
DeFi’s manipulation problem: what the “financial LEGO” conceals
The fast-evolving DeFi sector offers users undeniable advantages regardless of capital, age or country. With a smartphone and an internet connection, you can access savings, loans and other financial tools without KYC, paperwork or intermediaries.
For the unbanked, it is a way to manage their own money without bureaucracy and other barriers; in high-inflation economies, stablecoins become an alternative to depreciating fiat. Smart contracts power everything—fast, transparent and without the “we’ll call you back”.
Yet DeFi still resembles the Wild West—light on regulation and prone to manipulation—worrying institutions and watchdogs. The industry is maturing quickly, however: tools to detect and curb sharp practice are improving.
DeFi’s standard-bearer?
Uniswap has for years led DEX by trading volume, only occasionally ceding first place to Solana-based Raydium.
As one of the first platforms to bring the AMM mechanism to market, Uniswap continues to remain the standard-bearer of DeFi innovation.
Even here, manipulation persists. A common tactic is the sandwich attack. Borrowed from high-frequency trading in TradFi, it sees an attacker place a buy order just before the victim’s trade and then a sell order immediately after—within the same block. The price is briefly distorted; the attacker profits at the user’s expense.
According to Kaiko, in March a market participant tried to swap ~220,800 USDC for USDT in the corresponding Uniswap V3 liquidity pool on Ethereum. Just before execution, the attacker sold almost 20m USDC for USDT, crashing Circle’s stablecoin to 0.024 USDT amid thin liquidity and heightened pool slippage.
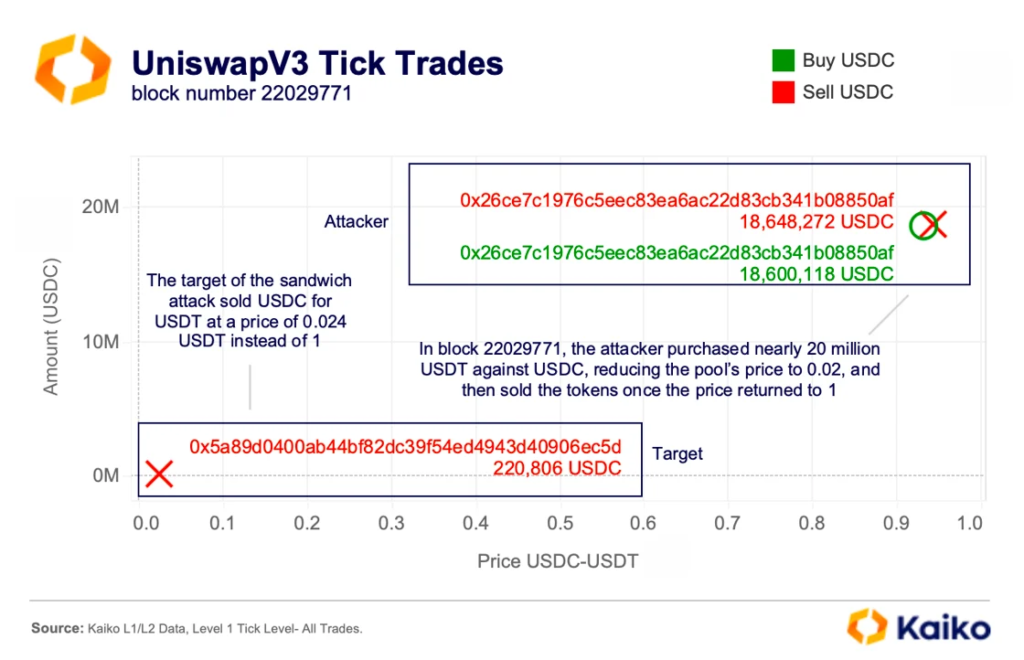
The swap cleared at a disastrous rate: the user received only about 5,300 USDT instead of the expected 220,800 USDT, losing roughly 215,500 USDT.
“The attacker then repurchased USDC at a lower price within the same block. They still profited after paying $200,000 to the block builder for priority execution,” the Kaiko researchers explained.
