Ledger data leak exposes details of a million hardware-wallet users
The Ledger hardware-wallet user database, stolen in June 2020, has been made publicly accessible via the Raidforums forum. About 1 million email addresses, 272,000 residential addresses and phone numbers leaked online.
A Twitter user going by the handle OMGBTC tallied the number of affected Ledger hardware-wallet customers by country.
Casa’s chief technology officer Jameson Lopp noted that only 1% of users protected their personal information with a PO Box or private mailbox.
1% of the Ledger customers from the recent leak went to the trouble of protecting their home address with a PO Box or private mailbox.
— Jameson Lopp (@lopp) December 20, 2020
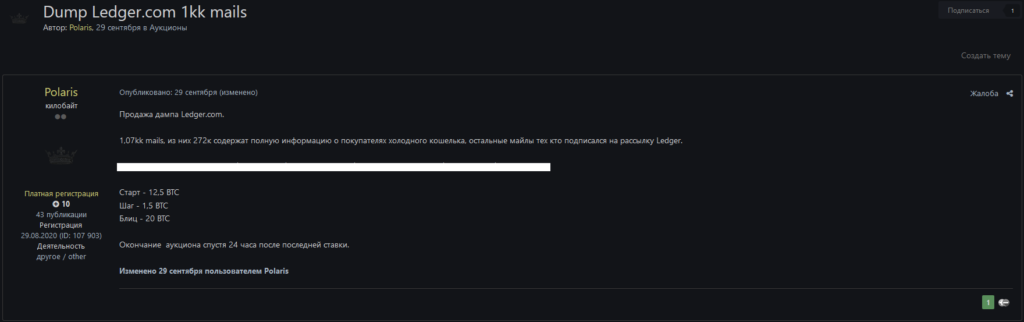
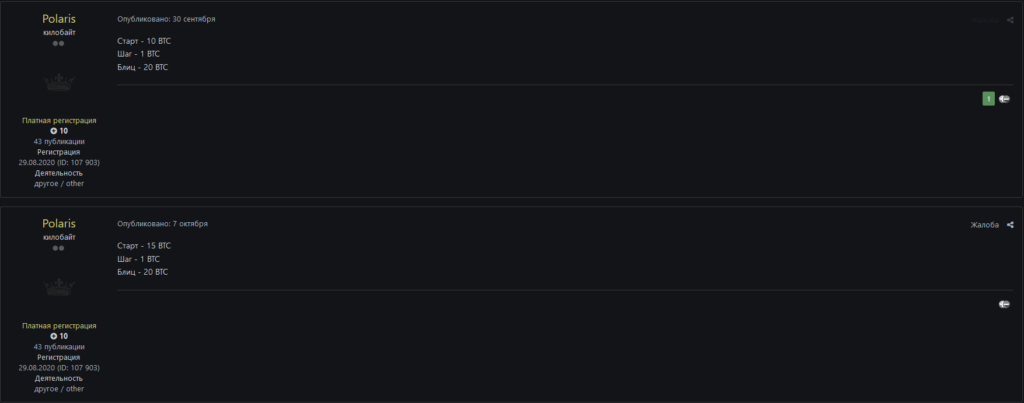
In late October, a user going by Polaris posted the database on the hacker forum exploit.in. Initially, he set the price at 12.5 BTC, but later repeatedly changed it.
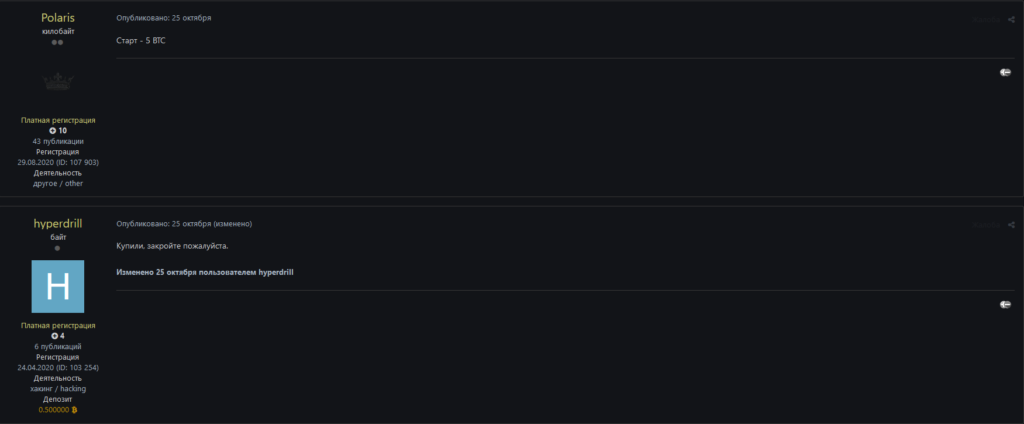
Screenshots from the exploit.in forum.
