
Fake on-chain sleuths prey on hack victims, an AI ‘journalist’ dupes the press, and other cybersecurity stories
The week’s key cybersecurity stories.
We have collected the most important cybersecurity news of the week.
- Fake on-chain sleuths steal remaining funds from victims of crypto theft.
- The media fell for an AI “journalist”.
- Meta is suspected of accessing photo galleries without user consent.
- Researchers hid a trojan in an AI image.
Fake on-chain sleuths are stealing what remains from crypto-hack victims
In August the FBI warned of fraudsters posing as bogus crypto law firms. Under the guise of sham asset-recovery services, the scammers stole money and personal data from clients.
According to the statement, the primary targets are victims of crypto hacks trying to reclaim stolen funds.
Law enforcement said the fraudsters used a wide array of manipulative tactics, playing on victims’ desperation and creating a false sense of security by impersonating government representatives or claiming cooperation with them. The reputations of people and organisations whose names were misused were also harmed.
When choosing help to recover cryptocurrency, the FBI advised watching for:
- references to fictitious government or regulatory bodies, such as the nonexistent International Financial Trading Commission (INTFTC);
- requests for payment in cryptocurrency or gift cards;
- knowledge of exact amounts and dates of previous bank transfers;
- claims that the victim is supposedly on a list of people scammed and can get their money back through “legitimate channels”;
- referrals to a “cryptocurrency recovery law firm”;
- assertions that funds are in a foreign bank and demands to open an account there. The domain or site may look legitimate but in fact be a fake platform to extend the scam;
- invitations to a group chat in a messenger app allegedly “for client secrecy and safety” with “foreign bank operators and lawyers”. They may demand fees to verify identity and ownership;
- refusal or inability to provide identification or a licence, refusal to turn on a camera or hold a video meeting;
- demands to send payment to a third party supposedly for secrecy and safety.
An AI “journalist” duped the media
Press Gazette noted that at least six outlets, including Wired and Business Insider, have in recent months removed articles from their sites. The reason, it reported, was that pieces published under the name Margot Blanchard were generated by AI.
In May Wired ran a story titled “They fell in love playing Minecraft. Then the game became their wedding venue.” It mentioned Jessica Hu, a 34-year-old clergywoman from Chicago known as a “digital officiant” on Twitch and Discord. The outlet could not verify her existence and, weeks later, removed the piece for failing to meet editorial standards.

According to Press Gazette, in April Business Insider published two Blanchard essays. Last week the outlet deleted them.
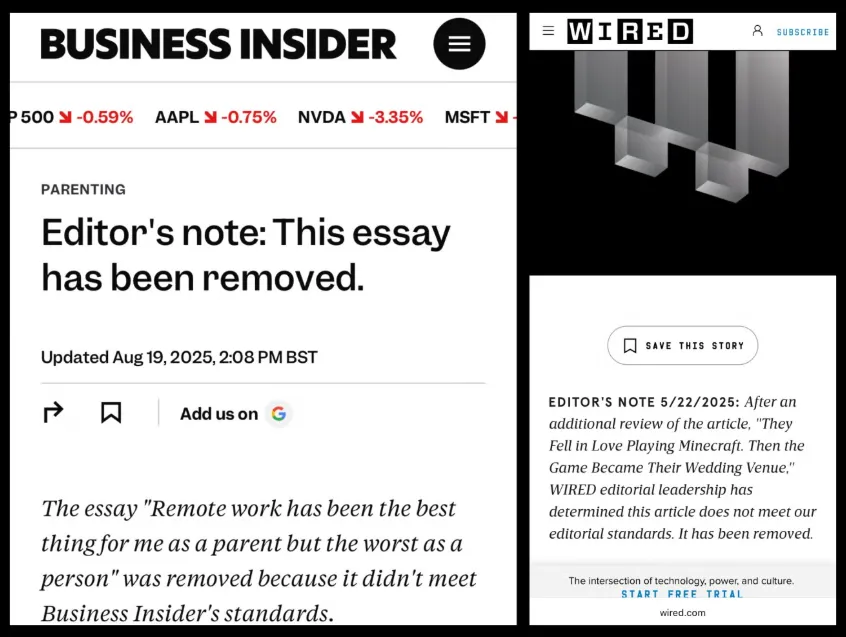
On 21 August Wired’s leadership acknowledged the error:
“If any publication should recognize AI grifters, it’s Wired. And in fact we usually do… Unfortunately, one slipped through.”
The outlet explained that on 7 April an editor received a pitch from one Margot Blanchard about “the growing popularity of hyper-niche internet weddings”. The email bore “all the hallmarks of a great Wired story”. After a standard exchange about scope and fee, the editor commissioned the piece, which ran on 7 May.
Wired said that within days the newsroom realised the author could not provide sufficient information about herself. The journalist insisted on payment via PayPal or cheque.
Further investigation showed the story was fabricated.
“We made mistakes: the story did not undergo proper fact-checking and was not edited by a senior editor[…] We acted quickly when we discovered the deception and took steps to prevent a recurrence. In the new era every newsroom must be prepared for this.”
Press Gazette said the first to flag irregularities was Dispatch editor Jacob Furedi. He reported receiving a pitch from Blanchard about “Gravemont, a closed mining town in rural Colorado that had been repurposed into one of the most secretive death-investigation training centres.” He asked the supposed freelancer to show records requests; she ignored the request.