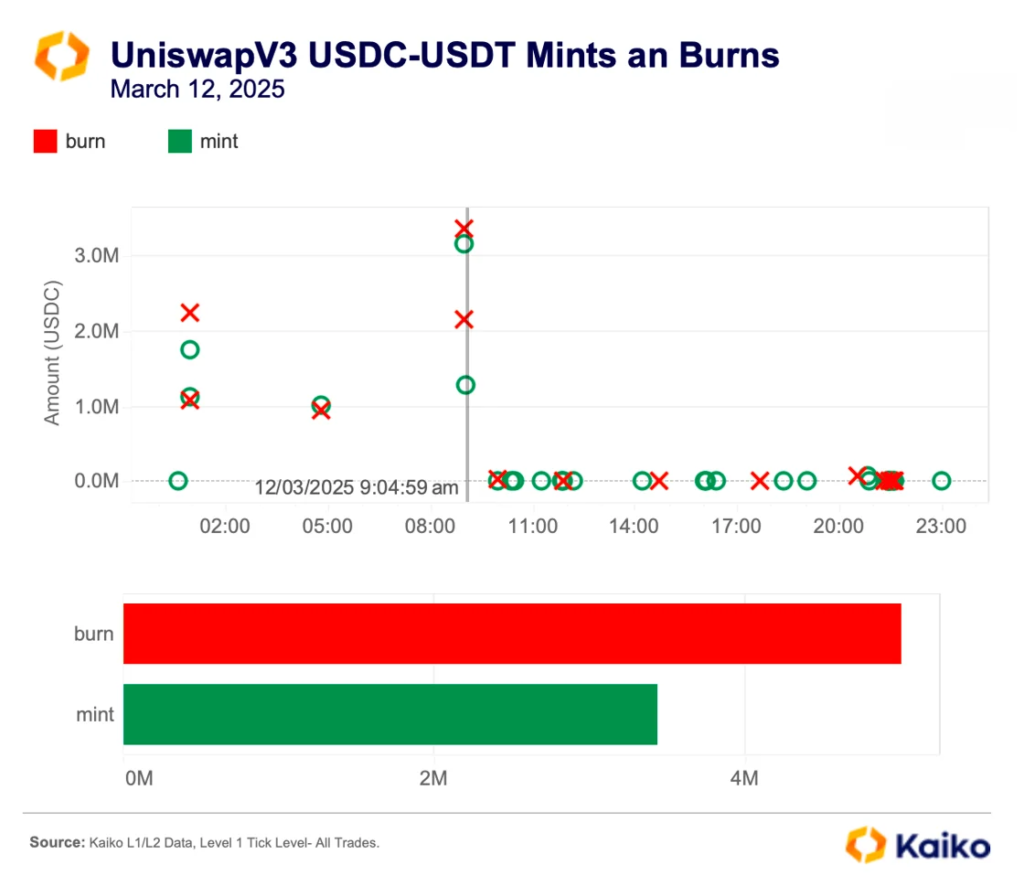
They observed that the incident coincided with declining USDC liquidity on Uniswap V3. On the day of the attack, more funds were withdrawn from the pool than added, helping the manipulator move the price.
“The result was significant slippage—the gap between expected and actual execution price. This created market risk not only for the victim but for all traders using that pool at the time,” the experts noted.
Similar—sometimes more intricate—attacks flare up on other non-custodial venues too, including the hyped-up Hyperliquid.
A new stress test
Hyperliquid, one of the largest platforms for decentralised perpetuals, came under a coordinated attack late last month. The incident, and the team’s response, caused an uproar in the crypto community, prompting debate and doubts about decentralisation.
