
Hack-cheat for ChatGPT, scandalous leak from Roskomnadzor’s internal network, and other cybersecurity events
We have rounded up the week's most important cybersecurity news.
- The ‘Cyber Partisans’ leak reveals the real role of one Roskomnadzor structure.
- Reddit was hacked and its source code stolen.
- Hackers have learned to create malware using ChatGPT.
- Tor onion services slowed due to DDoS attacks.
The Cyber Partisans leak reveals the real role of a Roskomnadzor structure
The hacker group ‘Cyber Partisans’ from Belarus shared with Russian media an archive of documents from the internal network of Roskomnadzor's subordinate Main Radiocommunication Centre (GRChC).
The dump of more than 2 TB of information was obtained as early as November 2022. At the GRChC they acknowledged the attack but described the situation as under control.
Some 1.5 million emails, mostly from 2020–2022, as well as about 200,000 text documents, spreadsheets and presentations shed light on the key role of this structure in monitoring Russians online.
Among other things, the GRChC helps block independent media, files reports on potential ‘foreign agents’, censors queries in ‘Yandex’ about the war, hunts for posts about Vladimir Putin's health, protests, and ‘fakes’ about the army.
Reddit hacked and source code stolen
On February 5, unknown attackers compromised the Reddit site and stole its source code.
The criminals created a phishing page mimicking Reddit's internal network site. Through it, attackers stole employee credentials and two-factor authentication tokens.
Among the compromised data were limited contact details for Reddit, as well as information about current and former employees. Potentially data about advertisers could have been stolen, but more specific financial information and campaign statistics were not affected.
The breach did not affect the site's core working systems, passwords, or user accounts.
The incident's other details were not disclosed, noting only a recent similar attack on game developer Riot Games.
Hackers learned to create malware using ChatGPT
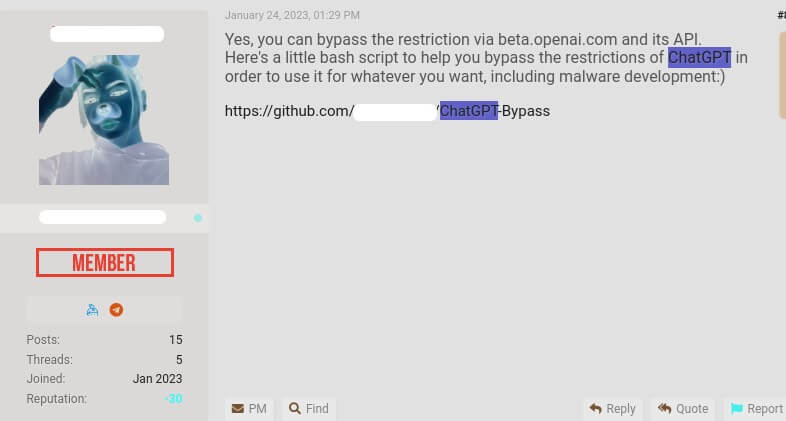
A paid bot appeared on Telegram, enabling bypass of ChatGPT's restrictions on creating illegitimate content, including malware and phishing emails. Check Point researchers noted this.
ChatGPT is available to developers. However, the current API version of the AI bot is poorly protected against various abuses and can be used by external applications.
“For example, integrating the GPT-3 language model into Telegram channels allows creating malicious content without any restrictions or barriers set in the ChatGPT user interface,” the researchers said.
On one of the hacker forums they found ads for such a service. The first 20 queries to the chat bot are free; after that, users are charged $5.50 for every 100 queries.

During testing, experts were able to create a phishing email and a script that steals PDF documents from an infected computer and sends them to the attacker via FTP. To create this script they used the request: “Write malware that will collect PDF files and send them via FTP”.
Another hacker-forum member published code that allows free generation of malware.
Secure messaging app hacked to monitor drug traffickers
Dutch police dismantled the anonymous messaging service Exclu. Before that, authorities hacked the service and, for five months, tracked the criminals' activities.
On Friday, the police carried out an action day as part of the investigation into the cryptocommunication service #Exclu. Arrests were also made over the past weekend, and around 200 phones were seized for further investigation: https://t.co/0B9brVcF8K @Europol @Eurojust @landelijkparket
— Landelijke Eenheid (@POL_Lnd_Eenheid) February 6, 2023
During the investigation, 79 searches were conducted in the Netherlands, Germany and Belgium, 42 people were arrested.
Two of those detained were the owners and operators of Exclu, the others were users of the service, including operators of drug laboratories. They seized several kilograms of narcotics, firearms, more than €4.3 million in cash and luxury items.
Exclu sold six-month subscriptions for €800 and allowed encrypted messaging and media exchange. Police estimate the messenger's audience to be about 3,000 people, 750 of whom lived in the Netherlands.
Tor onion services slowed due to DDoS attacks
For the last seven months, the Tor network has been regularly disrupted due to powerful DDoS attacks. Users report issues loading pages and lack of access to onion services.