Meta is suspected of accessing galleries without user consent
Meta analyses and stores photos from devices. According to ZDNET, some Facebook users found two enabled options in Meta app settings that give the company access to the gallery. The feature is intended to use AI to offer “personalised creative ideas” such as travel montages and collages.
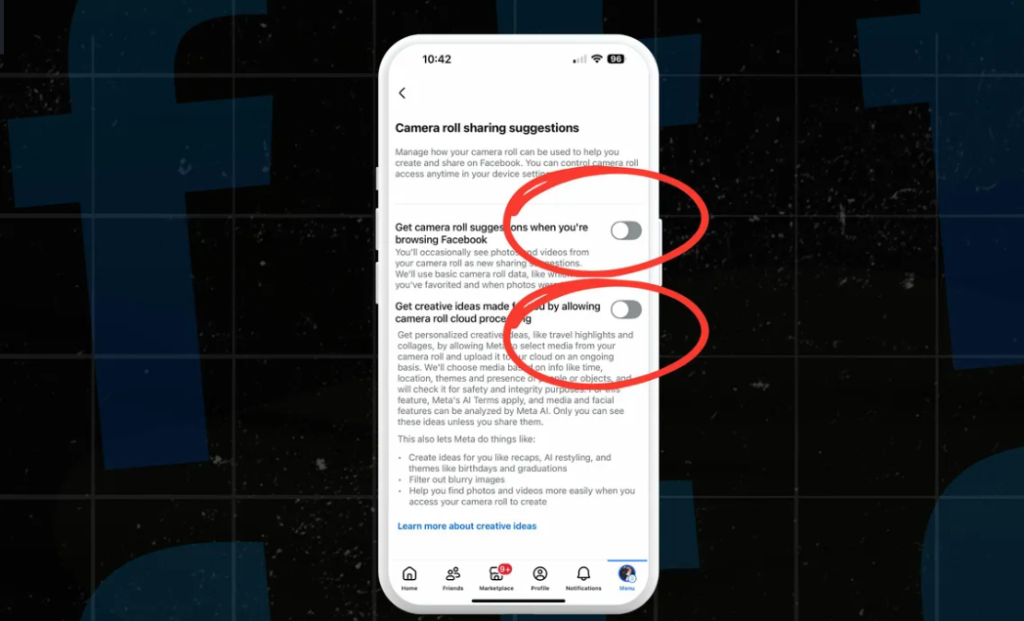
Media reported that the options for AI features called “suggestions to use photos from the gallery” are enabled for users who say they did not consent.
If a user taps “allow”, they agree to Meta’s AI terms and to analysis of “media and facial features”. Facebook then uses images from the gallery (including creation dates and the presence of people or objects) to suggest collages, themed albums, recap posts or AI-modified versions of images.
Researchers hid a trojan in an AI image
Researchers at Trail of Bits developed a new attack to steal user data. The method embeds malicious commands in images that are processed by AI systems before being passed to a large language model.
The idea is to use full-size images with “invisible” instructions that emerge when quality is reduced by resizing algorithms. When uploaded to AI systems, such images are automatically downscaled to improve performance and save resources.
Depending on the system, image-resizing algorithms may lighten the image using nearest-neighbour, bilinear or bicubic interpolation.

In Trail of Bits’ example, when downscaled bicubically the dark areas of the malicious image turn red and hidden text appears in black.
From the user’s perspective nothing unusual happens, but in fact the model executes hidden instructions that can lead to data leakage or other risky actions.
The researchers confirmed their method applies to:
- Google Gemini CLI;
- Vertex AI Studio (with Gemini backend);
- the Gemini web interface;
- the Gemini API via llm CLI;
- Google Assistant on an Android phone;
- Genspark.
Google will ban software from unverified developers
On 25 August Google announced it will soon stop allowing software from unverified developers in Google Play. A new Android protection system will block the installation of malicious apps when downloading from third-party sources.
“While the threat is more associated with third-party sources, the developer verification requirement now applies to apps from Google Play as well as apps in third-party stores,” the team added.
Early access to verification opens in October, and in March 2026 the system will become available to all Android developers. In September the mandatory identity verification requirement will take effect for Brazil, Indonesia, Singapore and Thailand, and in 2027 worldwide.
Also on ForkLog:
- ZachXBT called Ripple, Cardano and Hedera “insiders’ enrichment schemes”.
- US banks outpaced the crypto industry by the volume of laundered funds.
- The number of traders on Solana fell by 80% amid a rise in rug pulls.
- Scammers used Claude for vibe hacking.
- 112 crypto companies urged the US Senate to protect developers.
- A fake trader from Odesa stole $1m from acquaintances.
- CertiK’s founder called the war with hackers “endless”.
- In Ufa, authorities shut down an illegal crypto cash-out scheme worth 3bn rubles.
- Pavel Durov called his arrest in France “a legal absurdity”.
- A South Korean was charged with laundering $50m by converting bitcoin into gold.
What to read this weekend?
Why trading platforms block accounts, how a “clean” transaction can still lead to frozen funds, and how deeply AML systems trace transfer chains? In a guest piece for ForkLog, Fedor Ivanov—director of analytics at the company “Shard”—explains.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


