
Telegram user de-anonymisation, exposure of North Korean spies, and other cybersecurity developments
We’ve gathered the week’s most important cybersecurity news.
- Experts uncover APT43 hackers, engaged in espionage on behalf of North Korea.
- Media outlets reveal Rostec’s tool for de-anonymising Telegram users.
- GitHub removed a private repository containing Twitter’s source code after a DMCA notice.
- In Ukraine, authorities arrested a gang of phishers who stole $4.3 million from EU residents.
Experts uncover hackers APT43, engaged in espionage on behalf of North Korea
Analysts from Mandiant published a report on the North Korean hacking group APT43, which conducts espionage and cryptocurrency theft.
Mandiant Intelligence is pleased to bring you ??APT43, a prolific cyber operator that supports the interests of the North Korean regime. We believe APT43 funds itself through cybercrime to support its primary mission of collecting foreign intelligence.https://t.co/ArkVjlm6ZB
— Andrew Thompson (@ImposeCost) March 28, 2023
According to experts, the criminals are believed to be backed by North Korea’s General Reconnaissance Bureau, with the main targets including government and research institutions in the US, Europe, Japan and South Korea.
APT43 sends phishing emails impersonating fictitious officials, directing victims to controlled websites to harvest credentials. This enables the hackers to authenticate in target systems.
To steal funds, the group uses malicious Android applications targeted at cryptocurrency holders in China.
Stolen assets are laundered through mixers and cloud-mining services using fake aliases and addresses. For equipment and infrastructure, APT43 pays with PayPal, American Express and stolen Bitcoin.
GitHub removed the Twitter source code repository
GitHub removed the private repository of user FreeSpeechEnthusiast containing Twitter’s source code after a DMCA notice from the social network.
Sources cited by The New York Times say that the repository contained information about vulnerabilities in the security system that could allow hackers to exfiltrate user data or take Twitter offline.
The company is now seeking the court to compel GitHub to disclose identifying information about the culprit and those who gained access to it.
It is not known how long the source code remained on the network. Media reports say it was at least several months.
Trend Micro finds crypto-stealing malware OpcJacker
Trend Micro researchers discovered OpcJacker malware, which has been distributed since mid-2022 under the guise of cryptocurrency apps and other legitimate software on counterfeit sites.
OpcJacker features include keylogger, screenshots, theft of data from browsers, loading of additional modules and clipboard cryptocurrency address spoofing.
Upon infection, the malware replaces the legitimate DLL library inside the installed program with a malicious one. This enables it to load additional malicious payload — a modified Babadeda ransomware payload.
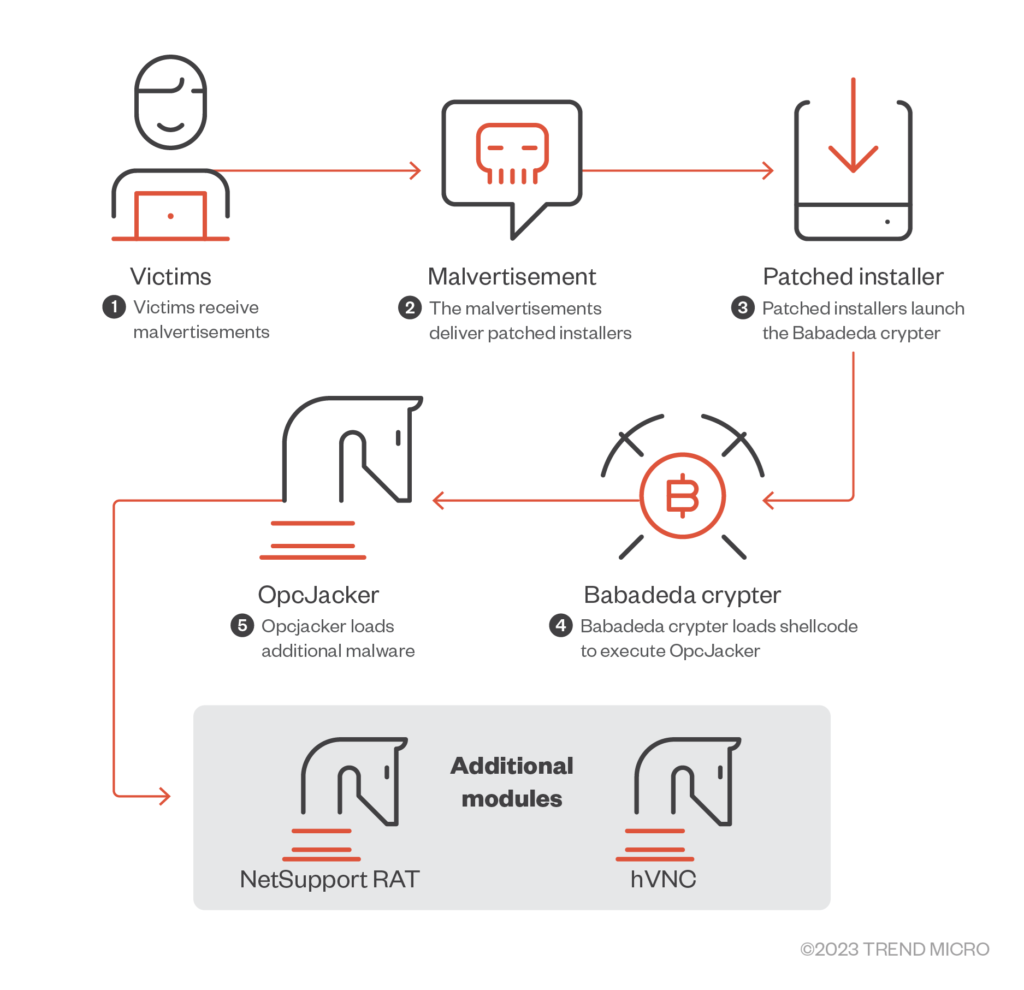
The malware’s primary objective remains unknown, but its ability to steal cryptocurrency points to a financial motivation, say experts.
