicking trusted resources, the interface tells users that all posted data have been fully scanned for viruses.
Stealka offers a broad arsenal, but its primary target is user data from Chromium- and Gecko-based browsers, including popular Chrome, Firefox, Opera, Yandex Browser, Edge and Brave.
Attackers are most interested in autofill stores containing account information and payment-card details. Cookies and session tokens let hackers bypass two-factor authentication to seize accounts, which are then used to spread the malware further.
According to Kaspersky, Stealka targets 115 browser extensions. Popular categories at risk include:
- crypto wallets: Binance, Coinbase, Crypto.com, SafePal, Trust Wallet, MetaMask, Ton, Phantom, Exodus;
- two-factor authentication apps: Authy, Google Authenticator, Bitwarden;
- password managers: 1Password, Bitwarden, LastPass, KeePassXC, NordPass.
The stealer also threatens messengers, mail clients, note managers, gaming services and VPNs.
Chrome extensions intercepted user traffic for eight years
Two Chrome Web Store extensions called Phantom Shuttle pose as proxy-service plug-ins but in fact intercept user traffic and steal confidential data, Socket reported.
Phantom Shuttle targets users in China, including foreign-trade professionals who need to test network connections from various locations inside the country. Both extensions are published under the same developer and marketed as tools for traffic proxying and speed testing. They are available by subscription priced from $1.4 to $13.5.
Active since 2017, the software routes a user’s web traffic through attacker-controlled proxy servers, accessed using hard-coded credentials. Malicious code is embedded inside a legitimate jQuery library.
By “listening” to web traffic, the extensions can intercept HTTP authentication requests on every site visited. They dynamically reconfigure Chrome’s proxy settings using a proxy auto-configuration script.
In the Default mode the malware can filter more than 170 domains, including:
- developer platforms;
- cloud-service management consoles;
- social networks;
- adult-content portals.
Local networks and the control domain are whitelisted to avoid disruption and detection.
Operating as a man-in-the-middle attack, the extension can:
- intercept data from any forms (logins, card details, passwords, personal information);
- steal session cookies from HTTP headers;
- extract API tokens from requests.
Activists “backed up” 86 million Spotify audio files
The leading music-streaming service was subjected to mass scraping by pirate activists from Anna’s Archive.
The group is widely known for a campaign to preserve literature, scientific publications, magazines and other materials. They call themselves “the largest truly open library in human history”, providing access to more than 61 million books and 95 million articles.
In a 20 December 2025 post, “Backing up Spotify”, the team claims it obtained access to metadata for more than 250 million tracks and 86 million of the service’s audio files.
The haul amounts to about 300 TB. The most-played tracks, per Spotify’s metrics, are available at 160 kbps, while less popular ones are compressed to 75 kbps.
Anna’s Archive says the move allowed it to create “the world’s first archive for music”. Activists claim it covers 99.6% of all listens on Spotify.
The group has posted the metadata on its torrent site and plans to release the audio files later. Additional metadata and album art will follow. The archive will be published in order of popularity.
On December 21 a Spotify team told Billboard the scraping had been confirmed:
“The investigation of unauthorized access showed that a third party collected public metadata and used illegal methods to circumvent technical copyright-protection measures to gain access to part of the platform’s audio files.”
On December 23 a Spotify spokesperson told PCMag of “detecting and blocking the accounts of the malicious actors involved in the unlawful data collection”.
Uzbekistan’s traffic-management system database was left without a password
Security researchers uncovered a critical data leak in Uzbekistan’s national road-traffic monitoring system. A network of a hundred high-resolution cameras using facial and licence-plate recognition had been openly accessible for an extended period without a password.
According to Anurag Sen, the researcher who found the vulnerability, the “intelligent traffic-management” database contains millions of photos and raw 4K video recordings. These can be used to reconstruct citizens’ routes.
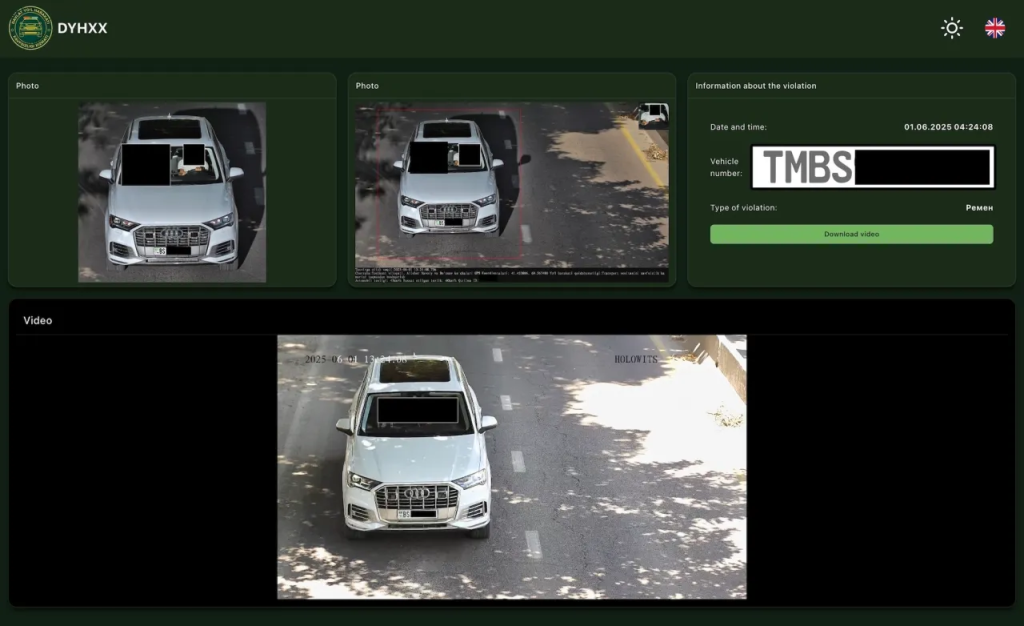
For example, one driver was tracked for half a year: cameras logged his trips between Tashkent and nearby settlements several times a week.
