
Lazarus Group Launders $200 Million from 25 Crypto Attacks, Report Reveals
On-chain researcher ZachXBT tracked the movement of $200 million stolen by the Lazarus Group hackers in 25 cyberattacks from August 2020 to October 2023.
2020: CoinBerry, Unibright, and CoinMetro Hacks
In August, the perpetrators withdrew $370,000 from the hot Bitcoin and Ethereum wallets of the Canadian crypto exchange CoinBerry. In September, they took $400,000 from the Unbright platform, and in October, $750,000 from CoinMetro.
The funds from these three thefts were moved by the Lazarus Group through intermediary wallets before being consolidated at one address in early January 2021.
The funds were then gradually transferred to the hackers’ account in Tornado Cash and subsequently withdrawn to an Ethereum address, where they were combined with assets obtained from other group thefts.
That same year, several transfers were made to an OTC trader from China, Wu Huihui, who was later sanctioned by the OFAC.
From July 2022 to November 2023, USDT was withdrawn in small batches to P2P platforms Paxful and Noones.
December 2020: Hack of Nexus Mutual Founder Hugh Karp
On December 14, hackers gained remote access to Karp’s computer and stole 370,000 NXM ($8.3 million) from his MetaMask.
From December 16 to 17, 137.1 BTC from this amount were sent in six transactions to the centralized mixing service ChipMixer. A few hours later, 136 BTC were withdrawn back to Ethereum via Ren Project and consolidated with funds from other thefts.
After passing through Tornado Cash, the assets ended up in a new Ren wallet.
In March 2021, the stolen cryptocurrency was repeatedly cycled between Bitcoin and Ethereum networks via ChipMixer. In April, a small portion of BTC was sold to Wu Huihui. The remaining amounts were sent to the Bixin exchange, Paxful, and Noones platforms.
April 2021: Hack of EasyFi Founder Ankitt Gaur
Similar to the previous case, $81 million in various tokens were stolen from Gaur via a malicious version of MetaMask.
The assets were then moved to new addresses using cross-chain transfers, sent to ChipMixer, and returned to the Ethereum network via the Ren protocol.
In June 2022, funds from two addresses were sent to new EOA addresses, where they were consolidated with other illegally obtained cryptocurrencies. They were then sent to the Binance exchange among other funds.
Another batch of funds was withdrawn to new Ethereum wallets as renBTC via ChipMixer, later exchanged for DAI and wBTC.
The final movements again led researchers to Paxful and Noones, where assets in the form of USDT were sent in small batches until November 2023.
July 2021: Bondly Hack
The incident resulted in $8.5 million in losses across Ethereum, BSC, and Polygon.
All assets went through the Tornado Cash mixer and were transferred via multichain bridges to new Ethereum addresses.
In June 2022, combined with other stolen funds, they ended up on Binance. Again, until November 2023, batches of USDT were sent to Paxful and Noones.
August and September 2021: Unknown Hacks
Due to the compromise of a private key, several individuals lost $2 million. The hackers immediately converted the assets to ETH, withdrew them to a single address, and sent them to Tornado Cash.
Through an intermediary wallet, the funds were combined with other illegal proceeds and distributed across exchanges.
October 2021: MGNR and PolyPlay Hacks
MGNR lost $24 million. The assets, converted to Ethereum, were sent in two parts through Tornado Cash and ended up in previously used Lazarus Group wallets. From summer 2022, USDT was sent to Paxful and Noones.
PolyPlay suffered $1.6 million in losses. The laundering followed a similar scheme.
November 2021: bZx Hack
A phishing attack on the protocol netted hackers $55 million. All cryptocurrency, after Tornado Cash, was further mixed with previously laundered assets from the above hacks and sent to Paxful.
August 2023: Steadefi and CoinShift Hacks
User losses amounted to $1.2 million. In the case of Steadefi, hackers posed as an employee of the investment fund Spirit Blockchain Group.
CoinShift did not publicly report the incident, but funds from wallets linked to the platform’s founder were suddenly withdrawn on August 16.
The stolen Ethereum from both hacks was sent in parts to Tornado Cash within minutes of each other.
