
Bank Heists, Security Services and the Democratic Party Hack: The Story of Russia’s Lurk Hackers
At the end of October 2020, the Sverdlovsk regional court freed Konstantin Kozlovsky — one of the alleged leaders of the Lurk hacking group, whose activities have been investigated for years by law enforcement and cybersecurity specialists. He is believed to have stolen more than a billion rubles from Russians’ bank accounts.
Kozlovsky himself says that he acted on orders from the FSB and is implicated in the hack of the Democratic Party of the United States.
ForkLog examines how Lurk was organized, what links it to the security services, and what tacit rule it violated.
- Initially, the hackers distributed software that, when tested by cybersecurity specialists, did nothing. It later turned out that the program was a modular system and gradually loaded malicious elements. Hence the name Lurk (from English — to lie low).
- Law enforcement detained the suspected participants of Lurk after nearly five years since the start of their activity.
- One of the group’s leaders claimed to have been recruited by the FSB and to be involved in attacks on the Democratic Party of the United States and in creating the WannaCry virus.
- Lurk violated one of the tacit rules in the cybercriminal milieu — “do not operate against Russia”.
Lurk came under the scrutiny of cybersecurity experts in 2011, when several banks reported money theft from accounts. Analysts at Kaspersky Lab detected hidden malware that attacked software for remote banking services.
After the trojan was identified, experts noted that the program behaved as if it did “anything but steal money.” In laboratory tests of its capabilities, no suspicious activity was detected.
At the time, because of this, as well as the relatively small number of incidents involving the software, it attracted little attention. However the malware proved far from harmless, as later turned out.
Thus the program earned the name associated with its operators — Lurk, which in English means “to lie low.”
***
In 2012 a number of major Russian media outlets came under cyberattack — attackers used them to spread malicious software.
“Technically, the malware was unusual: unlike most others, it left no traces on the hard drive of the attacked system, and operated only in the machine’s volatile memory,” said Kaspersky Lab.
Its main aim was reconnaissance. It determined whether a device carried remote banking software from one of the Russian developers. If such a program was found, the device was infected with additional malware.
It also allowed automatically creating payment orders or changing account details.
As later emerged, the program was a continuation of the Lurk virus. In studying many victims’ reports to Kaspersky Lab, analysts concluded that a hacker group stood behind the spread of the malware.
According to the investigation, one of the main organisers of the group was Konstantin Kozlovsky.
Team members were sought online among ordinary programmers. After selection, future staff were told what they would actually do.
Some members were responsible for development and distribution, others for operating the botnet from infected devices. Lurk also had specialists who withdrew illegally transferred funds from ATMs and handed them to the organizers.
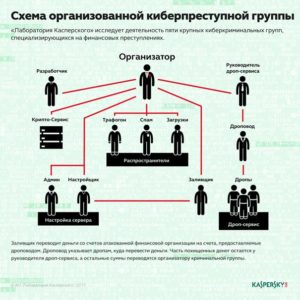
“That period can fairly be called the ‘golden’ period in Lurk’s history, because due to weaknesses in protection of transactions in the remote banking systems, stealing money through an infected accountant’s machine in the attacked organisation was not so much a matter of skill as sometimes simply automatic,” said Kaspersky Lab.
However, over time cybersecurity tools improved and banking systems became less vulnerable.
Consequently, Lurk’s earnings declined. The hackers began offering paid access to other criminals to the Angler exploit package, previously used to spread the Lurk malware, and also altered their methods of stealing funds.
For example, group members began engaging in SIM-swapping. After infecting a victim’s computer, the attackers gathered personal data, then reissued the SIM card and emptied the accounts.
Lurk members carefully encrypted their activities, but over time made more and more mistakes, which allowed law enforcement to identify them.
As a result, in 2016 law enforcement detained 50 suspects with links to Lurk in 15 regions of Russia.
“The arrest of Lurk hackers looked like a thriller. Emergency Ministry workers cut locks in the hackers’ country houses and apartments in different parts of Yekaterinburg, after which FSB officers rushed in, grabbed the hackers and threw them to the floor, and searched the premises,” writes Daniil Turovsky, author of Invasion. A Short History of Russian Hackers.