The system is built on equipment from China’s Maxvision and Singapore’s Holowits. Beyond recording traffic violations, the algorithms can identify drivers and passengers in real time. Cameras are deployed not only in large cities such as Jizzakh and Namangan but also at strategically important border sections.
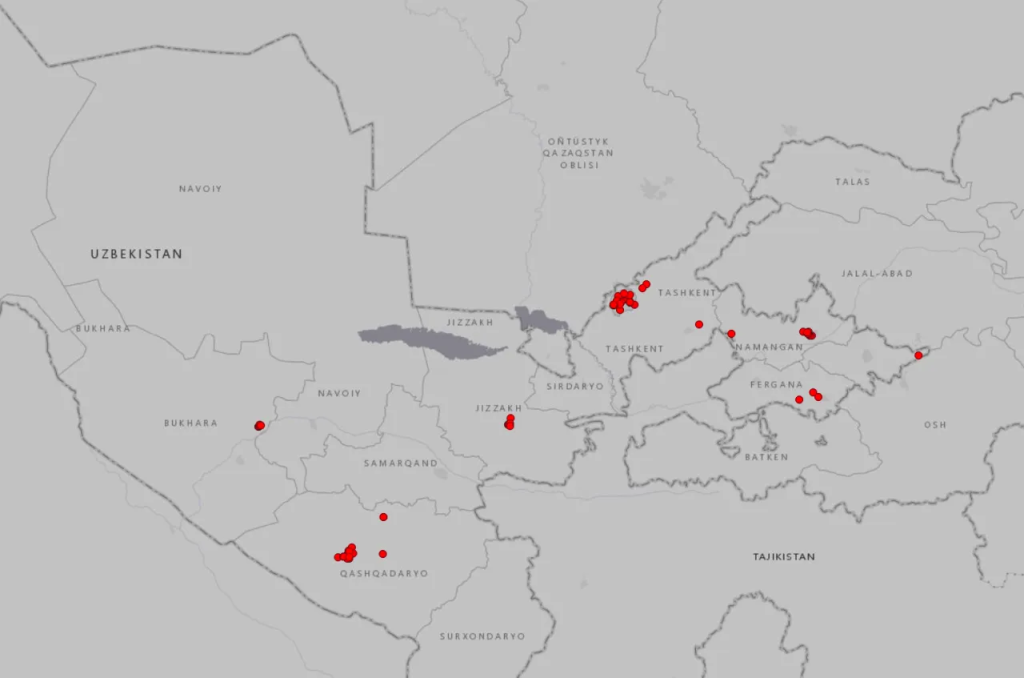
Despite the scale of the leak, government agencies, including the Interior Ministry and the UZCERT incident-response team, had not closed access to the data or issued official comments at the time of publication.
The incident echoes recent problems at an American surveillance giant — Flock. Earlier it was reported that in the US dozens from this supplier also ended up accessible online without authorization.
Leaks of this scale pose serious privacy risks, allowing criminals to exploit state infrastructure for stalking and the theft of personal data.
Interpol carried out sweeping raids in Africa
During Operation Sentinel in Africa, coordinated by Interpol, law-enforcement officers arrested 574 people and recovered $3 million linked to business email compromise and ransomware.
From October 27 to November 27, 2025, police in 19 countries took down about 6,000 malicious links and decrypted six ransomware variants. Financial losses from cybercriminals’ actions totalled more than $21 million.
Operation Sentinel highlights:
- Senegal: a $7.9 million transfer was prevented in an attack on an oil company;
- Ghana: after a loss of $120,000 and the encryption of 100 TB at an unnamed financial institution due to a ransomware attack, police restored 30 TB of data and made numerous arrests;
- Ghana, Nigeria: a cross-border scam impersonating well-known fast-food brands deceived more than 200 victims out of roughly $400,000. Police detained ten suspects, seized over 100 devices and disabled 30 servers;
- Benin: 106 arrests, removal of 43 malicious domains and blocking of 4,318 social-media accounts linked to fraud;
- Cameroon: rapid action against an online car-sales scheme traced a compromised server and secured the emergency freezing of bank accounts within hours.

Private companies also took part in the investigation: Team Cymru, The Shadowserver Foundation, Trend Micro, TRM Labs and Uppsala Security.
The teams helped trace IP addresses used in ransomware attacks and sextortion cases, and helped freeze criminal proceeds.
Also on ForkLog:
- Trust Wallet users were hacked for $7 million.
- CZ proposed a way to combat “address poisoning”.
- AI was used to forge documents for works of art.
- Polymarket reported a breach of user accounts.
- Media reported that Chinese darknet turnover on Telegram rose to $2 billion.
- “Prompt injection” has become the chief hazard for AI browsers.
- An investor lost nearly $50 million in an address-substitution attack.
What to read this weekend?
The safety of investment capital often hinges on measured decisions, typically justified with expert reports. ForkLog revisited top analysts’ forecasts for 2025 and compared them with objective reality.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


