
User Hacks North Korean Hacker
An unidentified user has hacked the account of an IT specialist from North Korea, who was part of a small hacker group linked to the theft of $680,000. This was revealed by blockchain detective ZachXBT.
1/ An unnamed source recently compromised a DPRK IT worker device which provided insights into how a small team of five ITWs operated 30+ fake identities with government IDs and purchased Upwork/LinkedIn accounts to obtain developer jobs at projects. pic.twitter.com/DEMv0GNM79
— ZachXBT (@zachxbt) August 13, 2025
Six North Korean citizens created over 30 fictitious identities to secure positions in crypto projects. They purchased fake documents and accounts on LinkedIn and Upwork, posing as experienced blockchain developers. One even passed an interview at Polygon Labs for a full-stack engineer position, claiming experience with OpenSea and Chainlink in their resume.
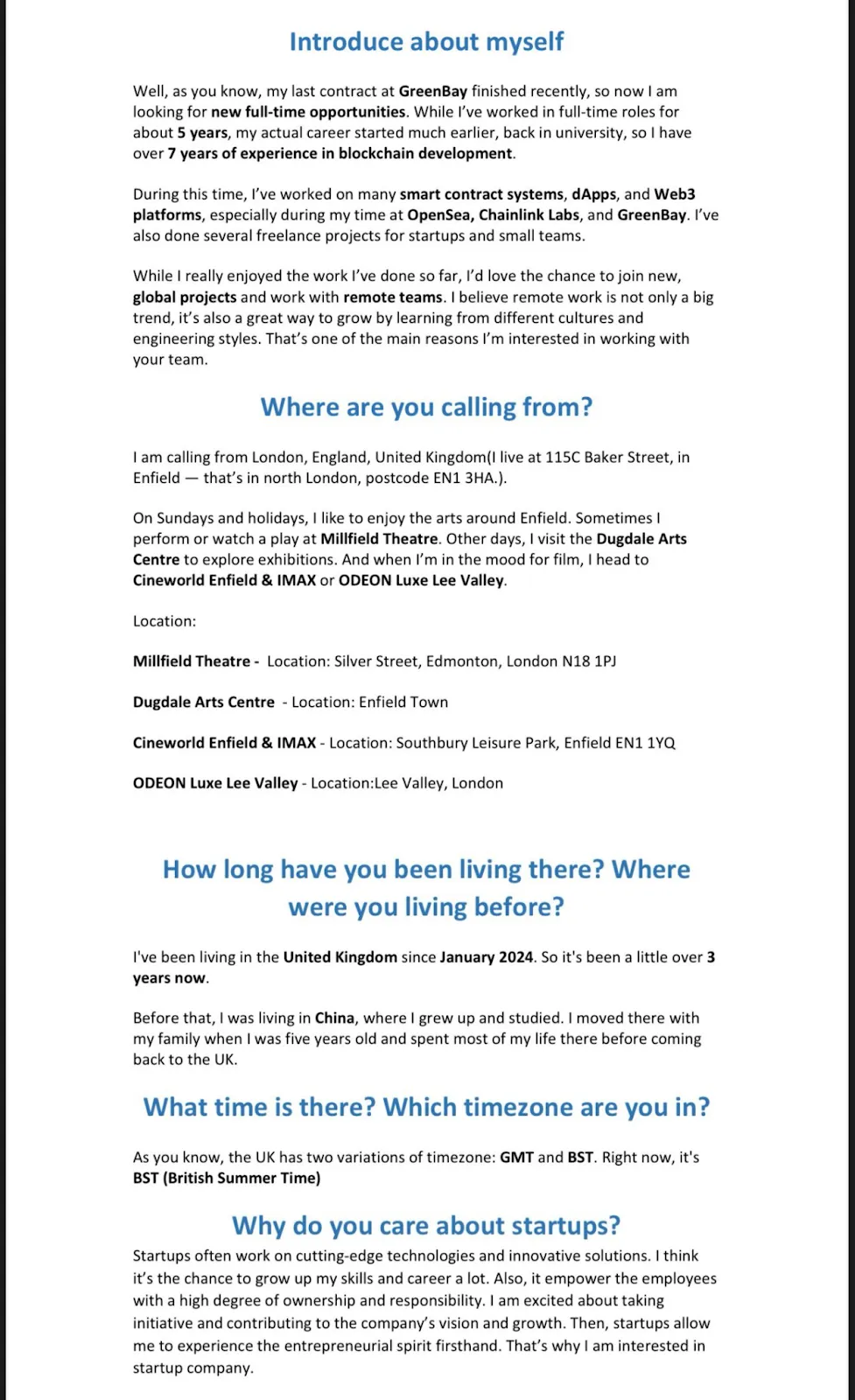
“My professional experience in blockchain development spans over seven years (including university), although I have officially worked full-time for about five years. During this period, I developed smart contract systems, decentralized applications, and Web3 platforms, including at OpenSea, Chainlink Labs, and GreenBay,” reads the script used for the fake identity named Henry Chan.