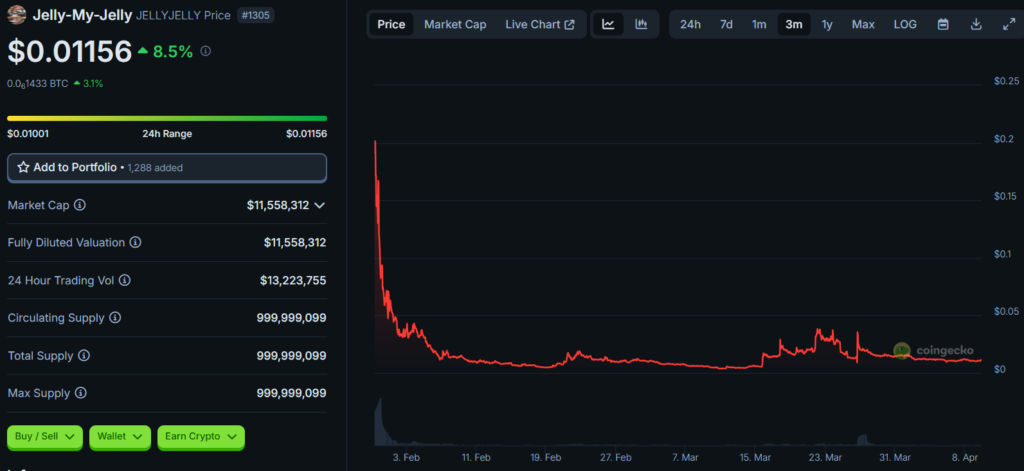
On 26 March 2025 an unknown trader targeted the Hyperliquidity Provider Vault (HLP), opening large positions on contracts tied to the thinly traded Jelly-My-Jelly (JELLYJELLY): a short of roughly $4m and two longs totalling about $3m.
JELLYJELLY’s market capitalisation is a modest $11.5m, though the coin trades on both DEX and CEX.
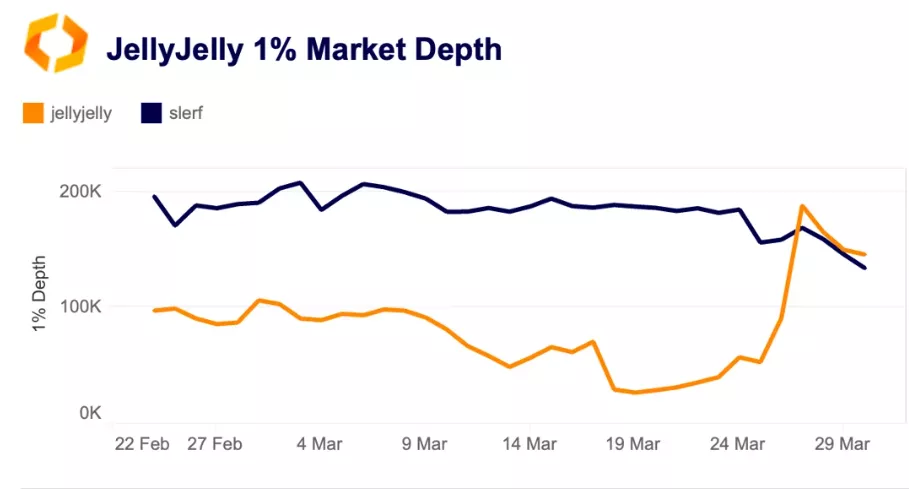
“Its daily liquidity, measured by 1% market depth, averaged just $72,000—less than half the figure for comparable low-cap tokens like Slerf ($190,000); more than 1,000 times lower than that of Solana’s native token, SOL,” observed Kaiko’s researchers.
During the attack the trader ran two coordinated manoeuvres, opening a short and a long on the token’s perpetuals simultaneously:
- Forced liquidation. The attacker withdrew the margin backing the short, triggering liquidation. Losses were borne by HLP.
- Spot pump. In parallel, the trader aggressively bought JELLYJELLY on spot markets. Given the low liquidity, the token spiked. Because Hyperliquid’s derivatives settle off a spot price sourced via an oracle, this instantly drove up perpetuals.
Within an hour the price of Jelly-My-Jelly surged by more than 500%—from $0.00806 to $0.0517.
