
Cybersecurity Updates: Bitcoin Botnet Enhancements and GRU Spy Network Disruption
We have compiled the most significant cybersecurity news of the week.
- Bitcoin blockchain-based malware gains a new feature.
- The FBI halts operations of the Warzone RAT trojan and Moobot botnet.
- Leader of the hacker group JabberZeus pleads guilty.
- New malware caught secretly scanning faces for deepfake creation.
Bitcoin Blockchain Botnet Gains New Feature
The modular botnet Glupteba has acquired a previously undocumented Unified Extensible Firmware Interface loader feature, allowing it to control processes in infected operating systems and providing additional stealth. This was reported by experts from Unit42, the incident response division of Palo Alto Networks.
#Glupteba is a modular #malware that can perform #CredentialStealing, #cryptojacking and more. Distributed through a pay-per-install system, a campaign from 2023 revealed a novel feature — a UEFI bootkit. We analyze both the bootkit and the campaign. https://t.co/pLxM5rCBMO pic.twitter.com/L1LZHyroKe
— Unit 42 (@Unit42_Intel) February 12, 2024
The malware uses the Bitcoin blockchain as a backup command-and-control center, making it resilient to shutdown attempts.
Glupteba has been known since the early 2010s and is a full-featured grabber and backdoor capable of cryptocurrency mining and deploying proxies on infected hosts.
Additionally, it can steal digital assets, credit card data, Google accounts, and other programs, as well as use routers for remote administrative access.
The botnet’s developers continually refine its multi-stage infection chain.
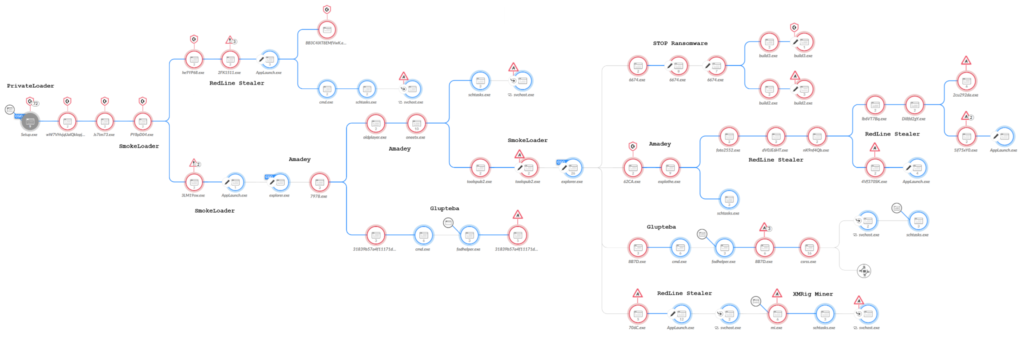
In 2023, Glupteba affected various sectors in Greece, Nepal, Bangladesh, Brazil, South Korea, Algeria, Ukraine, Slovakia, Turkey, Italy, and Sweden.
FBI Halts Warzone RAT Trojan and Moobot Botnet
The FBI seized four domains and the main website of the Warzone RAT remote access trojan, and arrested two individuals involved in its operations.
27-year-old Daniel Meli from Malta has been charged with unauthorized damage to protected computers and conspiracy to infiltrate information systems.
31-year-old Prince Onyeoziri Odinakachi from Nigeria is accused of providing customer support to cybercriminals who purchased access to Warzone RAT from June 2019 to March 2023.
Meli faces up to 25 years in prison, while Odinakachi could face up to 15 years. Each may incur a fine of at least $500,000.
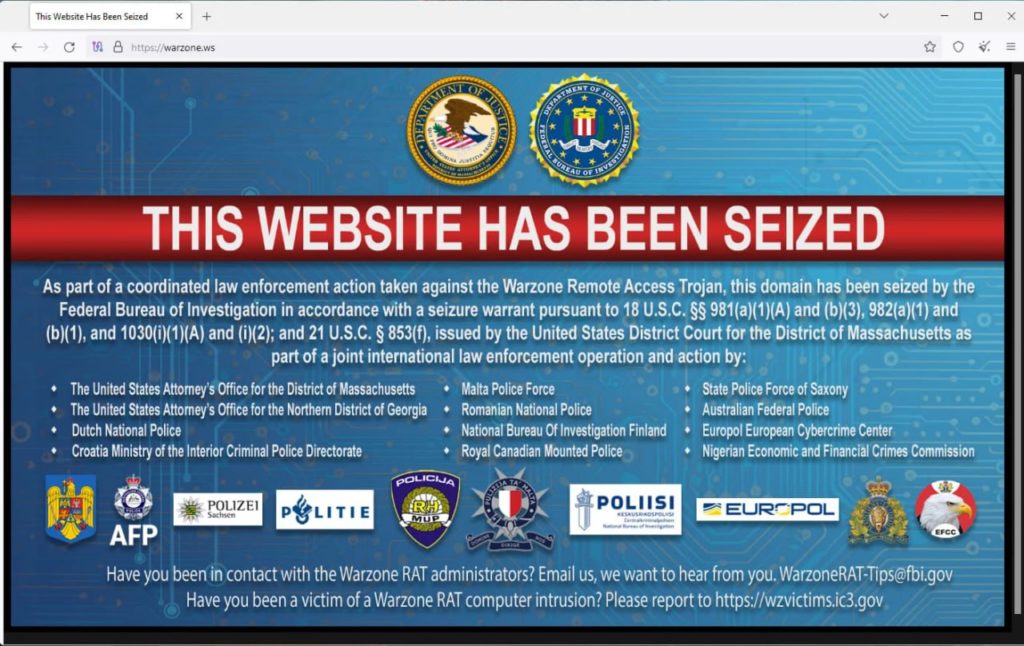
Created in 2018, Warzone RAT allowed hidden access to remote desktops, theft of cookies and passwords, keystroke logging, webcam video recording, and process management within the system. The malware’s server infrastructure was located in Canada, Croatia, Finland, Germany, the Netherlands, and Romania.