The hackers conducted their work using software for remote access, AnyDesk, and concealed their location via VPN. They used Google services for task planning and communication. In May, the operational expenses of the perpetrators amounted to $1489, covering computer rentals and software subscriptions.
The cybercriminals executed transactions through the Payoneer service. One of the wallets is linked to a group involved in the June attack on the Favrr marketplace. During this breach, the perpetrators stole $680,000.
Search queries accessed included questions about deploying ERC-20 on Solana and leading AI companies in Europe. However, the most frequent was: “how to tell if they are North Koreans?”
ZachXBT also highlighted that the search history showed active use of Google Translate with translations from Korean to English via a Russian IP.
The blockchain detective urged crypto companies to better vet candidates, emphasizing that such operations are not complex. He noted that vulnerabilities are exacerbated by overwhelmed HR departments.
“The main issue in combating DPRK IT workers (DPRK ITWs) is the lack of cooperation between government agencies and the private sector. Another challenge is the negligence of recruiting teams, who start arguing upon receiving warnings. The methods of DPRK ITWs are not sophisticated, but they are persistent due to their massive presence in the global job market,” he noted.
North Korean Hackers at Binance
Binance’s Chief Security Officer Jimmy Su told Decrypt that the exchange receives fake resumes from North Korean hackers daily. According to him, this has been ongoing for years, but recently the perpetrators’ tactics have become more sophisticated.
Previously, they sent template applications with Japanese and Chinese surnames. However, now the cybercriminals use deepfakes and voice modulators in interviews, posing as developers from Europe or the Middle East.
Suspicion arises from slow internet connections. According to Su, due to the use of translators and other simulators, the perpetrators’ responses are delayed by several seconds.
“The only reliable way to verify a candidate is to ask them to cover their face with their hand. The deepfake usually ‘breaks,’ but we do not disclose all methods to avoid aiding the hackers,” he added.
A Binance representative stated that the exchange has never hired North Korean state agents but continues to monitor employees for suspicious behavior. Specialists from North Korea often rank among the top performers—likely due to working multiple shifts. If someone does not take breaks even for sleep, it is a typical sign of a connection to Lazarus, Su noted.
He added that some companies ask candidates to speak negatively about North Korean leader Kim Jong Un during interviews, which is prohibited in the country. Other details were not disclosed by the Binance representative for security reasons.
In addition to employment attempts, Lazarus also:
- infect NPM libraries—adding malicious code to open repositories, which is embedded in projects;
- conduct phishing “interviews”—posing as recruiters, offering to update Zoom via a fake link, and infecting victims’ devices with malware.
In February, the Bybit exchange lost $1.46 billion in a hack. Cybersecurity experts blamed the Lazarus group for this.
In July, the Indian trading platform CoinDCX suffered a loss of $44.2 million. The cyberattack was also attributed to North Korean hackers.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