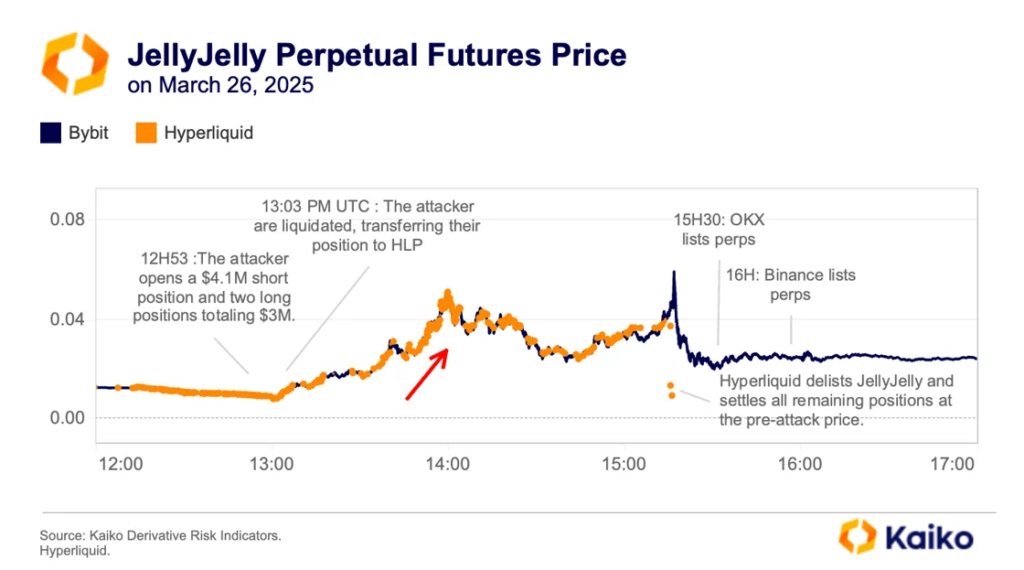
In Kaiko’s view, the manipulation exposed weaknesses in Hyperliquid’s liquidation mechanism.
“After open interest exceeded critical thresholds, the platform blocked new positions. This prevented liquidators from closing the attacker’s short in time, increasing losses and exacerbating HLP’s situation,” the experts explained.
They added that Binance and OKX fanned the flames—these large centralised exchanges listed Jelly-My-Jelly futures the same day Bybit’s trading volume in the asset hit a record $150m.
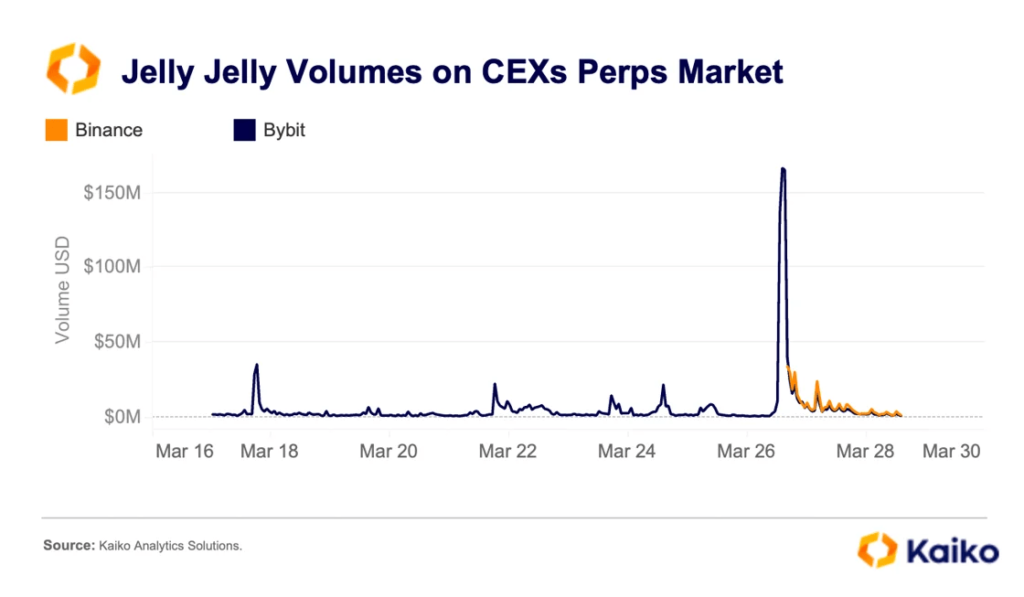
Kaiko also noted that activity around JELLYJELLY came with violent price swings and liquidations “on both sides of the market”:
“In the morning forced short closures dominated, but by evening it was long holders who were caught. The largest liquidation on 26 March was a short of about $250,000.”