Additionally, the FBI dismantled the Moobot botnet, consisting of hundreds of routers, used by the Russian General Staff’s Main Intelligence Directorate as a global cyber espionage tool.
The hackers targeted government and military structures, as well as security services and corporate organizations in the US and other countries.
Leader of Hacker Group JabberZeus Pleads Guilty
Ukrainian citizen Vyacheslav Penchukov admitted his leadership role in the hacker groups Zeus and IcedID.

Before his arrest in Switzerland in November 2022, he was on the FBI’s most wanted cybercriminals list for nearly a decade.
Last year, Penchukov was extradited to the US, where he is held responsible for infecting thousands of computers with malware and extorting millions of dollars.
The court hearing is scheduled for May 9. Penchukov faces up to 40 years in prison.
New Trojan Caught Secretly Scanning Faces for Deepfake Creation
Group-IB specialists discovered the GoldPickaxe trojan, which spreads under the guise of government applications and popular mobile services.
The #GoldDigger family grows: Group-IB’s TI Unit finds GoldPickaxe.iOS, the first #iOS #Trojan harvesting #FacialRecognition data for unauthorized bank access, targeting #APAC. It is linked to the GoldDigger family discovered last October. Learn more: https://t.co/pC4AAubb47 pic.twitter.com/APRROpufHb
— Group-IB Threat Intelligence (@GroupIB_TI) February 15, 2024
The malware operates semi-autonomously. It can discreetly photograph the victim’s face, intercept incoming SMS, and request identification documents through social engineering. This information is later used by attackers to create deepfakes or gain unauthorized access to bank accounts.
The trojan has versions for iOS and Android. So far, the attacks, which began in October 2023, mainly target the Asia-Pacific region. However, the methods used could be effective worldwide.
Data of 200,000 Facebook Marketplace Users Leaked on Darknet
An unknown hacker under the alias IntelBroker has posted 200,000 records containing confidential information of Facebook Marketplace users on a hacker forum, reports Bleeping Computer.
The leaked data includes names, phone numbers, email addresses, Facebook IDs, and social media profile information. All of this can be used for further phishing attacks or SIM card swapping.
According to available information, the leak was obtained in October 2023 as a result of a breach of a third-party contractor managing Facebook’s cloud services.
Meta has not commented on the incident.
Canada Bans Import and Sale of Flipper Zero
Canada’s Department of Innovation, Science and Economic Development announced a ban on the import, sale, and use of the Flipper Zero device, along with other hacking gadgets, as part of efforts to combat car theft.
According to the Canadian government, approximately 90,000 cars are stolen annually in the country (one every six minutes).
The portable programmable tool Flipper Zero allows interaction with various hardware and digital equipment through multiple protocols, including RFID, radio, NFC, infrared, and Bluetooth.
Users have repeatedly demonstrated how it can unlock cars, open garage doors, activate doorbells, and clone various digital keys.
Flipper Devices, the developer of the device, told Bleeping Computer that the gadget is useless for stealing cars manufactured in the last 24 years, as they use rolling codes.
“Moreover, to intercept the original signal, one would need to actively jam the owner’s signal, which the Flipper Zero hardware cannot do. Flipper Zero is designed for testing and developing security systems, and we have taken necessary precautions to ensure the device cannot be used for criminal purposes,” the developers added.
Also on ForkLog:
- CoinMetrics assessed the cost of a 51% attack on Bitcoin and Ethereum.
- Bitcoin mixer YoMix replaced sanctioned Sinbad for North Korean hackers.
- A vulnerability was found in the Trust Wallet app for iOS.
- OpenAI blocked state-sponsored hackers from accessing ChatGPT.
- Chainlink and Telefónica to enhance Web3 application security.
- Hackers breached the X-account of the Notcoin project.
- The MINER experimental token team reported an attack on the smart contract.
- Crypto casino Duelbits lost $4.6 million in a hack.
- PlayDapp gaming platform suffered $290 million in damages from two exploits.
- A trader lost over $100,000 purchasing an ERC-404 token.
- Vitalik Buterin provided guidance on detecting deepfakes.
Weekend Reading Suggestions
We publish an excerpt from Laura Shin’s book “The Cryptopians” about how Ethereum managers defended against hacker attacks during the ICO boom.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


