
Russian bitcoin malware, data leak at thousands of US corporations, and other cybersecurity events
We’ve gathered the week’s most important cybersecurity news.
- Data from the Pentagon and thousands of corporations lay exposed for five months.
- Malware linked to the GRU blamed for attacks on cryptocurrency wallets.
- The DreamBus botnet returned after a two-year hiatus and continued mining Monero.
- A spying clone of Signal landed in app stores.
Pentagon and thousands of corporations’ data publicly accessible for five months
The U.S. National Security Council (NSC) acknowledged an unprecedented breach in which, since January, credentials of about 2,000 companies, including government agencies and large corporations, were exposed. This was disclosed by researchers at Cybernews.
The NSC, a non-profit, conducts security training. The site has registered nearly 55,000 users.
Cybernews researchers discovered a platform subdomain presumably used during development. It posted a list of all online catalogs, enabling access to most server files, including a database backup with users’ emails and hashed passwords.

Among the victims were the U.S. Department of Justice, the U.S. Navy, the FBI, the Pentagon, NASA, and Shell, BP, Intel, IBM, AMD, Boeing, Pfizer, Ford, Toyota, Volkswagen, Tesla, Amazon, Coca-Cola and many others.
The data were publicly accessible for five months, after Internet of Things search engines first indexed the breach on January 31, 2023. NSC fixed the issue following Cybernews’s report.
The breach could have been used to gain access to corporate networks for deploying ransomware or stealing internal documents.
Malware linked to the GRU blamed for attacks on crypto wallets
New Russian malware, Infamous Chisel, has been used to target cryptocurrency wallets and messaging apps. This is stated in a joint report by the U.K. National Cyber Security Centre (NCSC), the FBI, the NSA and CISA.
Experts attribute the malware’s operation to the Sandworm hacker group, tied to Russia’s military intelligence.
Infamous Chisel provides persistent access to the compromised Android device and allows copying certain application directories, including those related to the Web3 browser Brave, the Binance and Coinbase apps, the Trust wallet, Telegram and Discord.
According to the report, the malware developers did not pay much attention to concealing the malicious activity of its components.
The DreamBus botnet returned after a two-year hiatus and continued mining Monero
DreamBus, which had shown no activity since 2021, has resumed targeting Linux users to install the hidden XMRig miner for Monero mining. This was highlighted by Juniper Threat Labs.
DreamBus exploits a recently patched vulnerability in the Apache RocketMQ messaging app that allows for remote code execution.
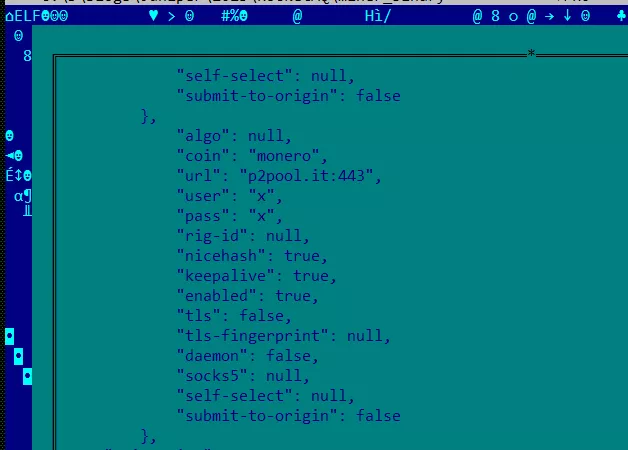
While mining Monero remains the main objective, the modular nature of the malware allows extending its capabilities and potentially stealing confidential chats.
Spyware clone of Signal found in app stores
ESET researchers found in Google Play and Samsung Galaxy Store an application aimed at stealing messages from the Signal messenger.