The exact sum of losses from Lurk’s activities varies by source. The MVD puts it at more than 3 billion rubles, the FSB at 1.7 billion, and media citing investigators’ data report losses of 1.2 billion rubles.
Beyond financial damage to Russian banks, Lurk was suddenly implicated in a political scandal.
Konstantin Kozlovsky, during one of the court hearings, said that, acting on orders from the FSB, he participated in the hack of the Democratic National Committee and Hillary Clinton’s emails.
It was after this breach that the ‘Russian hackers’ became a semi-legendary group and arguably the United States’ main cybersecurity threat, at least according to American authorities and the media.
***
In July 2016, Wikileaks published almost 20,000 emails from the Democratic Party of the United States, obtained in the hack and containing a multitude of compromising items.
CrowdStrike, which investigated the incident, concluded that Russian groups were involved, but not Lurk — Cozy Bear and Fancy Bear.
Nevertheless, Kozlovsky asserted that he was behind the attack and acted on orders from the FSB.
Initially, excerpts of his testimony and letters appeared on his Facebook page, but later they disappeared.
In addition to the Democratic Party hack, he was allegedly involved in attacks on government and military structures, banks and exchanges, FIFA, the Olympic Committee, WADA and others. He also claimed to have been behind the WannaCry virus, whose damage exceeded $1 billion.
Kozlovsky said that he supervised its actions alongside the former FSB major Dmitry Dokuchayev, who was arrested on treason charges and later received six years of imprisonment.
According to the hearing transcript, Kozlovsky insisted that the Lurk-related case was fabricated and that the defendants were in fact innocent:
“My heart aches that I betrayed them all, and that the FSB officers treat us this way. Since I was 16, Dokuchayev and his people led me, and I did everything they said, and now we are all in prison.”
Dokuchayev himself rejected cooperation with Kozlovsky and said he did not even know the latter.
Kozlovsky also mentioned a Kaspersky Lab employee, Ruslan Stoyanov, who was involved in treason cases alongside Dokuchayev. Notably, Stoyanov was among those who investigated Lurk and described in detail how the group was organised.
Other defendants in the Lurk case did not unequivocally confirm Kozlovsky’s statements. One of the group’s members, Igor Makovkin, said he had never heard of any supposed FSB role in Lurk’s actions.
Makovkin entered into a pre-trial cooperation agreement and his case was separated into a separate proceeding. In 2018 the court sentenced him to five years in a standard regime colony.
In summer 2020, some of the defendants were released from custody, with their remand replaced by house arrest. Later Kozlovsky was released as well — he is barred from using a phone and the internet, and from communicating with other defendants.
***
Whether Lurk operated under the auspices of the FSB or whether this was merely Kozlovsky’s attempt to shift part of the responsibility remains unknown.
Some argued that the statements that appeared on the Facebook page could not have been posted by Kozlovsky, since he was in pre-trial detention at the time.
In addition to the Democratic Party hack, experts attributed the WADA incidents to the group Fancy Bear. It is associated with Russian security services, but linked to the GRU rather than the FSB.
Despite media naming Lurk as one of the largest hacker groups in Russia’s history, its scale and threat may be overstated — one member, Alexander Safonov, described Lurk as largely an ineffective “gathering of amateurs”.
At the same time, he claimed that shortly before the arrest the hackers carried out several breaches together with a more advanced group of specialists who, he says, were recruited by the FSB.
Lurk violated one tacit but important rule — “do not operate against Russia”.
“In translation to Russian, the phrase means the following: ‘do not steal from Russian citizens, do not infect their machines, do not use compatriots to launder money'”, explain Kaspersky Lab.
The matter is not about patriotism, but about “utterly utilitarian considerations,” ForkLog says, citing Group-IB head Ilya Sachkov. If a cybercriminal operates in the country where he lives, he will be found and jailed quickly.
Author: Alina Saganskaya.
Subscribe to ForkLog news on Telegram: ForkLog Feed — all the news stream, ForkLog — the most important news and polls.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


