
Hacked Crypto Cameras, Durov vs WhatsApp, and Other Cybersecurity News
Durov warns of WhatsApp vulnerabilities; DNS data leak; Water Labbu extortion; Maggie backdoor; Optus breach arrest; PwC-linked hacking.
We round up the week’s most important cybersecurity news.
- Durov warned that hackers have full access to the contents of phones via WhatsApp.
- Cryptocurrency scammers were victimised by Water Labbu attackers.
- Hundreds of Microsoft SQL servers were attacked by the Maggie backdoor.
- The DNS retailer confirmed a leak of customers’ personal data.
Durov reports hackers have full access to content on phones via WhatsApp
Telegram founder Pavel Durov warned WhatsApp users about potential access by hackers to contents on their phones.
According to him, this became possible due to a security vulnerability found by WhatsApp developers last week. It allowed hackers to execute remote code by sending the victim a malicious video or initiating a video call in the app.
Durov stressed that updating WhatsApp to the latest version does not solve the problem, because similar vulnerabilities have been found regularly since 2017. Before 2016 the app had no encryption at all.
“Every year we hear of a WhatsApp issue that threatens all users’ devices. That suggests there is almost certainly another breach in the security system already there. Such problems are unlikely to be mere accidents — they are backdoors,” wrote Durov.
The Telegram founder recommended avoiding WhatsApp, which he says has “been a tool of surveillance” for 13 years.
Meanwhile, Meta filed a suit against several Chinese companies for developing and allegedly using “unofficial” WhatsApp apps for Android to steal more than a million accounts since May 2022.
The DNS retailer confirmed a leak of customers’ personal data
On October 1 the Telegram channel “Data Leaks” found a partial dump of 16.5 million records containing DNS store customers’ data.
It contains:
- first and last names (not for everyone);
- email address (7.7 million unique addresses);
- phone number (11.4 million unique numbers);
- username.
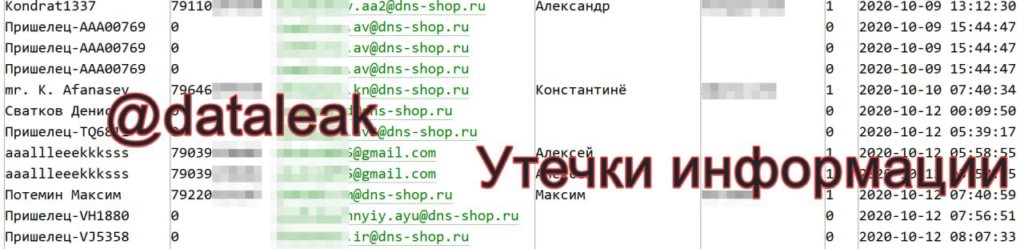
Partial dump was obtained no earlier than September 19. Its source is the September data dump from the online retailer “Online Trade.Ru.”
In addition, another DNS SQL dump from June 12, 2008 is publicly accessible. It includes hashed user passwords.
On October 2 DNS confirmed a leak of customers’ and employees’ personal data. The company did not disclose the number of affected individuals or the nature of the exposed data, noting only that passwords and bank cards were not touched.
“The breach was carried out from servers located outside Russia. We have already found gaps in the protection of our information infrastructure and are working to strengthen information security,” added DNS.
The retailer is now conducting an investigation and addressing the consequences of the attack.
Hundreds of Microsoft SQL servers were attacked by the Maggie backdoor
Security researchers from DCSO CyTec uncovered a new malware, Maggie, aimed at Microsoft SQL servers.
MSSQL, meet Maggie!
In our latest blog post, we analyze ‘Maggie’, a novel backdoor for MSSQL servers, implemented as an Extended Stored Procedure and only controlled using SQL queries.https://t.co/A6SQ3lLHPE
— DCSO CyTec (@DCSO_CyTec) October 4, 2022
It has already infected hundreds of machines in South Korea, India, Vietnam, China, Russia, Thailand, Germany, and the United States.
The backdoor masquerades as an Extended Stored Procedure DLL (sqlmaggieAntiVirus_64.dll) with a digital signature from DEEPSoft Co. Ltd, which appears to be based in South Korea.
Hackers control Maggie via SQL queries, enabling it to fetch system information, launch programs, interact with files and folders, enable Remote Desktop Services, launch a SOCKS5 proxy, and configure port forwarding.
The malware can also brute-force administrator credentials to move laterally to other Microsoft SQL servers.
The malware includes a simple TCP redirection function that helps attackers connect to any IP address accessible from the infected MS-SQL server.
It is not yet clear how exactly attackers use Maggie after infection, how the malware is deployed on servers, or who is behind the attacks.
Cryptocurrency scammers fell prey to Water Labbu attackers
The Water Labbu hacker group compromised cryptocurrency scam sites and siphoned off the funds of their victims, Trend Micro reports.
In July the FBI warned about fraudulent dapps that steal cryptocurrencies under the guise of liquidity mining. Water Labbu injects malicious scripts into such sites. They monitor newly connected Tether and Ethereum wallets with balances above 22,000 USDT or 0.005 ETH, respectively.
If the victim uses a mobile device, the script prompts the user to approve the transaction through the site of a decentralized application, creating the impression that the transaction originates from the scamming resource itself. If the request is approved, all funds go to the operators’ address.