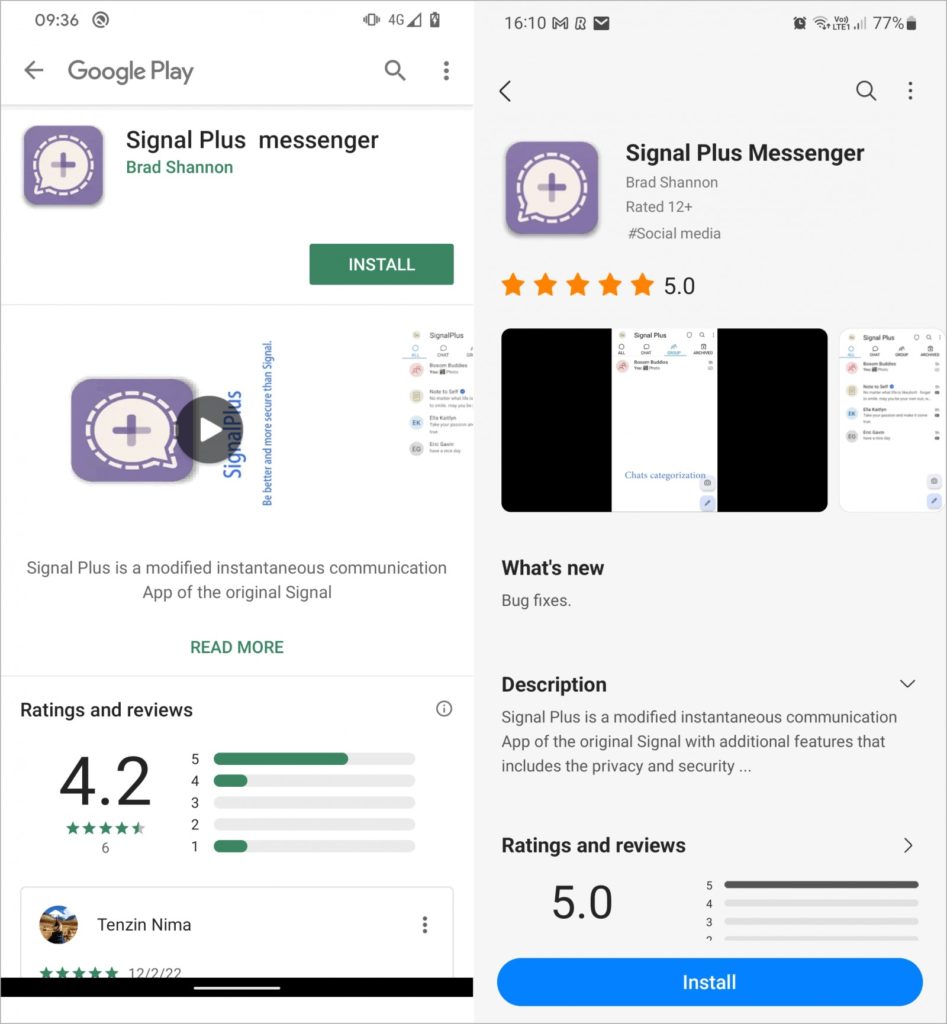
The Signal Plus Messenger clone is infected with BadBazaar spyware that can track the device’s precise location, steal call logs and SMS, record calls, take photos with the camera, and steal contact lists, files and databases.
In addition, the fake app’s features allow the attacker to tie the victim’s Signal account to their device, enabling them to see future messages in chats.
ESET believes BadBazaar was developed by the Chinese hacker group GREF. Its targets include users in Poland, the Netherlands, Ukraine, Spain, Portugal, Germany, Hong Kong and the United States.
Signal Plus Messenger was released on Google Play and Samsung Galaxy in July 2022. Google removed the malware on May 23, 2023; at the time of the report the app remained available in the Samsung Galaxy Store.
Paramount data breach
The American media conglomerate Paramount said that between May and June 2023 unknown parties gained access to its systems, resulting in a data breach affecting about 100 people. The media learned of this only now.
Among the compromised data were names, dates of birth, Social Security numbers or other forms of identification, and some information about the affected person’s relationship with Paramount.
The investigation is being conducted with law enforcement. The media group offered affected users two years of free data-monitoring services.
Also on ForkLog:
- Hackers attacked Russians after Binance restrictions.
- Ronaldinho denied participation in a $61 million crypto scam.
- Blogger exposed a seed phrase on YouTube and lost $60,000.
- Web3 projects lost $1.25 billion year-to-date due to hackers.
- OpenSea accused of blocking users for transacting with Tornado Cash.
- FBI seized nearly $9 million in bitcoins from Qakbot botnet operators.
- Sam Bankman-Fried asked for a temporary release to prepare for trial.
- In Hong Kong, a group was arrested for money laundering $15 million via cryptocurrencies.
- The L2 network Shibarium was relaunched after a major outage.
- Loss from the Balancer hack was estimated at $900,000.
What to read this weekend?
A chapter from the book “Blockchain for Everyone. How Cryptocurrencies, BaaS, NFT, DeFi and Other Newer Financial Technologies Work” by Doctor of Economics Artem Genkin and digital-technology expert Alexei Mikheev. It discusses some fundamental issues, including cybersecurity, that hinder the wide adoption of DLT.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


