
Advertising tracking in Chrome, Roskomnadzor against WhatsApp, and other cybersecurity developments
Here are the week’s key cybersecurity headlines.
- Experts have identified a new alternative to the LockBit ransomware.
- Google has started tracking browser history for advertising purposes.
- Roskomnadzor did not rule out blocking WhatsApp in Russia.
- Meduza editor targeted with Pegasus spyware.
Experts have identified a new alternative to the LockBit ransomware
The attackers have started using a new ransomware called 3AM in cases where deploying LockBit in the target network is not possible, according to analysts at Symantec Threat Hunter.
The malware is written in Rust and is not linked to any known ransomware family, making it a completely new strain of malware.
Before an attack, 3AM resets system policy configurations for a specific user. The ransomware also attempts to stop services and products related to security and backups.
So far, 3AM attacks are rare. However, experts do not rule out that it may attract the attention of other attackers in the future as an alternative to LockBit.
Google has started tracking browser history for advertising purposes
Google has added a new advertising platform in the latest Chrome update: Privacy Sandbox. It will monitor pages visited by users and assemble a list of advertising topics based on their interests.
A warning about the new tool appears on opening the browser. After that the advertising platform automatically enables.
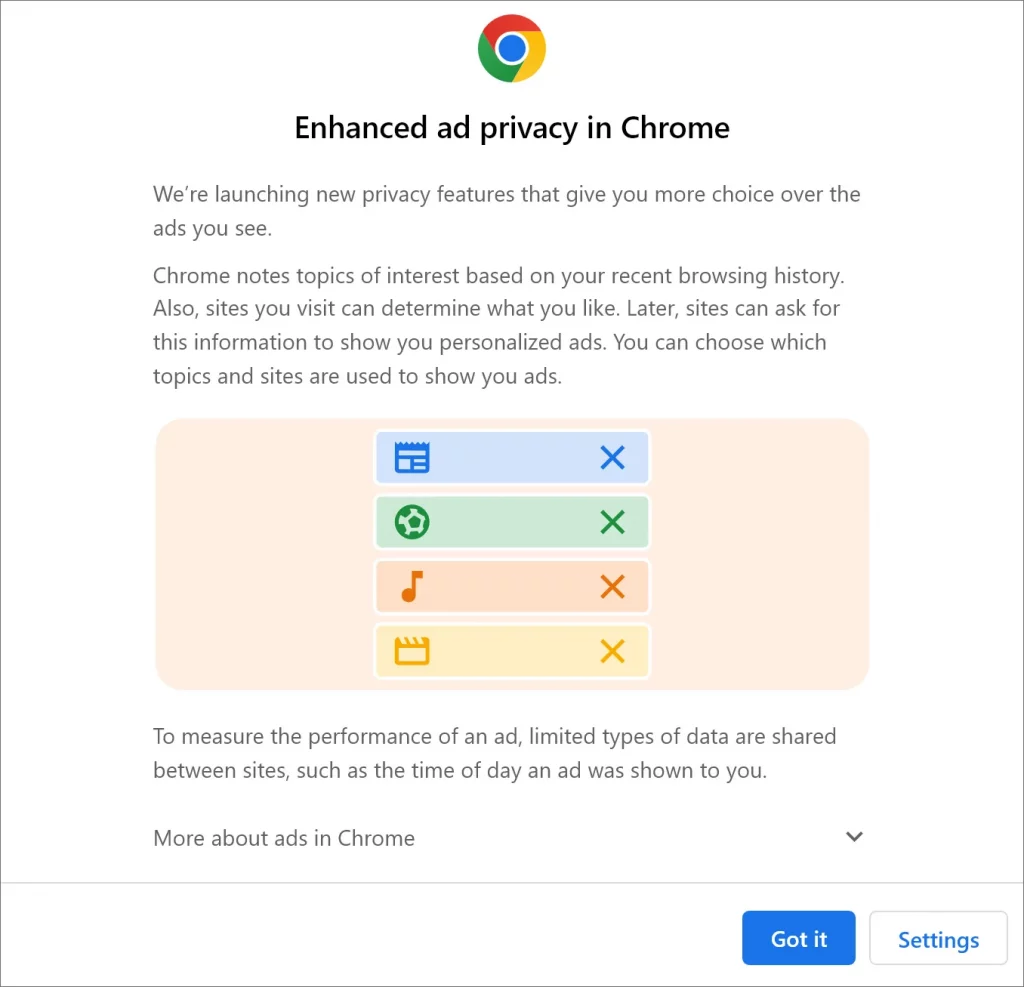
Privacy Sandbox testing will continue through 2024, and by the fourth quarter third-party cookies should be fully disabled by default.
