
Hackers stole bitcoins in 52 countries via a fake Tor browser
Malicious actors are distributing the CryptoClipper Trojan disguised as the Tor browser on third-party websites. This was сообщили experts at Kaspersky Lab.
Once it infects a victim’s system, the clipper registers itself in startup under the guise of a popular application, such as uTorrent.
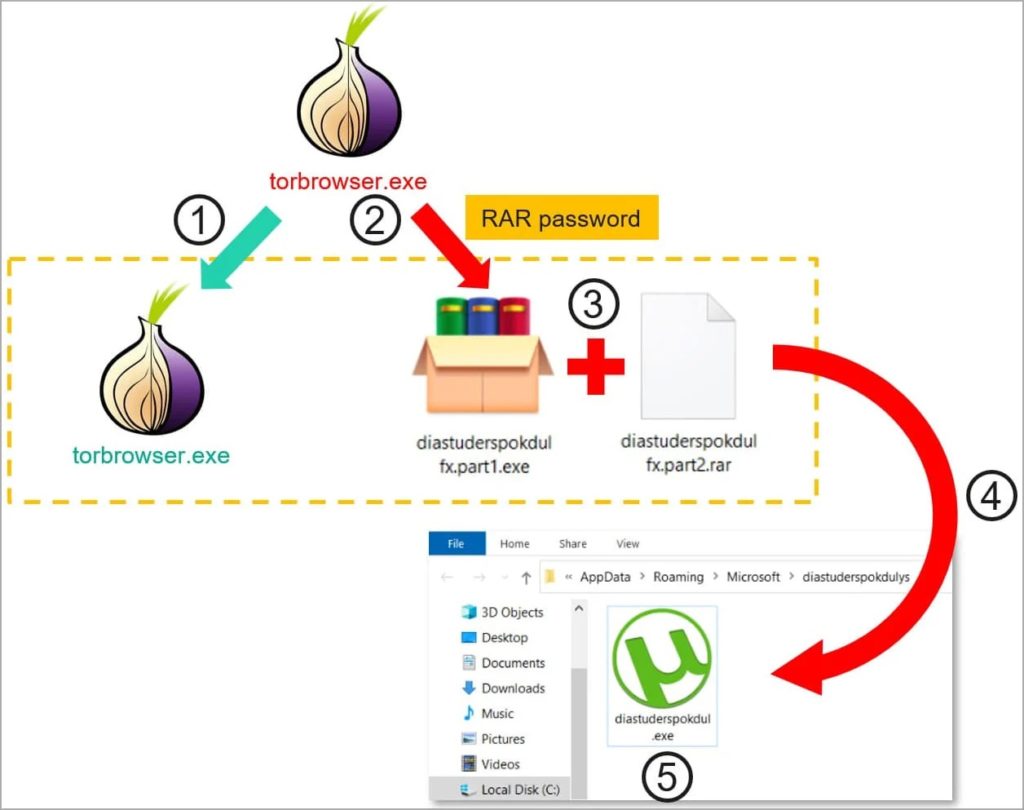
When it detects a cryptocurrency address in the clipboard, it automatically replaces it with one of the attacker\’s wallets. The clipper is capable of substitutions in the networks of Bitcoin, Ethereum, Litecoin, Dogecoin and Monero.
The campaign has already affected more than 15,000 users in 52 countries. The highest number of attacks has been recorded in Russia, where the Tor browser has been blocked since the end of 2021. Rounding out the top ten countries by victims are the United States, Germany, Uzbekistan, Belarus, China, the Netherlands, the United Kingdom and France.
Experts estimate that in 2023, using the malware, more than $400,000 in cryptocurrency was stolen.
Earlier, ESET Research researchers uncovered Trojan‑like variants of Telegram and WhatsApp for Android and Windows, aimed at stealing cryptocurrency and able to recognise seed phrases from screenshots.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


