
Android fingerprint brute-force, Meta’s record EU fine, and other cybersecurity headlines
We have gathered the week’s most important cybersecurity news.
- Meta fined in the EU $1.3 billion for sending user data to the United States.
- Experts uncovered a method to hack Android via fingerprint brute-forcing.
- The Inferno Drainer phishing service stole more than $5.9 million in cryptocurrencies.
- A ransomware attack hit a US government contractor.
Meta fined in the EU $1.3 billion for sending user data to the United States
The Irish Data Protection Commission imposed on Meta’s local subsidiary a record fine of $1.3 billion for privacy violations.
The regulator found that the company transfers user data from the EU to the United States, where privacy safeguards vary by state, and thus does not guarantee their security.
The Irish supervisory authority, which is the leading privacy regulator for the bloc of 27 countries, opened the investigation in August 2020.
Now Meta must stop transferring user data to the United States, bring it into line with the GDPR, and within six months delete all unlawfully stored and processed information.
Representatives of the company called the imposed fine unfair and intend to appeal the authorities’ decision.
Experts uncovered a method to hack Android via fingerprint brute-forcing
Some Android smartphones from Samsung, Xiaomi, OnePlus, Vivo, OPPO and Huawei were found vulnerable to fingerprint brute-forcing. The researchers from Tencent Labs and Zhejiang University report.
In the attack named BrutePrint the attacker generates a large number of fingerprint samples and matches them to the device’s sensor until a suitable one is found. As a result, they can gain access to the target device and all data stored on it.
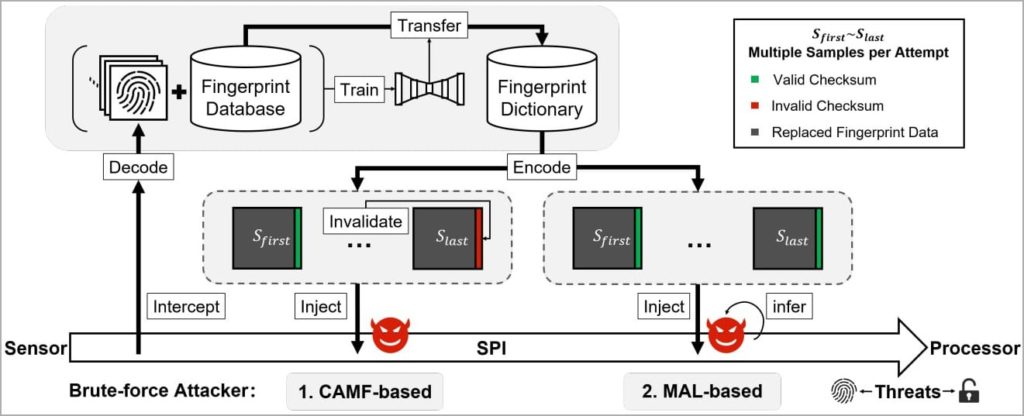
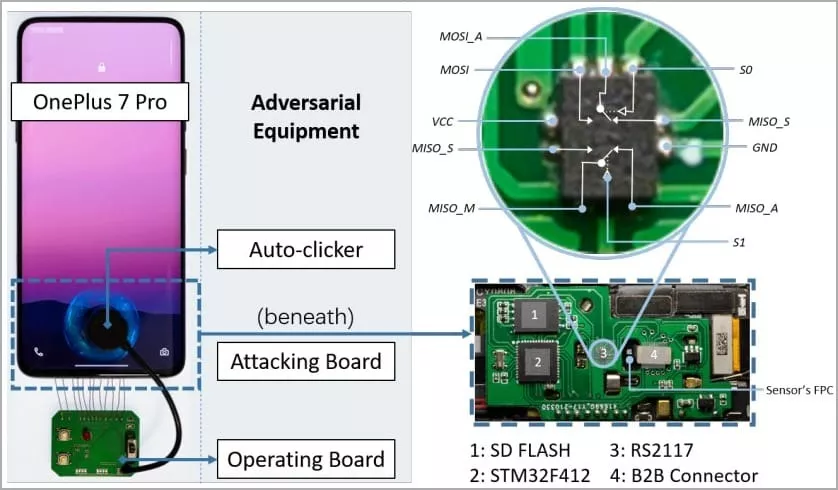
The attacker would need physical access to the device, a fingerprint database from academic datasets or biometric leaks, and equipment costing about $15 in total.
Android devices allow unlimited fingerprint attempts, so with enough time the attack would be successful.
The vulnerability stems from many manufacturers using standard fingerprint recognition algorithms. More advanced devices equipped with ultrasonic sensors are better protected.
Inferno Drainer phishing service stole more than $5.9 million in cryptocurrencies
Since March 27, the Inferno Drainer phishing service has stolen cryptocurrencies worth more than $5.9 million through at least 689 fake sites. Scam Sniffer reports.
Inferno Drainer is marketed as a multi-chain scam. Its creators provide clients with an administration panel that allows configuring phishing pages and even offer a trial version.
Pages created with Inferno Drainer imitate sites of 229 popular brands, including Pepe, MetaMask, OpenSea, Sui, zkSync and others.
As of the report, most assets ($4.3 million) were stolen from the Ethereum network, $790,000 from Arbitrum, $410,000 from Polygon and $390,000 from BNB Chain.
