What is Monero (XMR)?


1
What is Monero?
Attention! The article is outdated and requires an update.
Monero (XMR) is a privacy-focused cryptocurrency with open-source code, whose protocol implements several transaction-anonymisation techniques: stealth addresses and ring confidential transactions.
On the Monero network, only the transacting parties—and anyone given a special access key—can see the amount and the sender and recipient addresses.
2
Who launched Monero, when and how?
Monero launched in April 2014 under the name BitMonero. Its protocol was based on the code of CryptoNote and Bytecoin. The name was later changed.
The CryptoNote protocol was introduced in 2012 by the developer Nicolas van Saberhagen. He described CryptoNote in “CryptoNote White Paper v 1.0” and “CryptoNote White Paper v 2.0“.
Bytecoin was the first mass implementation of CryptoNote. The project’s reputation was undermined by a premine in which the developers kept 80% of the total supply. Led by Riccardo Spagni, some users created their own version of the coin with zero premine.
Almost all Monero developers use pseudonyms. Only two have revealed their identities—Riccardo “Fluffypony” Spagni and Francisco Cabañas.
The cryptocurrency ranks third after Bitcoin and Ethereum by number of developers, though only a few write code on a permanent basis.
3
Which anonymisation technologies does Monero use?
Ring signatures
In cryptography, a “ring signature” allows a member of a set of signers to sign a message anonymously, without revealing their identity.
In Monero, ring signatures add decoys (mixins) to a transaction in the form of inputs/outputs from previously made transactions. They help obfuscate the trail: it is impossible to determine with certainty which parts are decoys and which are the real funds.
For a long time the option to add decoys to transactions was unavailable and later optional. Users ignored it. This enabled researchers to deanonymise about 64% of all transactions made before September 2017.
Ring Confidential Transactions (RingCT)
The Confidential Transactions technology hides the time, the payment amount and the participating addresses.
RingCT was implemented in Monero in January 2017. Since September 2017 this feature has been mandatory for all transfers. At least ten decoys are automatically added to a transaction.
Stealth addresses
Transactions on the Monero network are executed via unique one-time “stealth addresses” created by senders’ wallets. The coins are sent to that address.
These addresses hide the link between the sender address, the recipient address and any other transactions/addresses.
A recipient does not lose anonymity when receiving many payments to one address, because incoming transfers are routed through different stealth addresses.
Future integration of the Kovri I2P protocol into Monero
The protocol, written in C++ and based on I2P, will route all Monero user traffic (IP and other metadata) through nodes run by anonymous volunteers, akin to Tor.
A user exposes their IP address when making a transaction. Although it is not recorded on the blockchain, real-time network scanning can capture the IP.
4
What types of Monero addresses exist, and what are their keys for?
Monero addresses consist of 95–106 characters and start with the digit 4.
Standard addresses (standard address, raw address) are the technical basis for subaddresses and integrated addresses. They are useful for:
- receiving a block reward in solo mining, as other address types are not supported;
- accepting payments from senders who combine multiple payouts into one (such as mining pools).
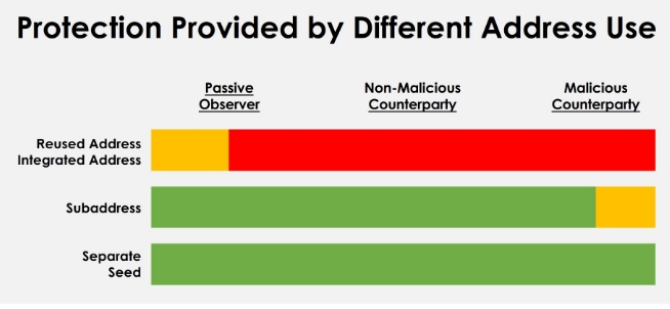
An integrated address is a regular address with an encrypted identifier (ID) embedded. It allows one to distinguish incoming transactions (for exchanges) and payments (for merchants).
A subaddress is generated from a standard address and provides the highest degree of anonymisation.
Subaddresses are stored in groups called accounts within a wallet. Accounts can be labelled, for example “Mining”, “Trading”, and so on.
Keeping several accounts under one mnemonic phrase (SEED) is convenient when restoring a wallet. You also know exactly who sent you funds and for what. Create a new address for every incoming payment.
Two wallet versions are available for download: a command-line (CLI) version and a graphical interface (GUI) version, recommended for most users.
5
What are private and public keys for?
The public view key reveals the stealth addresses related to a transaction.
The public spend key is used by the sender’s wallet to generate a public key for the stealth address.
The private view key is required to view information about an address’s transactions. If you share it, you allow someone else to see the amounts and the history of all incoming transactions. It will not show outgoing transactions correctly unless you also provide the key images associated with them.
The private spend key grants full access to the address and allows the coins at it to be spent.
6
What are Monero’s advantages?
- A dynamic block size keeps fees low and confirmations fast during a spam attack. If there is room in the block, there is no transaction queue. The network monitors the number of transactions in the last 100 blocks. If the count rises, the block size increases, but by no more than twice the current size.
- Tail emission provides funding in which a fixed money supply ceases to be fixed over time. To compensate for “lost” coins and incentivise miners, after May 2022 the network will add 0.6 XMR every two minutes to the base money supply (18.4 million coins). Monero is programmed to reduce the block reward gradually, similar to Bitcoin.
- Multilingual mnemonic phrases (SEED phrases) are useful if an attacker finds them on a piece of paper. Even an experienced thief (or investigator) may not realise it is a SEED if the words are not in English.
7
How easy is it to attack Monero?
In 2019 researchers discovered the “Janus attack”. Imagine your account has two subaddresses. They are also posted on public forums.
You do not want one of the addresses associated with you, while someone wants to prove such a link. They agree a trade with you and then send the payment to the other address. If you fail to notice that the payment arrived at the wrong address and confirm receipt, you reveal yourself.
There is also a transactional-flood attack. It consists of sending a huge number of small transactions to compromise the anonymity of other users by controlling the decoys. The cost of the attack is estimated at $1.7m.
8
Why has Monero been delisted on several exchanges?
Under pressure from the FATF and local regulators, exchanges are removing privacy coins from listings in an attempt to ensure compliance.
Monero transactions cannot be deanonymised even with tools such as Chainalysis and Crystal Blockchain, which makes it hard for exchanges to purge grey capital.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!