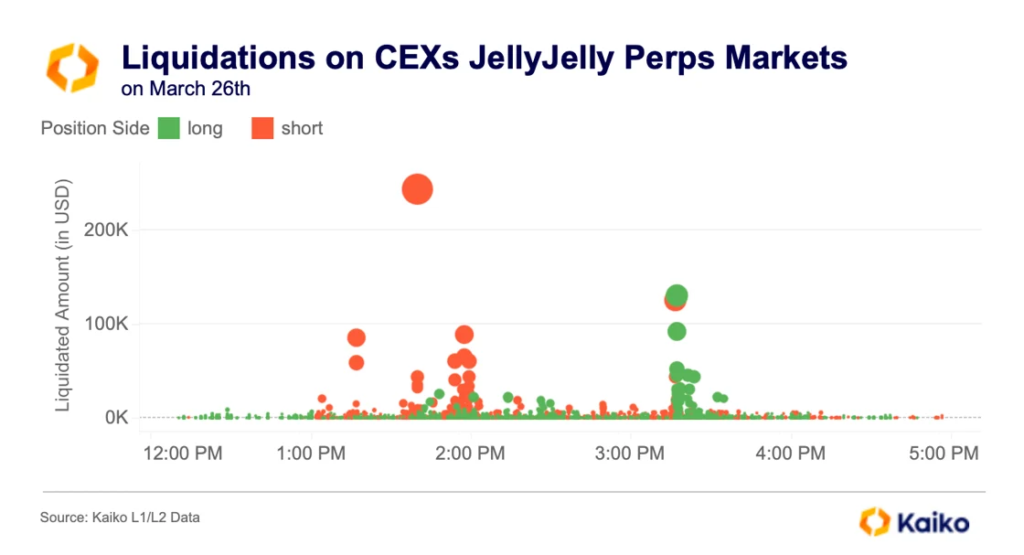
“These actions indicate a carefully planned attack. On-chain data show the perpetrator began test transactions on Hyperliquid at least ten days before the 26 March attack, likely to hone the strategy,” the researchers concluded.
Hyperliquid later halted trading in JELLYJELLY contracts by validator decision due to “suspicious market activity”. The whale managed to withdraw about $6.2m.
A watchful community
The crypto community had already flagged peculiarities on Hyperliquid. Weeks before the attack, EmberCN analysts recorded abnormal behaviour by several large traders—possibly a stress test of the liquidation mechanism.
Experts at 10x Research noted that Hyperliquid’s high transparency opened the door to a kind of crowd-led “whale hunt” using leverage—to force liquidations. The trend, they argued, could materially shift the market balance.
One example came on 16 March, when a user going by CBB called on the community to liquidate a large trader who had opened a 4,442 BTC short with 40x leverage. After coordinated action, bitcoin rose 2.5%, and the whale had to increase the position to 6,210 BTC (~$524m) to avoid liquidation.
Analysts drew parallels with GameStop, when retail investors teamed up against hedge funds. A similar “people’s hunt” could become a new crypto-trading motif, where platform transparency lets small players influence large investors’ actions.
Even manipulators get burned
A year ago a group of MEV bots profiting from backrunning lost over $25m to a rogue validator.