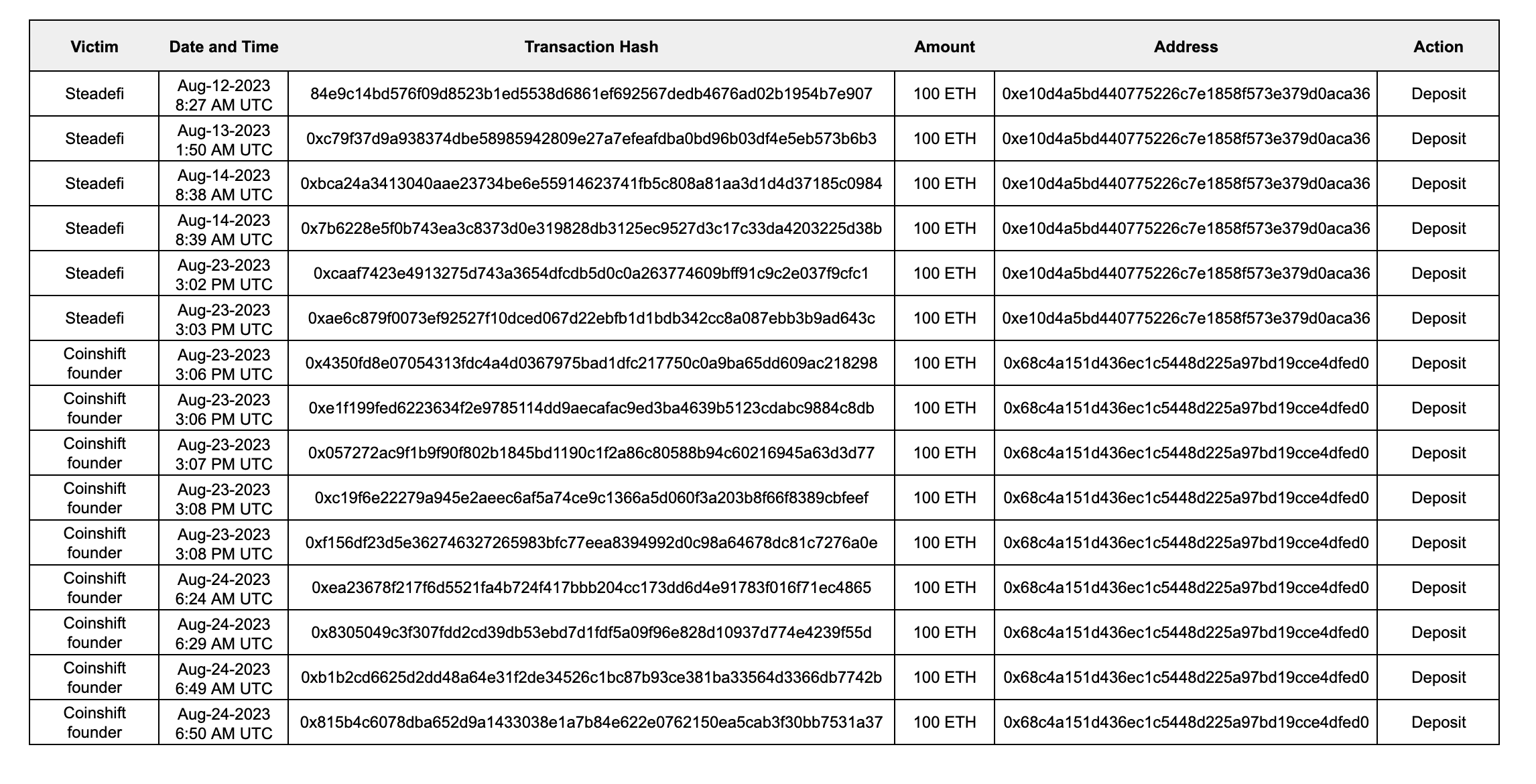
Assets distributed across three addresses later ended up in a single wallet. After conversion to USDT, they were sent to the hackers’ accounts on Paxful and Noones.
Investigation Results
In total, accounts belonging to Lazarus Group on P2P platforms Paxful and Noones received $44 million from July 2022 to November 2023. The hackers later switched to new deposit addresses.