The buyer was a user named hyperdrill, who presumably paid 5 BTC for the data. However, on December 20, another user posted the same database on the forum at cheaper prices — the starting price was 1.5 BTC.
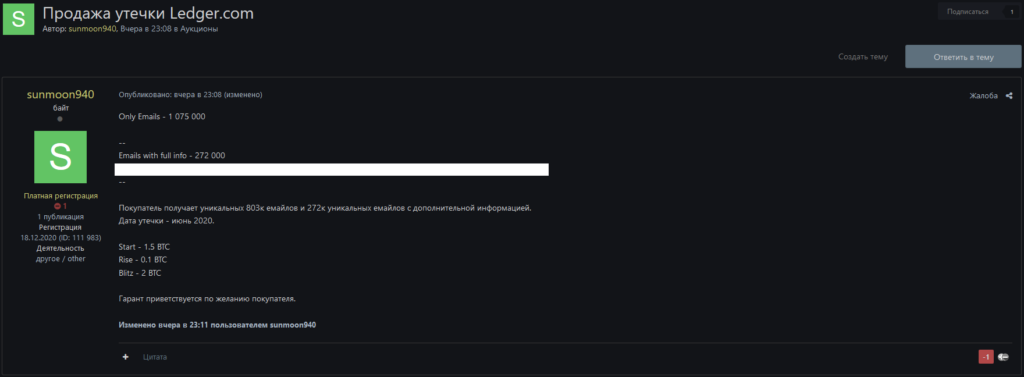
Screenshot from the exploit.in forum.
“I paid a lot for this database and promised not to leak it, but the owner did not keep his word. So I am posting everything for free,” wrote hyperdrill.
Ledger representatives suggested that this was the same database that leaked in June 2020.
Today we were alerted to the dump of the contents of a Ledger customer database on Raidforum. We are still confirming, but early signs tell us that this indeed could be the contents of our e-commerce database from June, 2020.
— Ledger (@Ledger) December 20, 2020
“To say we deeply regret this situation would be an understatement. Since July we have taken every possible measure to make Ledger more secure in the future,” the company said.
Some users reported receiving emails about wallet deactivations and a phishing link. Ledger urged everyone not to share recovery data to regain access.
MOST IMPORTANTLY: Never share the 24 words of your recovery phrase with anyone, even if they are pretending to be a representative of Ledger. Ledger will never ask you for them. Ledger will never contact you via text messages or phone call.
— Ledger (@Ledger) December 20, 2020
The Ledger team said they are monitoring phishing campaigns in a dedicated section on their website.
We have set up a webpage sharing the anatomy of these phishing attacks so you can avoid falling for them and report any new attacks you receive: https://t.co/x9NCMbvhEO
— Ledger (@Ledger) December 20, 2020
Update: Users have started receiving letters threatening physical harm. The attackers are demanding $500 in bitcoin to back off.
In the data trail: The breach occurred on June 25 — an unknown actor gained access using an API key. Wallet developers learned of the vulnerability on July 14 from an external researcher.
In late October, Ledger users complained about phishing email campaigns demanding an urgent update.
In December, attackers under the name of Ledger CEO Pascal Gauthier sent out new notices to customers with phishing links. As ForkLog found, on December 11 one of the hackers’ addresses held 60.19 BTC.
Subscribe to ForkLog news on Telegram: ForkLog Feed — full news feed, ForkLog — the most important news and polls.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!