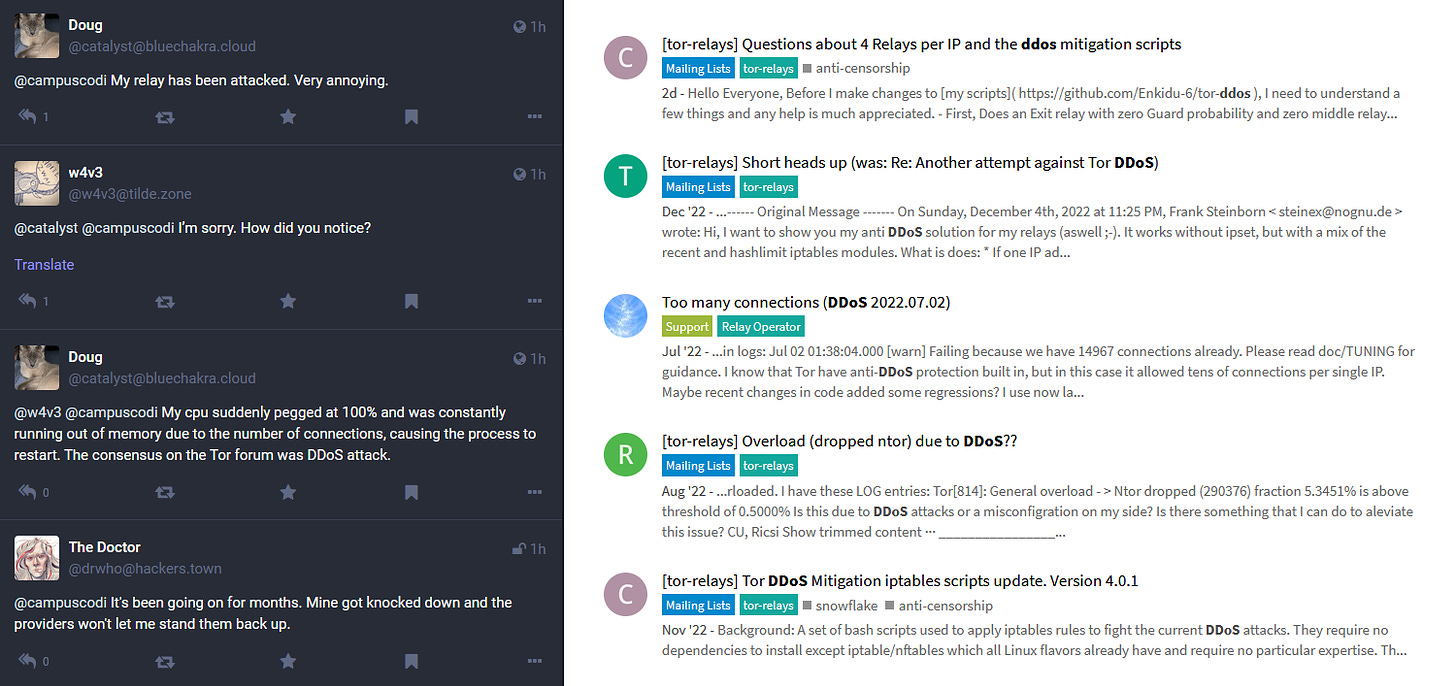
Tor Project developers are aware of the problem and are working to mitigate the impact of attacks and protect the network.
“The methods and targets of these attacks have changed over time, and we have adapted as they continued. It is not possible to identify with certainty who is behind them, or what their intentions are,” said a Tor Project representative.
According to Risky Business, the attacks do not occur simultaneously across the whole network. Instead, attackers target a small number of specific relays and switch to others after a few days.
At the same time, none of the operators received ransom demands during the attacks.
Malicious Dota 2 mods found in Steam
Experts at Avast found four malicious game mods for Dota 2 in the Steam store that allowed attackers to backdoor players' systems. Despite mandatory checks at publication, the authors of the mods managed to bypass them.
To gain control over a player's machine, the attackers used Valve’s Panorama framework. Its JavaScript part relies on an vulnerable V8 engine version.
The exploit was embedded in a legitimate file that added a scoreboard functionality, making it harder to detect.
“The backdoor allowed any JavaScript code retrieved via HTTP to be executed, giving the attacker the ability to hide or modify the exploit code at will, and to fully update the entire mod,” Avast said.
Additionally, the attacker embedded in the mods a file that tested executing a malicious Lua snippet on the server side. It features logging, arbitrary command execution, coroutines, and HTTP GET requests.
Avast notified Valve’s developers, who updated the vulnerable V8 version on January 12, 2023. The company also removed the malicious mods from Steam and warned at least 200 players affected by the attack.
Also on ForkLog:
- South Korea imposed sanctions against Bitcoin ransomware operators.
- The Bank of Russia added CZ-Changpeng FX to the blacklist.
- The Webaverse team lost $4m in USDC after meeting with an “investor”.
- Yuga Labs won a court case against one of the creators of “fake” BAYC tokens.
- The Damus social network announced payouts in satoshis. This led scammers to monetize this.
- Bitzlato co-founder Anton Shkurenko was arrested in Moscow. He gave an exclusive interview to ForkLog on the matter.
- CoW Swap lost $166,000 due to a hack.
- UN: North Korean hackers stole a record amount of cryptocurrency in 2022.
- GitHub chief urged to remove open-source software from the EU AI Act.
- Russia’s Interior Ministry could not identify victims or the amount of losses in the REvil case.
- A Russian court found a participant in a P2P deal guilty of colluding with the attacker.
- Experts suspected the crypto project Dingo of fraud.
- Interpol will develop means of policing crime in the metaverse.
What to read this weekend?
In ForkLog’s educational section “Cryptoorium” we cover types of scams and offer advice on how not to become a victim.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