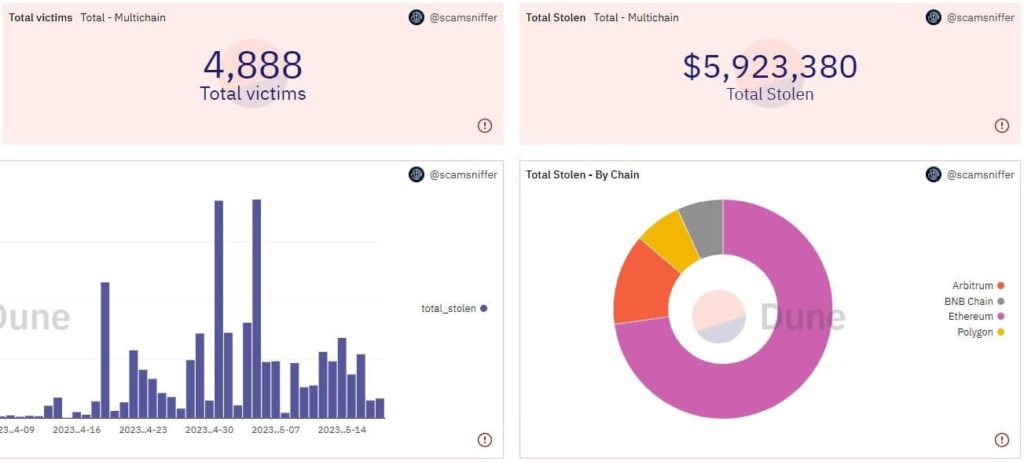
According to the researchers, the attackers split the proceeds from the attacks across five wallets.
A ransomware attack hit a US government contractor
The Swiss multinational technology company and US government contractor ABB confirmed the ransomware attack on some of its systems. The incident occurred on May 7.
The attackers managed to steal an undisclosed amount of data from compromised devices, but the company found no signs of impact on client systems.
ABB has contained the breach in its services and is taking additional security measures to protect the network. An investigation has been opened with law enforcement.
BleepingComputer reports that the attack was organized by hackers from the Black Basta group. They targeted the corporate Windows Active Directory and affected hundreds of Windows devices, according to company sources.
ABB designs industrial control, dispatch management and data collection systems for manufacturing and energy suppliers. Its clients include the US Department of Defense and federal civilian agencies, including the Departments of the Interior, Transport and Energy, as well as the Coast Guard and the U.S. Postal Service.
North Korean IT staffing firms behind the “army” of IT specialists hit with US sanctions
OFAC announced sanctions against four organizations and one individual from North Korea involved in cyberattacks and illicit IT income schemes.
The list includes:
- Pyongyang University of Automation;
- Technical Reconnaissance Bureau of the Reconnaissance General Bureau (RGB) of North Korea;
- Cyber Unit of the 110th Research Center;
- Chinyong Information Technology Cooperation;
- North Korean citizen Kim San-man.
According to OFAC, thousands of North Korean IT specialists are fraudulently placed in foreign companies . They intentionally conceal their identity and location, using proxy accounts, stolen personal data and forged documents .
Proceeds from their activities go to financing the North Korean missile and nuclear program.
Android app downloaded over 50,000 times turned into spyware
The Android screen-recording app iRecorder – Screen Recorder was trojanized a year after it appeared in the Google Play store, according to ESET.
In that time it had been downloaded more than 50,000 times.
The developer included within the update the malware RAT AhRat with code for a backdoor and a beacon to a command-and-control server.
The AhRat malware can track the location of infected devices, steal call logs, contacts and text messages, send SMS, record ambient sounds and take pictures.
At present the app has been removed from Google Play, but may still be available in unofficial Android app stores.
Also on ForkLog:
- The Tornado Cash developer to question Chainalysis by the court.
- A former Coinone pleaded guilty to bribery charges.
- A Coinbase lawyer challenged the sanctions against Tornado Cash.
- Binance paused deposits of 10 tokens amid Multichain issues.
- Elliptic: opioid shipments from China to the US are paid in Bitcoin.
- A video on YouTube showing the seed phrase breach of the Trezor T wallet.
- NBA star Shaquille O’Neal was again accused of promoting the collapsed FTX.
- The High Court of Montenegro refused to grant bail to Do Kwon.
- The DeFi project Fintoch was suspected of fraud totaling $31.6 million.
- In Kazakhstan, alleged organizers of the cryptocurrency pyramid MetaGo were identified.
- The FBI warned about new cryptocurrency scams.
- TRM Labs linked reduced hacker damage to sanctions against Tornado Cash.
- Ledger’s CEO acknowledged possible government access to wallet assets. In response to user backlash, the company decided to open-source the Recover protocol.
- An employee of the CoinDeal investment project was charged with fraud for $45 million.
- The Dash blockchain experienced a fault.
- Tornado Cash token holders were likened to terrorists.
- Unknown actors seized control of the Ethereum mixer Tornado Cash. The attacker proposed to restore control of the protocol to the Tornado Cash DAO, and later moved some of the stolen tokens.
What to read this weekend?
In the educational section “Cryptorium” we discuss what a VPN is, and the pros and cons of such services.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