Roskomnadzor opposes anonymous numbers based on blockchain
Roskomnadzor has proposed using equipment installed at providers under the sovereign internet law to restrict access to anonymity tools. The agency singled out services that use virtual phone numbers. This includes numbers on the Fragment blockchain platform, which can purchased for cryptocurrency for anonymous Telegram registration.
If the government passes the amendments, they would take effect on 1 March 2024.
Ukraine arrests phishing gang that stole $4.3 million from EU residents
The Ukrainian Cyber Police uncovered participants of an international criminal organisation who used phishing to steal banking card data.
The suspects created more than 100 phishing sites selling cheap goods targeting European users. All customer payment information automatically became known to criminals. They then wired funds from their accounts.
The group also set up call centres in Vinnytsia and Lviv, whose operators encouraged potential victims to make purchases.
Over 1,000 victims from the Czech Republic, Poland, France, Spain, Portugal and other EU countries have been recorded. The total damage exceeds 160 million hryvnias ($4.3 million).
During a series of searches, law enforcement seized mobile phones, SIM cards and computer equipment. A criminal case has been opened for fraud and the creation of a criminal group. The suspects face up to 12 years in prison with confiscation of property.
Two organizers have been arrested. Ten more participants have been detained in the EU. The investigation continues.
Media reveal Rostec tool for de-anonymising Telegram users
Rostec, the Russian state corporation, has purchased a platform that enables revealing the identities of anonymous Telegram users. The investigation by The Bell and Meduza says.
Since 2022, Rostec has been fighting a war on two fronts. As well as supplying hardware to the front, it is also eliminating criticism of its chief, Sergei Chemezov, a friend of Vladimir Putin, from Telegram channels. The Bell and Meduza found out more – a thread ?1/13
— The Bell (@thebell_io) March 28, 2023
According to them, the software suite named “Hunter” analyses more than 700 public data sources, including social networks, blogs, forums, messaging apps, classifieds, cryptocurrency blockchains, the dark web and state automated services.
The data allow names, nicknames, email addresses, phone numbers, crypto wallets and IP addresses to be linked and eventually identify Telegram channel administrators.
Journalists believe Rostec’s primary targets are authors critical of Russia’s state policy.
Public organisation Roskomsvoboda notes that using only data points cannot de-anonymise the channel owner. They suggest Rostec may also exploit a zero-day vulnerability in the platform or work with an insider inside Telegram.
A Telegram spokesperson told Bleeping Computer that the most common methods for de-anonymising channel administrators are accepting payments for advertising, granting access to third-party bots, or using unofficial Telegram apps.
Rostec plans to sell “Hunter” in 2023 to all Russian Interior Ministry administrations and the FSB’s operational-technical divisions.
Also on ForkLog:
- Ormenus Coin will pay $102 million in a suit by the SEC.
- The court found participants of the bZx DAO responsible for the breach of the protocol.
- The SEC brought charges against the Beaxy crypto exchange and its executives.
- Hackers stole bitcoins in 52 countries via a fake Tor browser.
- The client database of the Tetchange exchange was put up for sale for $1,000.
- DEX SafeMoon lost $9 million in a breach.
- HAPI Labs: nearly 96% of donations to the Russian army went through Binance.
- Sam Bankman-Fried was granted new terms of release on bail. He was also charged with bribing a Chinese official.
- The THORChain network paused operations due to a vulnerability.
- An analyst estimated the number of irrecoverably lost bitcoins.
- CFTC filed a lawsuit against Binance and Changpeng Zhao.
- Verichains warned about wallet vulnerabilities with multisig.
- A former Coinone employee was arrested in a bribery case.
- An American was sentenced to four years in prison for ICO fraud involving $21 million.
- In Canada, extortionists abducted the bankrupt “crypto king”.
- A glitch in ChatGPT exposed subscribers’ payment information.
- Do Kwon will appeal the decision to extend detention in Montenegro.
- The Kokomo Finance team suspected of an exit scam of $4 million.
- The hacker who breached Euler Finance returned more than $100 million in Ethereum, and later another $50.5 million in ETH and DAI.
What to read this weekend?
Together with HAPI Labs experts, we examine how “dirty” cryptocurrency becomes “clean” and how AML services should label it going forward.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


