
New Android Malware, ASUS Breach, and More: This Week in Cybersecurity
New Android spyware, a supplier breach tied to Asus, and a botnet menacing maritime systems.
The week’s key cybersecurity developments.
- Researchers found a compromised device belonging to a North Korean hacker.
- Spyware is targeting Android users.
- The Broadside botnet targets maritime navigation systems.
- Asus, Qualcomm and ArcSoft were hit by hackers.
Analysts find a North Korean hacker’s compromised device
Researchers at Israeli cybersecurity firm Hudson Rock found in the logs of the Lumma infostealer a compromised device belonging to a North Korean hacker.
The data point to a direct link between the owner and infrastructure used in the attack on Bybit in February. A crucial clue was an email address on the device that had appeared in Silent Push reports; it was used to register a phishing domain just hours before the Bybit incident.
Although the owner of the infected system may not have taken part directly in the theft of funds, experts are confident the machine was part of the shared resource pool of Lazarus.
According to the analysts, the compromised workstation was powerful and purpose-built for developing hacking tools. Despite using a VPN to appear as a US IP address, the browser language was set to Chinese, and the search history contained requests to translate from Korean.
Disk activity suggested the hacker was preparing a new phishing campaign. The researchers also found evidence of purchases of domains impersonating popular services and local files for fake Zoom installers.
Spyware targets Android users
Zimperium experts identified a new malicious campaign targeting Android users.
The newly observed DroidLock trojan blends ransomware and spyware functions. It spreads via fraudulent sites masquerading as legitimate apps, using a two-stage infection scheme. Once installed, it tricks users into granting device administrator and accessibility permissions.
The trojan mainly targets Spanish-speaking users and can change the PIN and biometric settings, as well as remotely control the device. It also captures unlock patterns, records audio and steals the contents of SMS and calls.
Unlike traditional lockers, DroidLock does not encrypt files; it threatens to delete them. On command from its server, a ransom demand is displayed on the screen.
The researchers have notified the Android security team, and Google Play Protect can now detect and block the threat.
They strongly advise against sideloading APK files from third-party sources and urge caution with apps that request device administrator rights.
The Broadside botnet targets ships’ navigation systems
The new Broadside botnet is actively infecting CCTV systems and IoT gateways on commercial vessels, report experts at Cydome, a maritime-cybersecurity firm.
The malware is based on Mirai’s code. Its chief danger lies in its ability to mount powerful DDoS attacks and covertly intercept video streams. Infected devices can be used as a beachhead to penetrate ships’ navigation systems, posing a direct threat to maritime safety.
According to Cydome, the botnet activates password‑brute‑forcing against VSAT satellite terminals that provide connectivity to ships on the open sea. Infection happens automatically when a victim enters the coverage area. After compromising the gateway, the malware scans the vessel’s local network for weaknesses in electronic navigation chart display systems.
The researchers warned that Broadside’s operators have begun selling access to infected onboard networks on underground forums. Buyers may include rivals of logistics firms seeking route and cargo data, as well as pirates using vessel location information to plan physical attacks in high‑risk regions.
Asus, Qualcomm and ArcSoft hit by hackers
Asus confirmed unauthorised access at a supplier’s infrastructure. The extortion group Everest in turn claimed a large data theft, the outlet Hacker reported.
The criminals say they stole 1TB of confidential information from all three companies — Asus, Qualcomm and ArcSoft. Media reports say the haul includes smartphone‑camera software source code, custom AI models and internal developer tools.
As proof, the hackers posted screenshots of compromised files on the dark web.
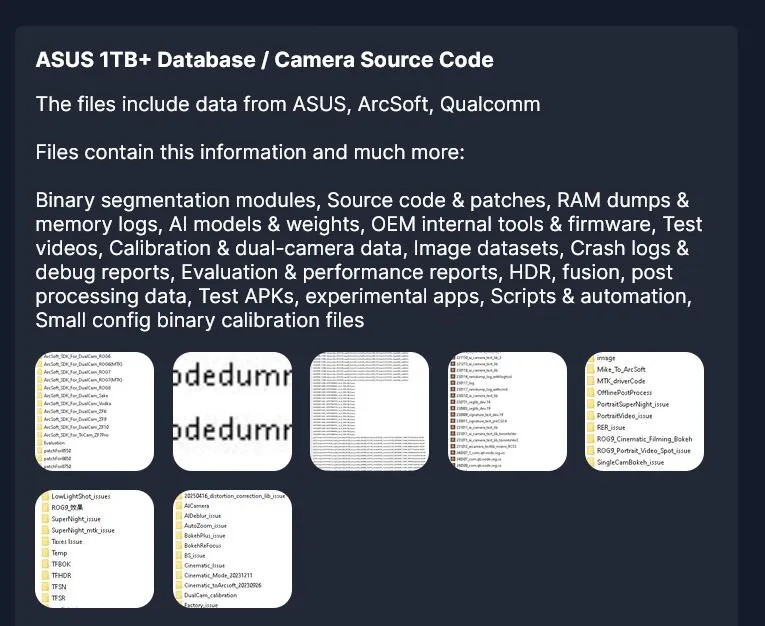
Asus stressed that the attack did not affect its own servers or customer data. The leak was limited to parts of the mobile‑camera software source code managed by a partner. The company has launched a supply‑chain security audit but did not name the compromised contractor.
At the time of writing, Qualcomm and ArcSoft had not commented on the possible data loss.
Also on ForkLog:
- Belarus’s Ministry of Information cited the reason for blocking several crypto exchanges.
- A co‑founder of the Finiko pyramid was extradited from the UAE to Russia.
- Silk Road wallets moved $3m in bitcoin.
- Arkham de‑anonymised more than half of Zcash transactions.
What to read this weekend?
French thinkers showed that technology is not neutral. The internet, conceived as a realm of freedom, carries the genes of control and simulation.
How 20th‑century ideas help explain the current state of Web3 — read our new ForkLog piece.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