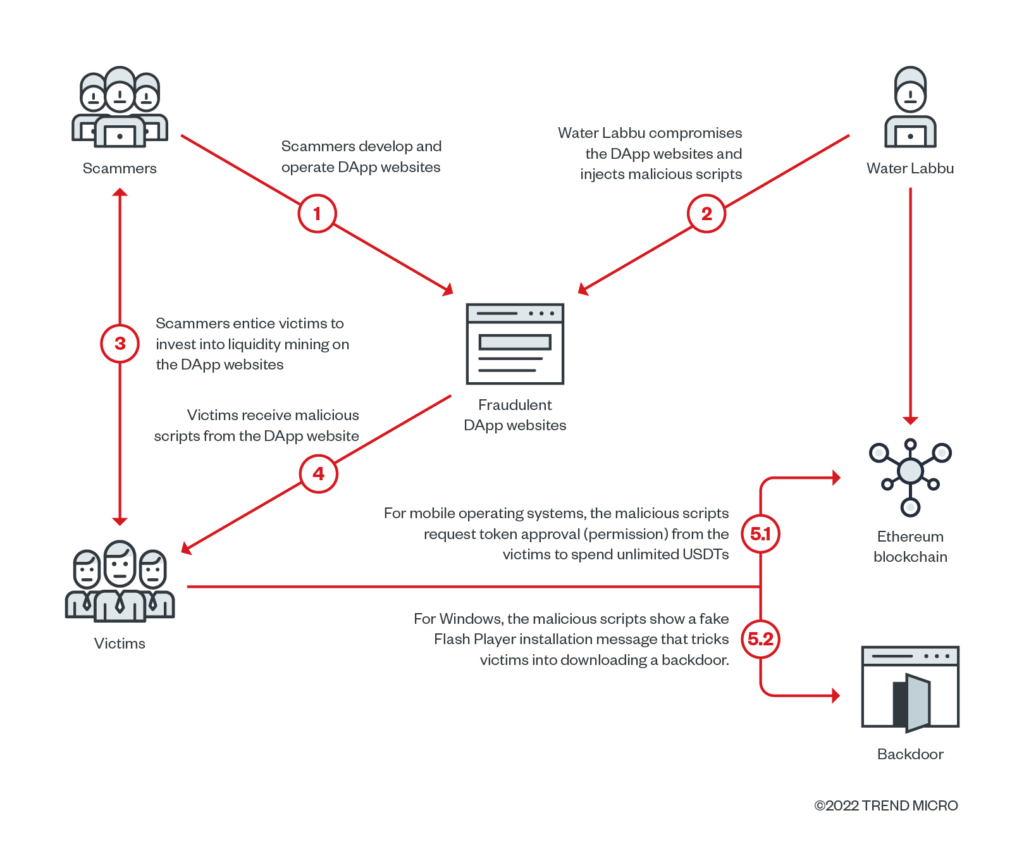
For Windows users, compromised sites display a fake notification to update Flash Player. That “installer” actually loads a backdoor directly from GitHub.
According to Trend Micro, Water Labbu’s profits amount to at least $316,728, based on transaction records from nine identified victims.
Australian police arrest teen who planned to profit from Optus breach
The Australian Federal Police (AFP) arrested a 19-year-old Sydney resident on charges of using Optus customer data for extortion.
According to the agency, the teen sent SMS messages to Optus breach victims demanding payment of A$2,000 within two days. Otherwise, he threatened to sell their personal data to other hackers.
To obtain the ransom, the hacker used an account at the Commonwealth Bank of Australia. The bank provided the police with the account holder’s information.
AFP says the arrested individual allegedly messaged 93 Optus customers whose data the hacker published on an online forum. None paid.
The teen is charged with extortion and unauthorized use of identification data. He faces up to 17 years in prison.
The hackers behind the Optus breach remain unidentified; the investigation continues.
Experts link organizers of hacks across 35 countries to intelligence services
An unnamed elite Chinese group linked to intelligence services has intensified the theft of confidential data from companies and government agencies around the world. CNN cites PwC’s research.
The attackers study networks for information on external or trade policy, but also use cryptocurrency scams. The group is described as the most active and influential among those tracked by PwC.
Experts say that in 2022 the hackers attacked organizations in at least 35 countries. In the United States, victims included government agencies, tech firms, and software developers. PwC did not specify details about those affected.
PwC researcher Chris McConkey previously disclosed the group’s campaigns, identifying suspected locations of the hackers from China, Iran, and other states.
Another expert, Adam Kozi, who tracked Chinese hackers for the FBI from 2011 to 2013, said that officers of the People’s Liberation Army conducted cyberattacks on Taiwan. He stressed that this is a core focus of China’s influence operations.
Also on ForkLog:
- A decentralized exchange Transit Swap lost $21 million in a hacker attack.
- The hacker behind Transit Swap sent assets to Tornado Cash.
- The Discord server of artist Beeple suffered a phishing attack.
- Elliptic: more than $4 bn in crypto were laundered through DEXs and cross-chain swaps.
- In Q3 the crypto industry lost $428 million to hacks and scams.
- The Zcash faced a spam attack.
- The BNB Chain team restored network operations after a $100 million breach.
- Celsius Network disclosed detailed user transaction data.
What to read this weekend?
In this popular feature, we explain how to access blocked resources and stay connected with loved ones even after a total internet outage.
Read ForkLog’s Bitcoin news in our Telegram — cryptocurrency news, prices, and analysis.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


