
Experts dissect the Blender Wallet hack
The hack of the non-custodial Blender Wallet on June 22 may very likely be an insider attack. This is what ForkLog’s experts polled concluded.
The Blender Wallet site states that, to compensate funds, they require users’ seed phrases, although non-custodial wallets are architecturally unable to access them and should not have access to them.
Kirill Chikhradze, Director of Product Development at Crystal Blockchain, said that their team managed to identify several service wallets of Blender Wallet and the Blender.io mixer, through which since early 2019 about 70 BTC in total have passed, which casts doubt on the claimed loss total of 100 BTC.
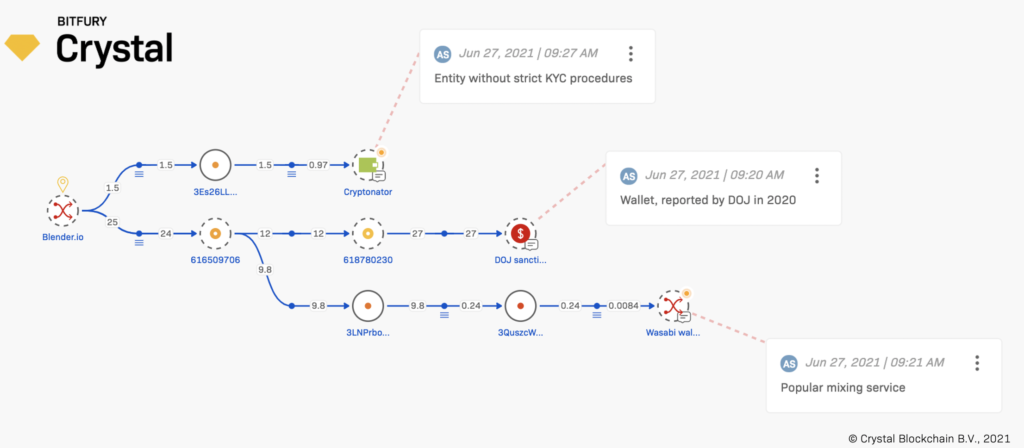
“It is still unclear exactly how the claimed attack could have occurred. Perhaps in a way similar to the Electrum attack in 2019. However the request to provide the seed phrase and password to recover funds should raise suspicion,” he noted.
It remains unclear how the service’s team calculated losses. Consensus protocols researcher Andrey Sobol told ForkLog that Blender Wallet operators could have learned the amount of losses if all requests went through their API.
“That is, when a user registered a new wallet, then their set of public addresses was sent to the server,” he speculated.
According to him, such a mechanism is used in many non-custodial solutions.
“In reality, the alternative is some decentralised network of nodes. Something similar to Electrum, but it slows it down. The telltale sign is, if the wallet operates stably and normally in updating information about new transactions, then the owner of the service has their own dedicated infrastructure,” Sobol explained.
Theoretically there are cases where sending the private key may be a prerequisite for compensation, the expert continues:
“Perhaps they fear that random people will start posing as owners of other people’s wallets. If we assume they are not scammers, they may request the seed phrase as 100% identification.”
Sobol noted that the company could ask users to sign a message with the private key, but for this the wallet would need a signing feature built in. Otherwise it would be easier to request the seed phrase.
“I do not rule out that hackers might attempt to steal money twice. First from wallets, and then, knowing the private key, they will ask the owners for a refund,” added Andrey Sobol.
According to Trustee Wallet CTO Ksenia Zhytomyrskaya, the incident currently looks like an insider breach:
“Most likely, code was injected inside the app that used user funds without their knowledge. This would explain the disabling of the Replace-By-Fee (RBF) function in the interface. If mnemonic phrases were leaked, then through any wallet you could withdraw,” she told ForkLog.
The expert noted that in an exit-scam the team would have taken all the money.
Zhytomyrskaya suggested that the seed-phrase requests could have been motivated by the team tracking a public address via it and confirming ownership.
“They simply want to collect the addresses of users who will claim reimbursement. Those who are afraid to send them simply won’t be compensated. Otherwise everyone would have to be compensated according to logs, since they saw the thieves’ transfers.”
Overall, the demand to provide seeds and passwords is excessive, emphasized the CTO of Trustee Wallet.
Among probable reasons for the hack of non-custodial wallets, Ksenia Zhytomyrskaya named sloppy log management, openly stored seed phrases, auto-fill of passwords, and classic credential-harvesting malware.
“Moreover, not all non-custodial projects are truly non-custodial, but that can be attributed to the injection of malicious code. Hence the importance of code auditing,” she added.
Zhytomyrskaya could not find the Blender Wallet source code. In a BitcoinTalk thread dedicated to the wallet, in May 2021 project representatives wrote that they “decided not to open the source code.”
The cybersecurity expert Yuri Melashchenko of Security Services Group warns of the potential danger of anonymous projects.
“From the outset the project was anonymous and private; it is impossible to determine who owns this email and Jabber. If you use mixers, you should understand that filing a report to the police or complaining to someone is unlikely to work. Initially the project deals in shady acts and appealing to some sense of justice in this case is even foolish.”
He noted that access to the server or hosting is held either by the owners or by hackers who can alter the site code.
“Perhaps from the outset the private keys were not accessible, but after hackers breached the hosting, changed the homepage and the code, they gained access to them,” the expert suggested.
Melashchenko stressed that if users are asked to send seed phrases, this means there can be no talk of non-custodianship.
“No non-custodial wallet service has access to private keys by design. I would never, under any circumstances, send the seed phrase, and would try entering it into another wallet to check the balance. If you see that everything is stolen, you can provide the seed, but never again accept funds to that wallet.”
Sending seed phrases from wallets to third parties endangers the safety of your funds. If you decide to send a seed phrase in the Blender Wallet incident, to minimise risk ensure via a third-party interface that the wallet balance is zero, and never again accept funds to it.
He noted that the team could just as easily have requested a public key rather than a seed phrase, but evidently users were not told where to generate or view it.
The Trustee Wallet CTO also says that without the source code it is difficult to draw conclusions.
“In a web app such as Metamask, mnemonic phrases are encrypted in storage, so it all comes down to developers. You need to look at the code and figure out why not everyone was hacked and what it depended on: perhaps only those who were active in the last days or who updated the version,” she noted.
A person identifying as a Blender Wallet representative told ForkLog that the team cannot establish wallet ownership without seed phrases, because they do not store any user data.
The loss amount in Blender Wallet was calculated based on “which addresses were generated in our wallet and the balance on them.”
Zhytomyrskaya notes that access to balance on addresses requires only the public key:
“If they require seed phrases, they contradict themselves. They can see the balance of an address after they receive it. But I don’t know whether they tracked them before the breach — for that you need the source code.”
According to the person who calls himself Blender Wallet’s representative, access to the source code is closed because, as they say, “it’s not an application but a website.” Melashchenko counters that running such a business without disclosing the code is unethical practice given that it deals with money.
ForkLog’s interviewee who claimed to be Blender Wallet’s representative confirmed that a seed phrase created at registration can be used in other wallets.
From the team’s side, he promised to provide transactions involving the stolen funds later.
ForkLog will continue to monitor developments. If you were a victim of the Blender Wallet hack or have additional information, please write to the editorial desk at newsroom (@) forklog.com.
Follow ForkLog news on VK.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