In Russia, blocking WhatsApp was not ruled out
Roskomnadzor allowed blocking of WhatsApp on Russian territory if the service launches “unfriendly channels.” This was reported by Interfax.
The agency’s comment came soon after the company announced the launch of its Channels feature in 150 countries.
Roskomnadzor reminded that it would require the messenger to immediately delete any prohibited information, and if it refuses, it would be blocked.
«Enforcement measures for non-compliance with Russian law directly depend on the administrations of such companies and the decisions they make», the agency added.
Meduza editor targeted by Pegasus spyware
Meduza editor Galina Timchenko’s iPhone was infected with Pegasus spyware in February 2023, but the breach was only discovered at the end of June after Apple’s notification. The investigation was conducted by Access Now and Citizen Lab.
?BREAKING: Exiled media under attack!
Access Now and @citizenlab reveal first-time documented use of NSO Group’s Pegasus spyware against a Russian journalist — the head of @MeduzaProject Galina Timchenko.
Dive into our report: https://t.co/yDXxday4oe
— Access Now (@accessnow) September 13, 2023
The malware gives the hacker access to the device’s microphone, camera and memory on a smartphone with a SIM card inserted. Unknown attackers could access the phone’s full contents, including home address, meeting schedules, photos, and even conversations in encrypted messaging apps.
Countering Pegasus installation is nearly impossible. In Timchenko’s case, it is likely that vulnerable HomeKit and iMessage services were exploited.
At the time of infection, the journalist was in Germany, attending a confidential meeting of representatives of Russia’s independent media. Two weeks earlier, Meduza was designated an undesirable organization in Russia.
Pegasus is developed by the Israeli NSO Group. After analyzing Timchenko’s phone, researchers could not determine who was behind the infection. Among those suspected are the security services of Russia, Kazakhstan, Azerbaijan, Estonia, Germany or Latvia.
More than 60,000 Android users downloaded a malicious Telegram clone
Researchers at Kaspersky Lab have discovered in Google Play a number of malicious modifications of the Telegram messenger. They are promoted among Chinese users as a fast alternative to the standard app by using a distributed network of data centers.
Externally the clones resemble the original Telegram, but their code contains spyware features.
In particular, they gain access to the user’s contacts, name, ID, phone number, and message contents, which are sent to a command-and-control server.
The campaign affected more than 60,000 Android users.
As of writing, all identified malicious apps have been removed from Google Play, and their developers have been blocked.
Also on ForkLog:
- Tether froze $1.4 million of the $2.7 million stolen from the Remitano exchange.
- A former Celsius Network top executive pleaded guilty.
- About one third of the cryptocurrency stolen by North Korean hackers was obtained in two attacks.
- Sam Altman acknowledged issues with Worldcoin.
- The Bitzlato exchange increased the amount of Bitcoin available for withdrawal.
- In Ukraine, a pre-trial investigation has begun into crypto market participants.
- OneCoin co-founder was sentenced to 20 years in prison.
- The CoinEx exchange confirmed a hack of hot wallets, after detecting a “suspicious outflow” by PeckShield analysts. The attack was linked to Lazarus hackers, and users were promised 100% compensation.
- OKLink and CertiK will develop a standard for blocking stolen tokens.
- The Banana Gun Telegram bot team redeemed their own tokens due to a bug in the smart contract.
- Hackers hacked Vitalik Buterin’s X account by SIM swapping.
- Media: in Moscow, the creator of the fraudulent Bitcoin exchange Intelex was arrested.
- The trial of Vinnik has been postponed to September 2024, with the defendant’s lawyer allowing a guilty plea.
- In Thailand, those accused of orchestrating crypto fraud worth $27 million were arrested .
- The Poly Network hacker transferred 1500 ETH to Tornado Cash.
- Lido Finance did not confirm an exploit of LDO tokens.
- US authorities demanded $5.2 million in Bitcoin from a hacker.
What to read this weekend?
A representative of the NAP in Uzbekistan spoke about the regulator’s countermeasures against cybercrime in the cryptocurrency space.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