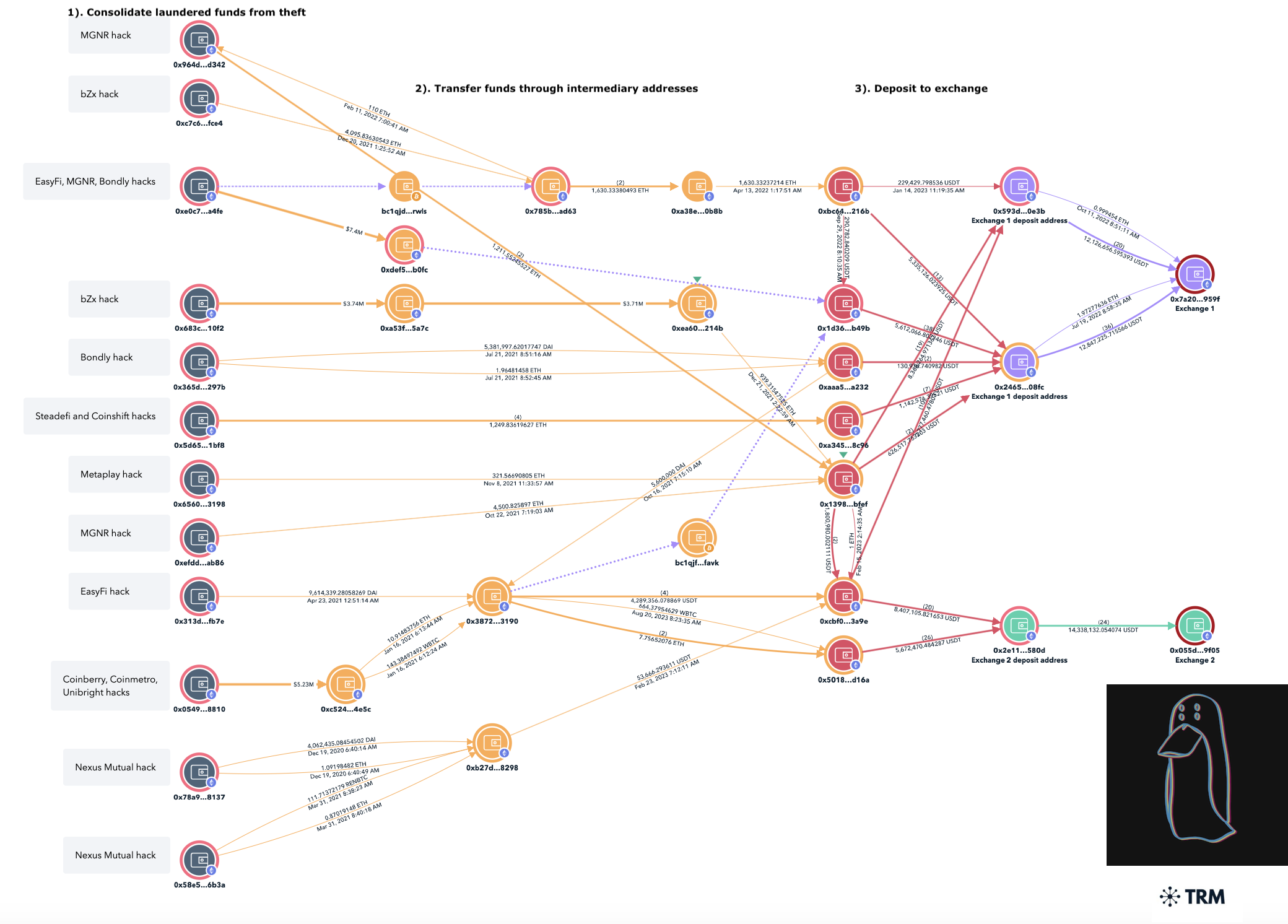
The entire amount was converted to fiat via bank transfers or cash withdrawals. Traditionally, the Lazarus Group uses Chinese OTC traders for this purpose.
In November 2023, Tether blacklisted $374,000 of the funds stolen by hackers. An undisclosed amount was also frozen on centralized exchanges in the fourth quarter of 2023.
Additionally, three out of four stablecoin issuers blocked an additional $3.4 million on addresses belonging to the cybercriminals.
Previously, ForkLog reported that the Lazarus Group created a fake investor to attack the DeFi segment.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