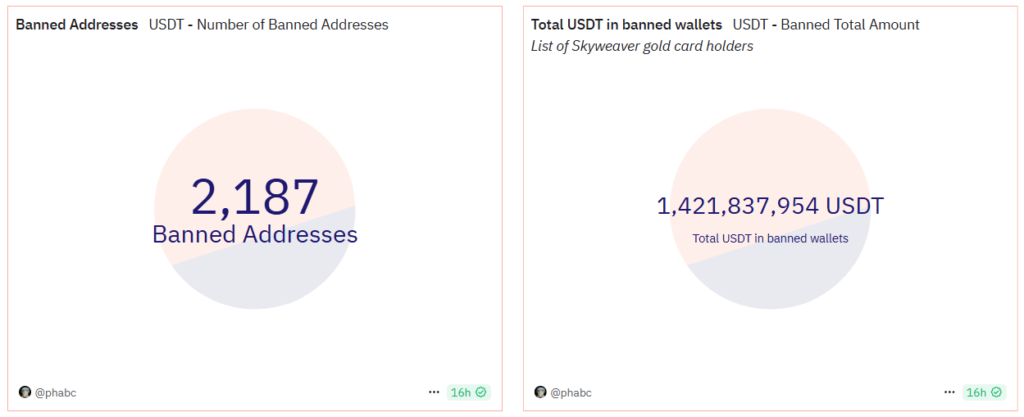
According to CertiK, the attacker swapped out recipient addresses in a transaction bundle. Instead of profits, the bots “forwarded” Wrapped BTC (WBTC), Ethereum (WETH) and the USDC, USDT and DAI stablecoins to the attacker’s wallets.
Almost immediately after the incident, Tether added one related address to its blacklist—holding roughly $3m in assets.
The move drew a wave of criticism on X. Users questioned the decentralisation of the market’s biggest stablecoin.
“They said ‘money of the future’… Got mad over a random MEV mistake… Straight to the blacklist,” wrote one user.
A representative of Cryptonary asked how such wallets are blocked.
“What does a blacklisted stablecoin address look like? Is it just added to a list or are any sanctions imposed?” the post read.
In September last year an “unlucky” MEV bot took out a $11.7m flash loan to attempt a sandwich attack—only to net $20.
The target was a user swapping $5,000 of Shuffle (SHFL) into WETH. Slippage was about 2%.
The bot executed 14 transactions across the Balancer, Aave and Uniswap protocols. After gas, the final profit was just over $20.
“Unlucky,” concluded Arkham Intelligence researchers.
Commenters wryly noted that in today’s market even an MEV bot can’t make more than $20.
How not to be duped
The DeFi Report founder Michael Nado offered a few tips on avoiding MEV bots when using DEXs:
- Reduce the slippage tolerance on your transactions.
- Don’t use Uniswap. Switch to CowSwap or another aggregator that can deliver better execution and prevent MEV.
- Use a custom RPC that doesn’t broadcast your transactions publicly.
Many projects aim to curb MEV’s impact on Ethereum. The best known—Flashbots—is a research outfit building tools to mitigate the negative effects of Maximal Extractable Value and reduce network risk.
Some wallets are adding built-in protections against MEV. For example, MetaMask introduced Smart Transactions, which uses a “virtual mempool” to stage operations before they hit the blockchain, helping prevent front-running and other MEV attacks.
The feature targets bot strategies and offers instant transaction simulation, allowing users to preview outcomes and reduce gas costs.
“Currently up to 15% of transactions revert, meaning users spend around 47,000 ETH each year on operations that accomplish nothing. That’s on top of the 124,000 ETH extracted by MEV bots that read users’ transactions and front-run them for profit. In total, that’s over $440m in annual losses,” the MetaMask team said.
The feature was developed with the Special Mechanisms Group at ConsenSys.
Smart Transactions is opt-in—the user decides whether to enable it and can revert to regular transactions at any time. MetaMask does not charge for the feature.
In 2022 the 1inch Network team introduced RabbitHole, a tool to shield MetaMask users from sandwich attacks.
It acts as a proxy between the wallet and Ethereum validators, letting swap transactions bypass the mempool. To make it work, 1inch integrated products from Flashbots, BloXroute, Eden and Manifold.
Conclusions
Despite adverse market conditions, DeFi keeps gaining ground, offering innovative financial instruments without intermediaries. Yet the young and still relatively small sector remains vulnerable to attacks and manipulation.
Recent incidents on Uniswap and Hyperliquid laid bare the fragility of low-liquidity tokens and weaknesses in liquidation mechanics. The analysis suggests that manipulation is often directly or indirectly amplified by large centralised exchanges, further distorting price formation and heightening trader risk.
Against this backdrop, the community needs to build more tools to bolster trading transparency and shrink avenues for manipulation. Only then can the ecosystem reach its next stage of maturity and win the confidence of both institutions and retail users.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


